This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage
Info:
All log tables in Azure Monitor Logs must have a TimeGenerated column populated with the timestamp of the logged event.
Var1 - Azure CLI:

Choose the bash mode.
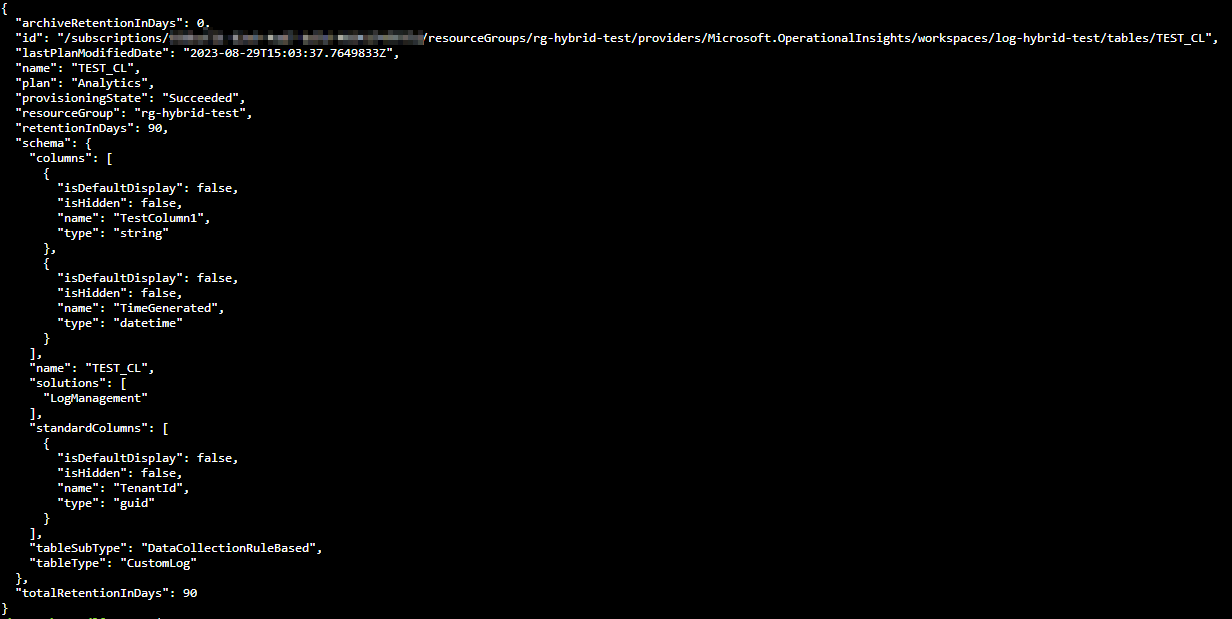
az monitor log-analytics workspace table create --resource-group <Resource Group Name> --workspace-name <Workspace Name> -n <Tabel Name> --retention-time <Numer of Days> --columns <Column Name>=<Columntype> (e.g. Column1=string TimeGenerated=datetime) 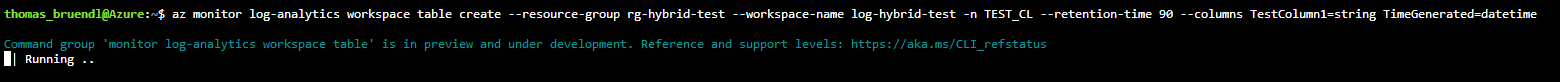
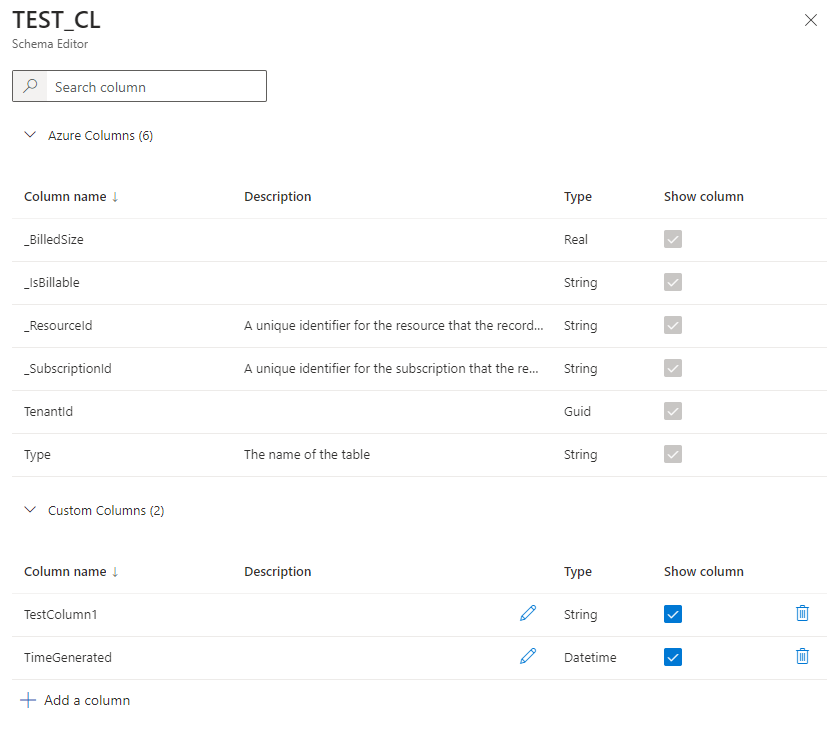
Var2 - PowerShell:

Choose the PowerShell mode.
