Introduction:
Automation is one of the most important things to push at your employer these days, especially if you work in IT. It frees up resources that are always limited and removes boring repetitive tasks. Of course, some security aspects must also be taken into account here, and automation only makes sense if it is done properly.
In a Windows environment, MSAs (Managed Service Accounts) should therefore always be used for this purpose, as insecure password handling can then be completely ruled out.
In this tutorial you truly start from scratch. This means that you do not have an MSA in use in your company yet. You will learn which prerequisites have to be fulfilled and how to prepare your environment for the use of an MSA. Afterwards, you will learn how to create and manage an MSA using different approaches.
Prerequisites
- Active Directory Forest Functional Level - Windows Server 2008 R2 (needed for automatic passwords and SPN management)
- Host services using MSAs on Windows Server 2008 R2 and Windows 7 computers (MSAs cannot be installed on down-level operating systems)
- PowerShell, AD PowerShell (part of the RSAT), and the .Net 3.5x framework enabled on any computers using or configuring MSAs
Setup
- KDS Root Key - Creation
- MSA creation and assignment (via PowerShell)
- MSA creation and assignment (via GUI)
- MSA - Installation
1.KDS Root Key - Creation:
The first step is to create a KDS root key. The root key has to be created once per forest and is used by the Key Distribution Service on the domain controllers.
Below you will find the PowerShell commands that need to be executed against one of the domain controllers.
# How to create a KDS Root Key (with 12h delay -> in order to complete the domain controller replication).
Add-KdsRootKey -EffectiveImmediately
# How to create a KDS Root Key immediately (e.g. in (test) environments consisting of only one DC)
Add-KdsRootKey -EffectiveTime ((Get-Date).AddHours(-10))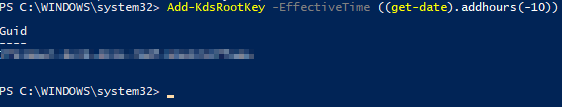
Required security settings
Since Managed Service Accounts (MSAs) only work with Kerberos Encryption AES128 and higher, the supported encryption types must be configured.
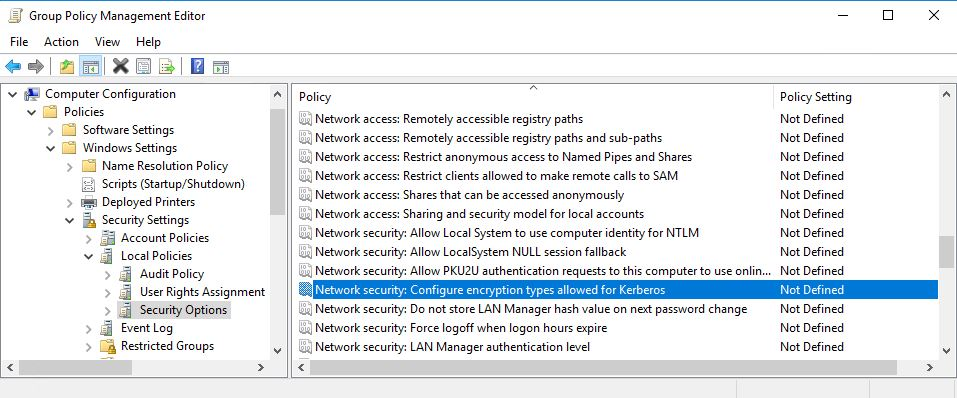
All activated and supported encryption types have to be configured via the following GPO settings:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > Network Security: Configure encryption types allowed for Kerberos.
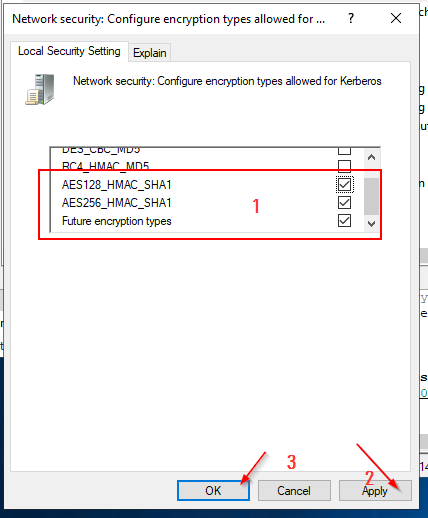
All values must be set to "Disabled" except for the following:
- AES128_HMAC_SHA1
- AES256_HMAC_SHA1
- Future encryption types
2. MSA - Creation (via PowerShell)
#Start a PowerShell and import the AD module
Import-Module ActiveDirectory
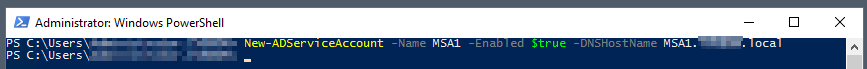
# Create an MSA
New-AdServiceAccount -Name "<MSA>" -DNSHostName "<MSA.FQDN>" -Enabled $true
2.1 MSA - Computer Assignment (via PowerShell)