$tableParams = @'
{
"properties": {
"schema": {
"name": "TEST2_CL",
"columns": [
{
"name": "TimeGenerated",
"type": "DateTime"
},
{
"name": "TestColumn2",
"type": "String"
}
]
}
}
}
'@
Invoke-AzRestMethod -Path "/subscriptions/{subscription}/resourcegroups/{resourcegroup}/providers/microsoft.operationalinsights/workspaces/{workspace}/tables/MyTable_CL?api-version=2021-12-01-preview" -Method PUT -payload $tableParams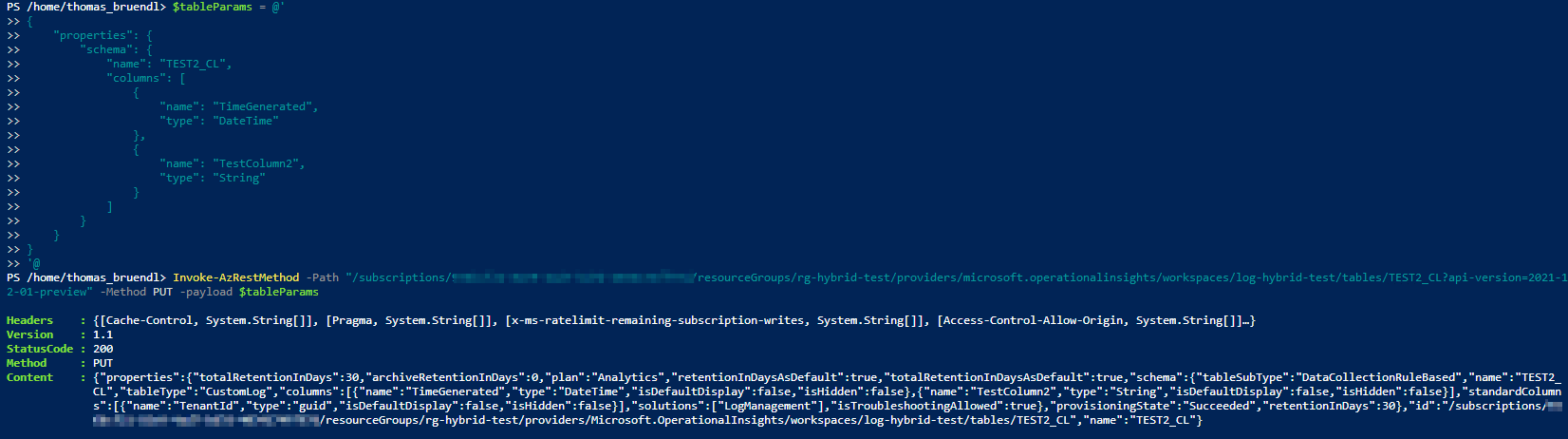