# Associate the new MSA with a target computer in Active Directory
Add-ADComputerServiceAccount -Identity <Host> -ServiceAccount <MSA>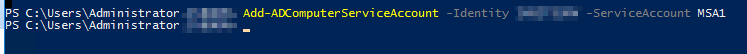
3. MSA - Creation (via GUI)
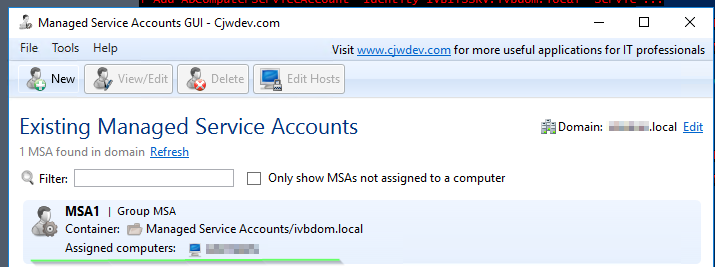
Managed Service Accounts GUI:
Download Link: ManagedSvcAccountsGUIInstaller.zip
3.1 Installation
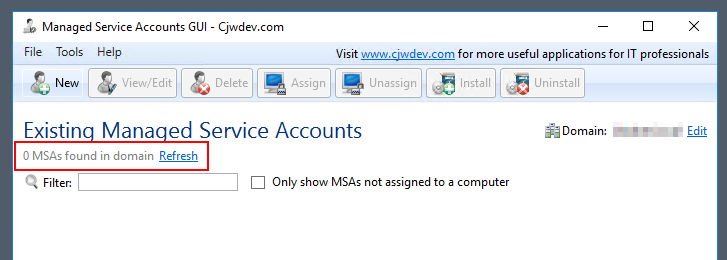
3.2 MSA - Creation (via GUI)
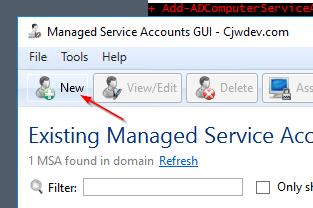
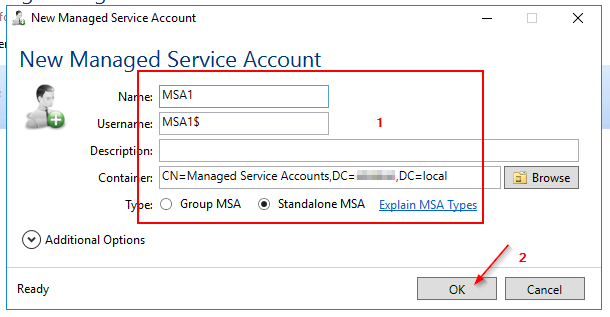
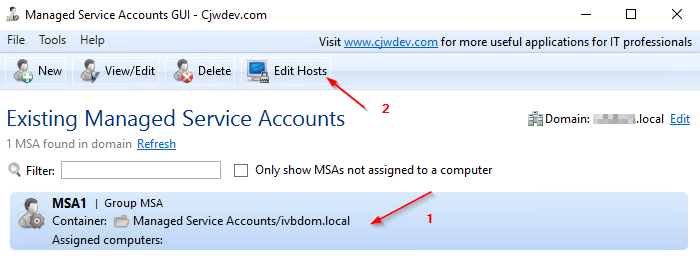