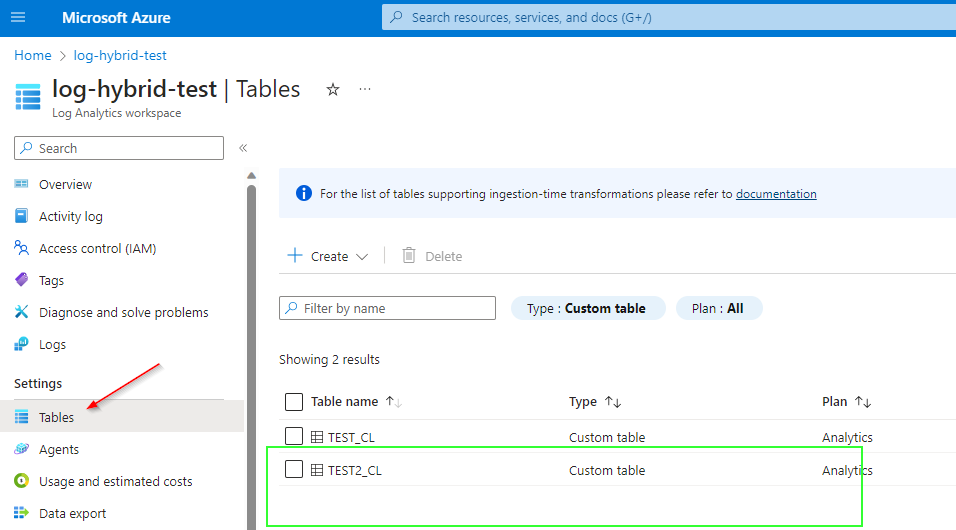
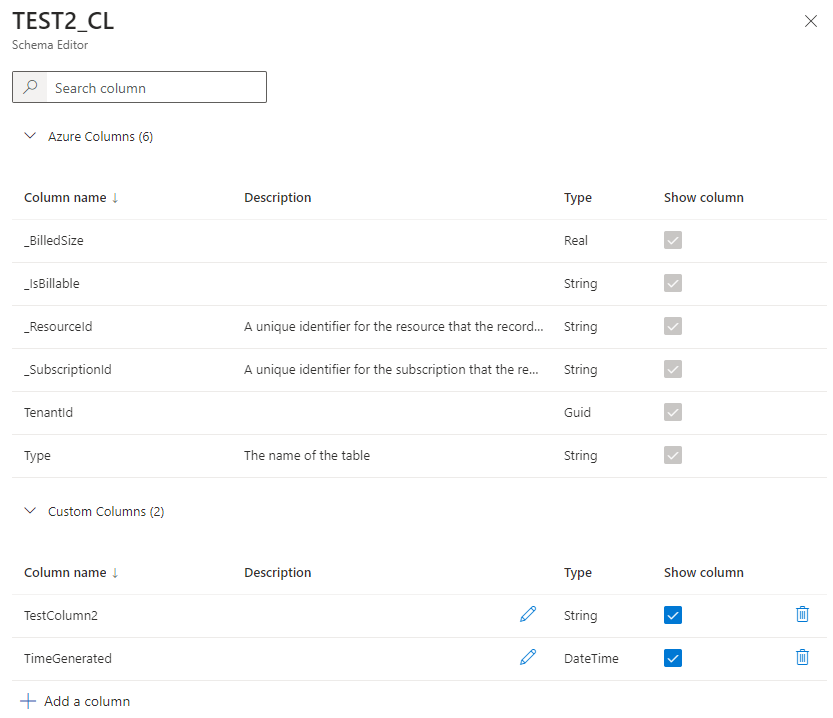
Var3 - Azure Portal:
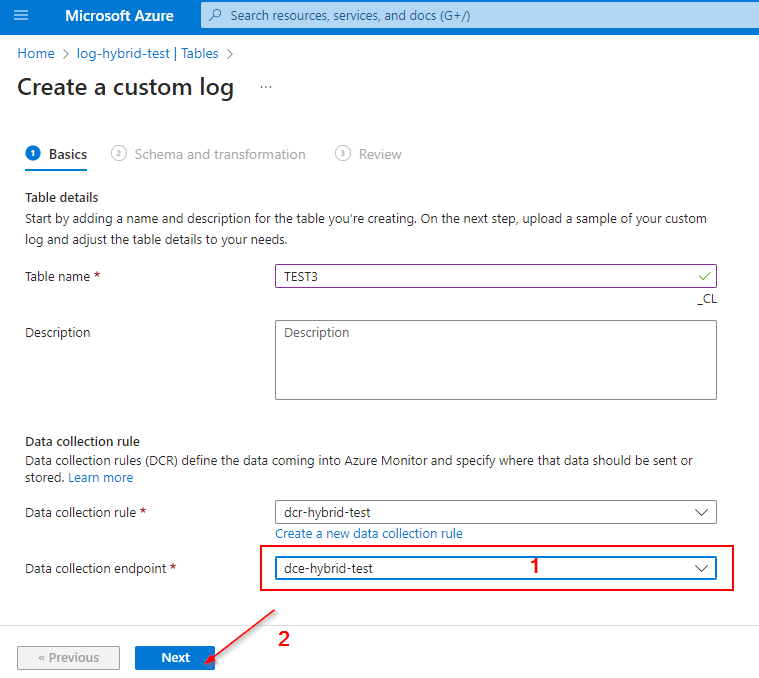
Data Collection Endpoint:
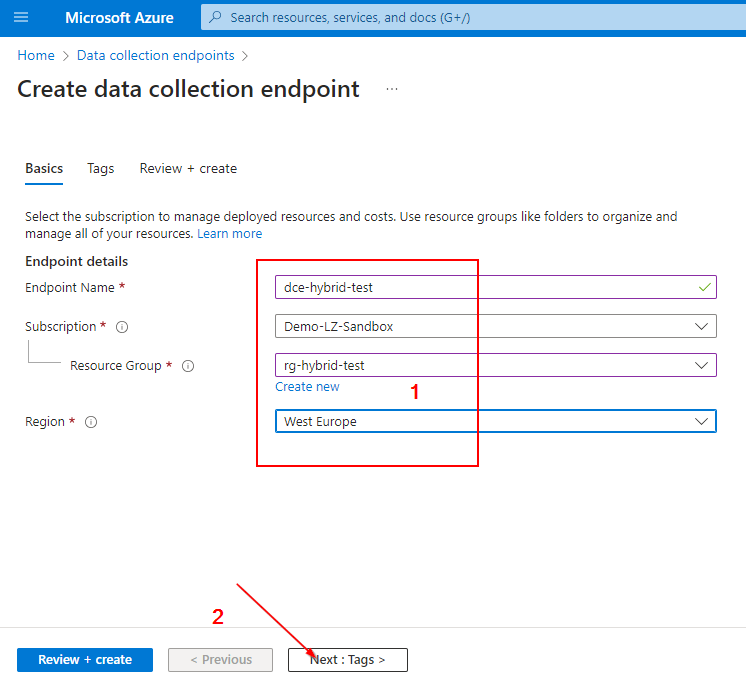
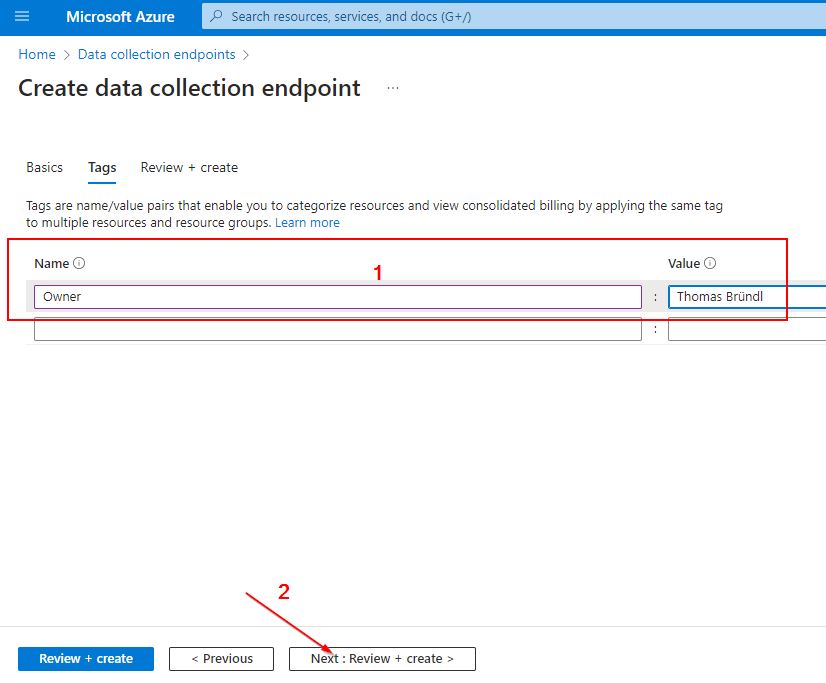
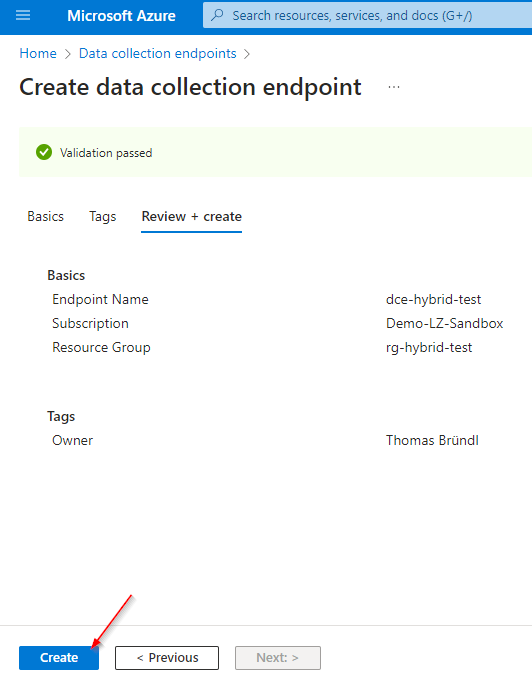
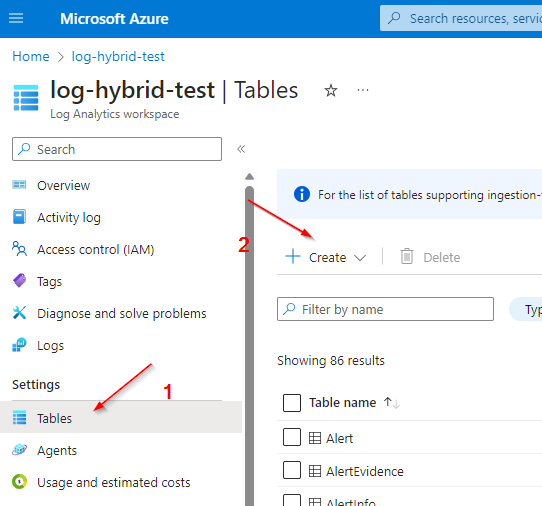
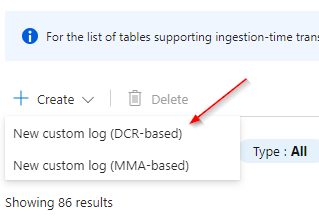
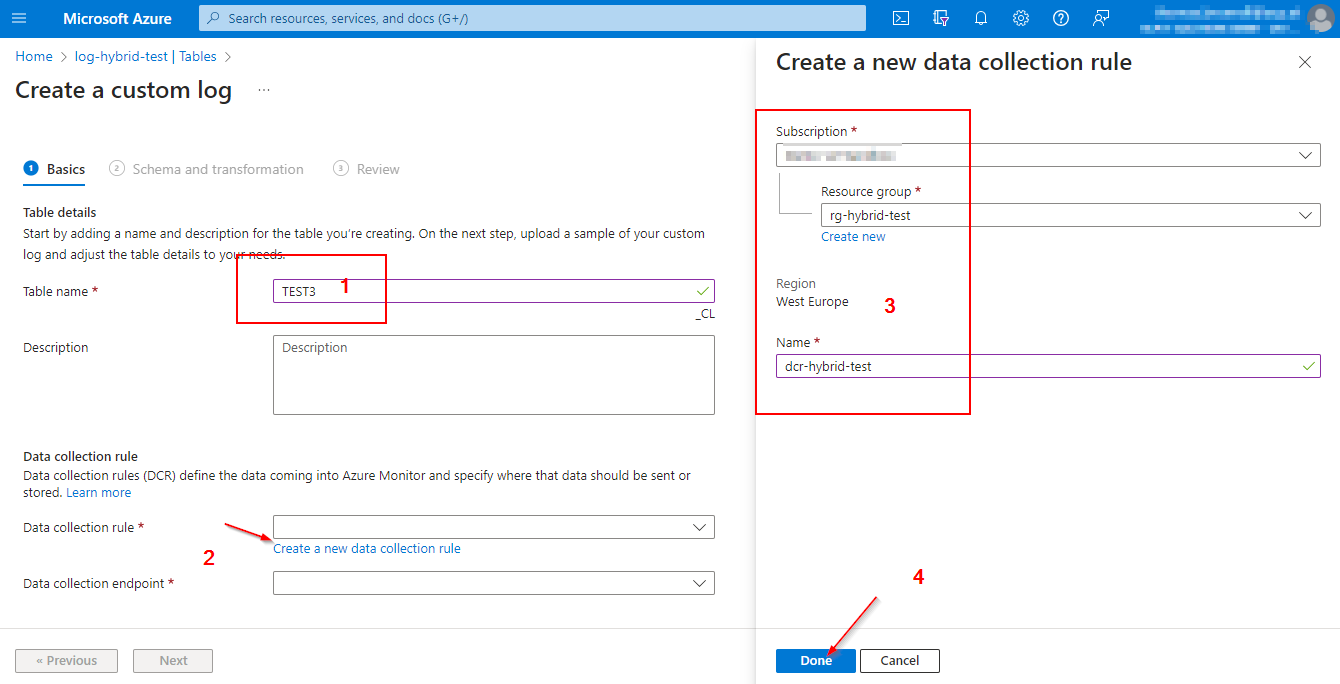
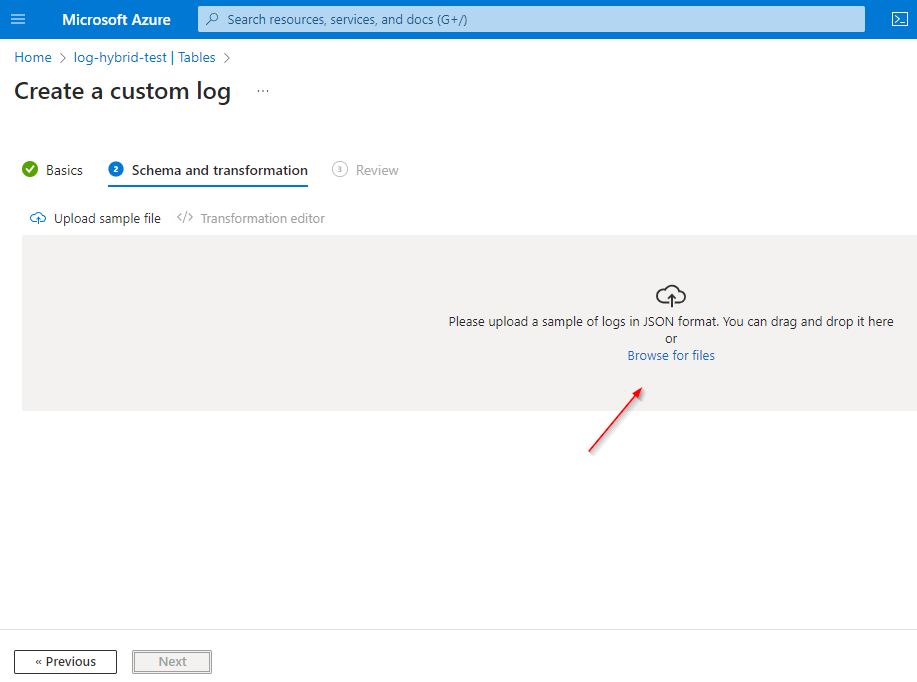
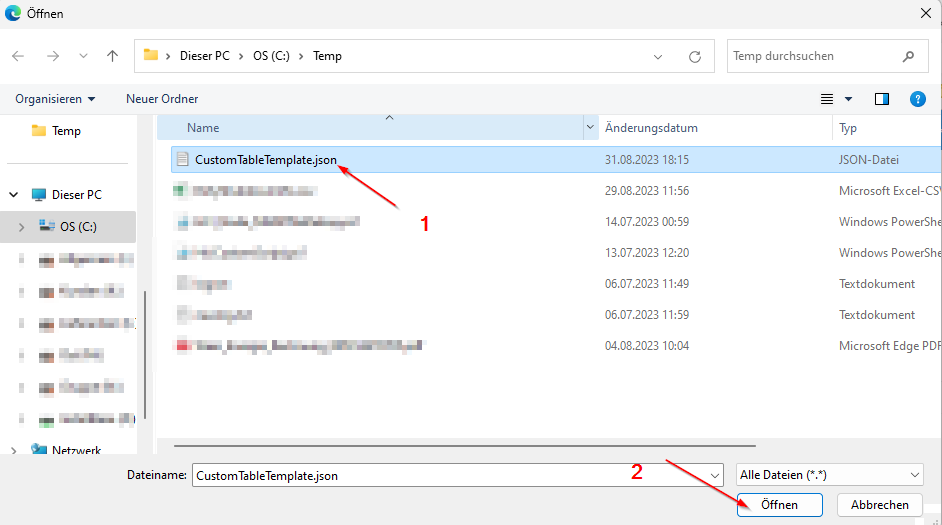
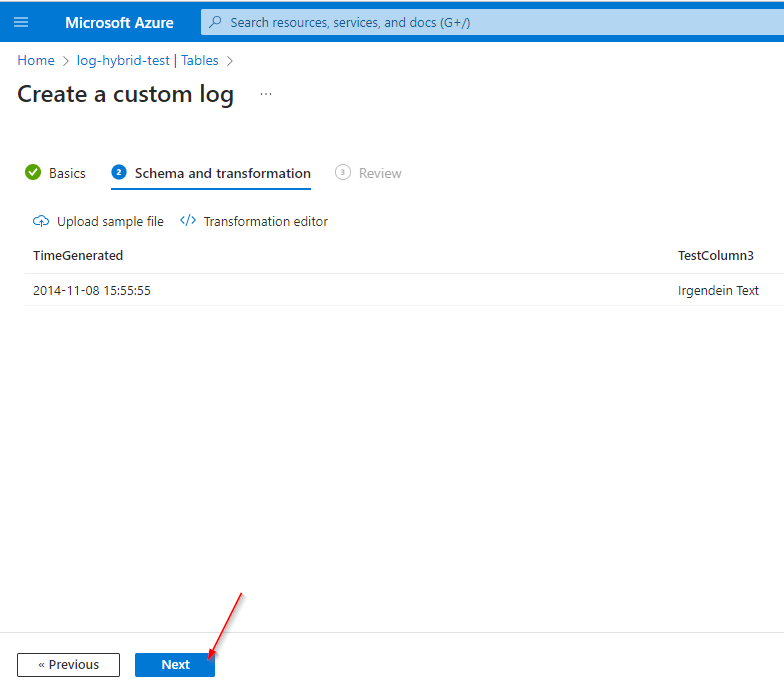
Custom Log Table:


[
{
"TimeGenerated": "2014-11-08 15:55:55",
"TestColumn3": "Irgendein Text"
}
]
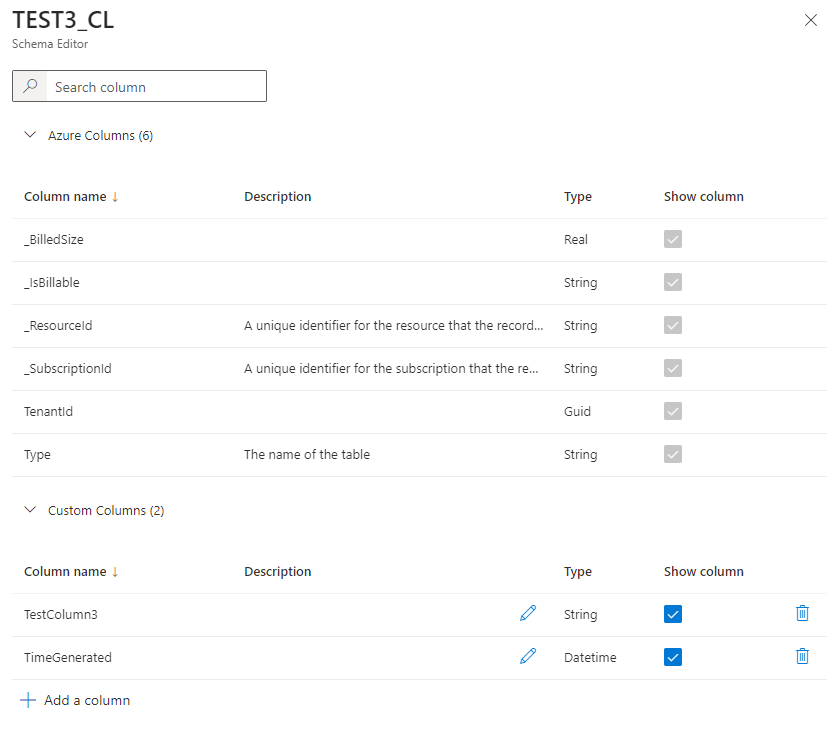
Additional helpful material:
Often you need a table, which matches the SYSLOG - table schematically.
Here you can find a script, with which you can create the table automatically.
$tableParams = @'
{
"properties": {
"schema": {
"name": "Syslog_CL",
"columns": [
{
"name": "MG",
"type": "guid",
"isHidden": true
},
{
"name": "SeverityLevel",
"type": "string",
"description": "Severity level of the event."
},
{
"name": "ProcessID",
"type": "int",
"description": "ID of the process that generated the message."
},
{
"name": "ProcessName",
"type": "string",
"description": "Name of the process that generated the message."
},
{
"name": "ManagementGroupName",
"type": "string"
},
{
"name": "HostName",
"type": "string",
"description": "Name of the system sending the message."
},
{
"name": "HostIP",
"type": "string",
"description": "IP address of the system sending the message."
},
{
"name": "SourceSystem",
"type": "string",
"description": "Type of agent the data was collected from. For syslog the value is typically Linux."
},
{
"name": "SyslogMessage",
"type": "string",
"description": "Text of the message."
},
{
"name": "TimeGenerated",
"type": "datetime",
"description": "Date and time the record was created."
},
{
"name": "TimeCollected",
"type": "datetime",
"isHidden": true
},
{
"name": "Computer",
"type": "string",
"description": "Computer that the event was collected from."
},
{
"name": "CollectorHostName",
"type": "string",
"description": "Name of the remote device that generated the message."
},
{
"name": "EventTime",
"type": "datetime",
"description": "Date and time that the event was generated."
},
{
"name": "Facility",
"type": "string",
"description": "The part of the system that generated the message."
}
]
}
}
}
'@
Invoke-AzRestMethod -Path "/subscriptions/{subscription}/resourcegroups/{resourcegroup}/providers/microsoft.operationalinsights/workspaces/{workspace}/tables/Syslog_CL?api-version=2021-12-01-preview" -Method PUT -payload $tableParams
More tables - templates, can be found here:
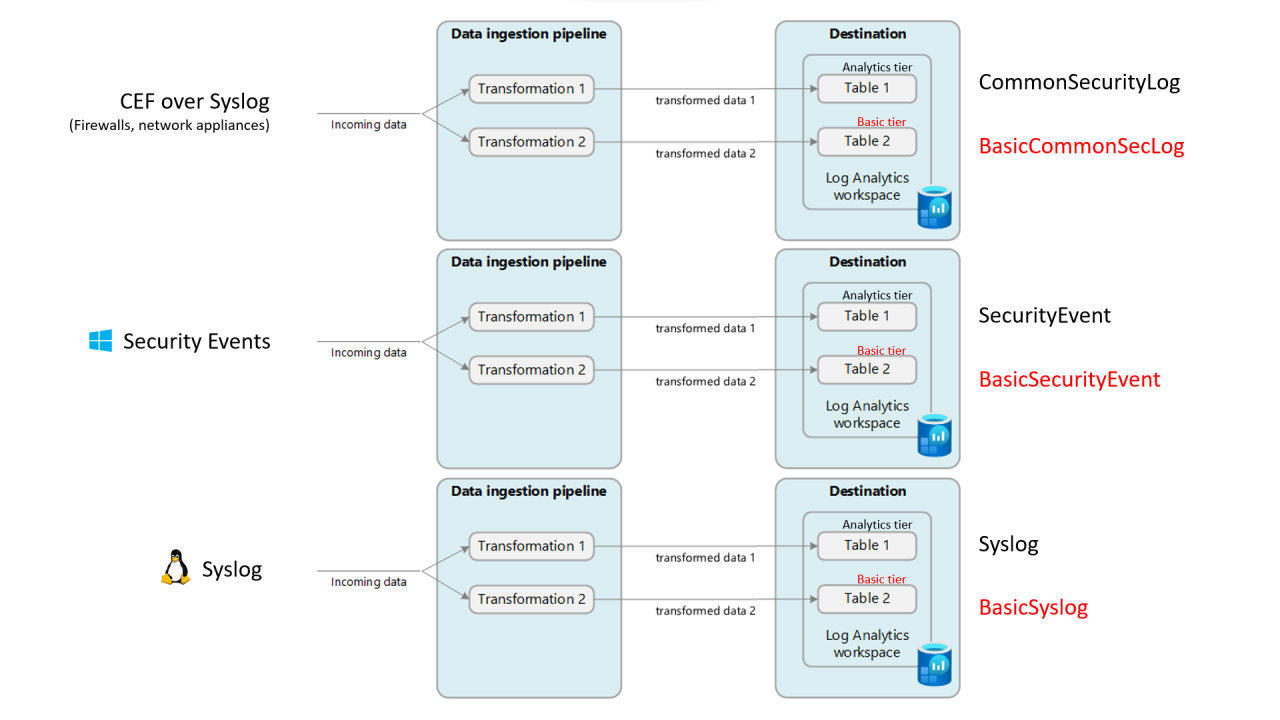
- CommonSecurityLog to BasicCommonSecLog
- SecurityEvent to BasicSecurityEvent
- Syslog to BasicSyslog
- Event to BasicEvent
References:
Add or delete tables and columns in Azure Monitor Logs - Azure Monitor
Create a table with a custom schema to collect logs from any data source.

Manage tables in a Log Analytics workspace - Azure Monitor
Learn how to manage table settings in a Log Analytics workspace based on your data analysis and cost management needs.

https://learn.microsoft.com/en-us/azure/azure-monitor/reference/tables/syslog#columns
Introducing a generic way to ingest DCR-based logs into Sentinel custom/basic table
(This is a continuation from previous article: Filter & Split Firewall/CEF logs into multiple Sentinel tables (analytics/basic tier) to save in ingestion costs) The most typical log tables in Sentinel are: CommonSecurityLog (Firewalls, network appliances using CEF over Syslog) SecurityEvent (Windows