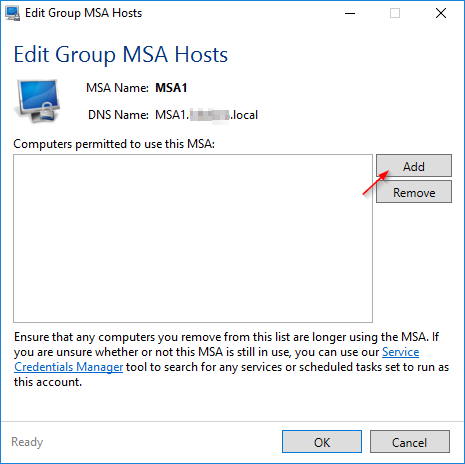
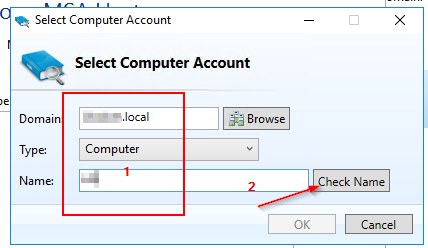
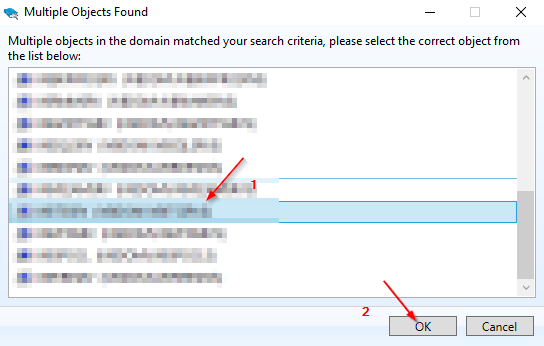
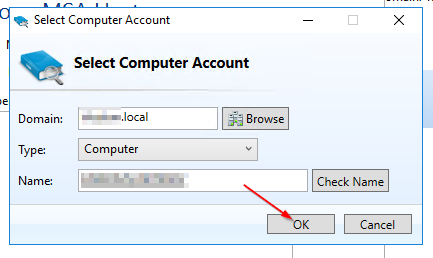
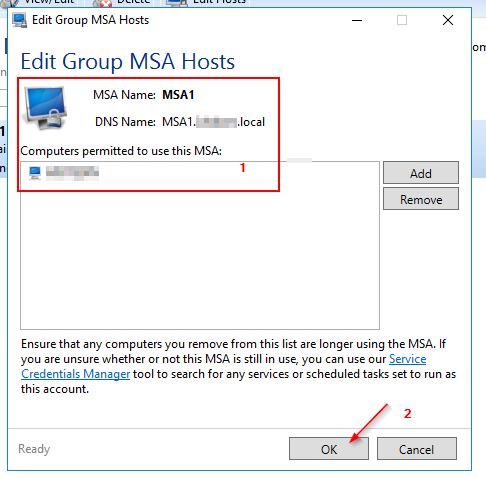

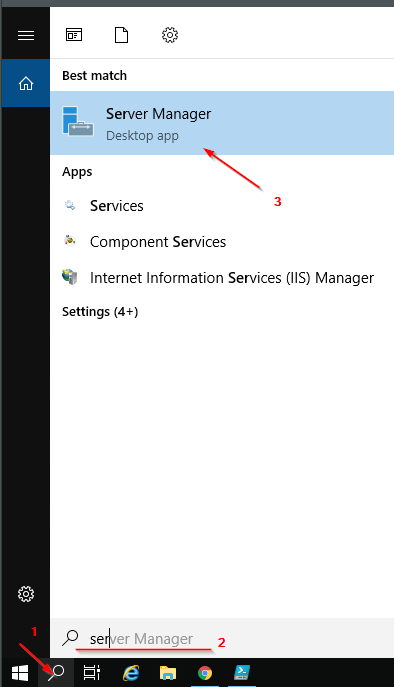
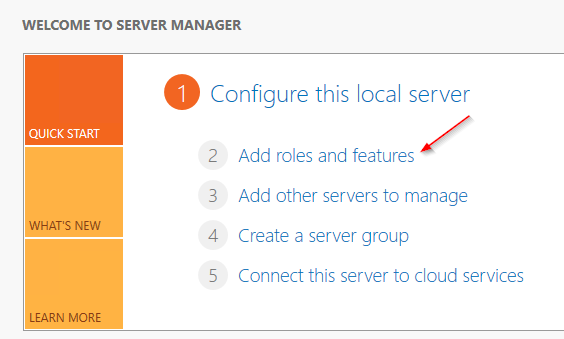
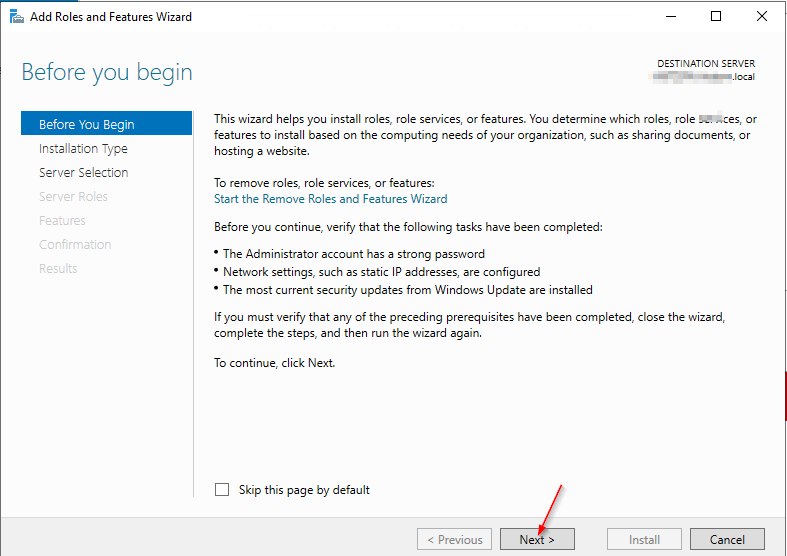
4.1 Installing the Active Directory Module for Windows PowerShell
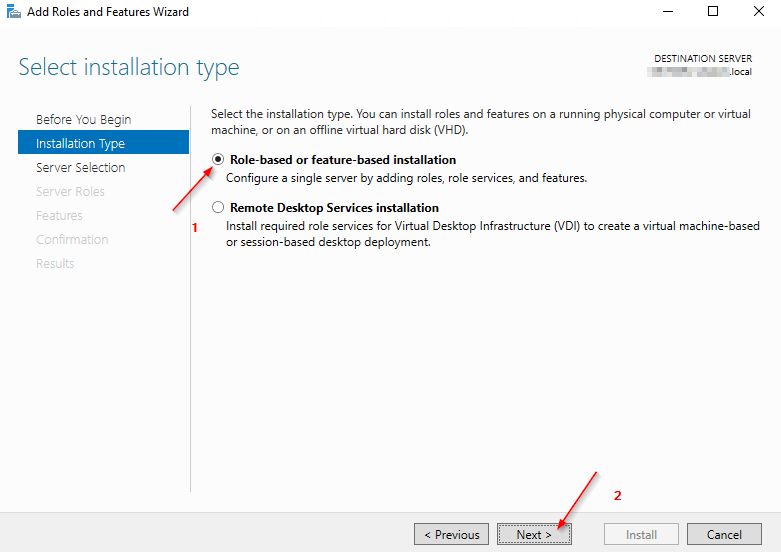
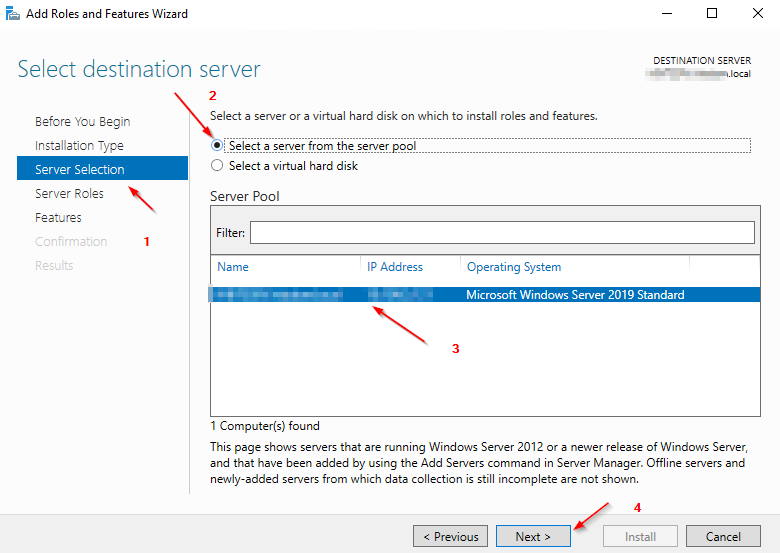
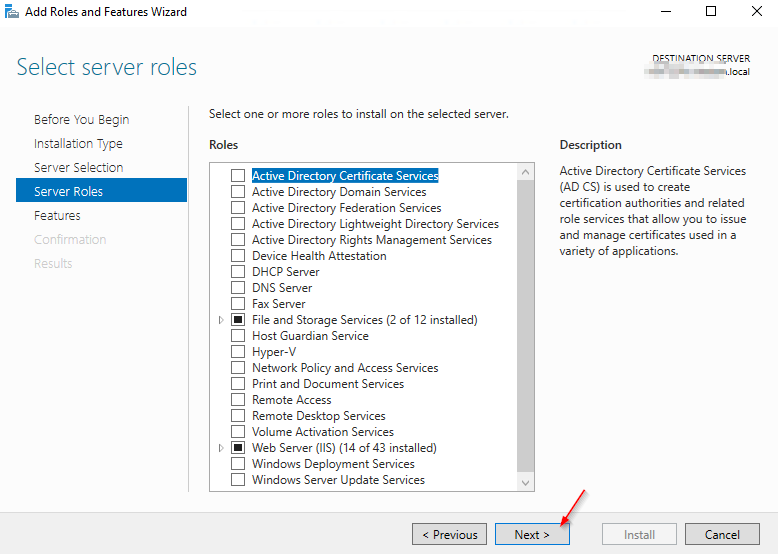
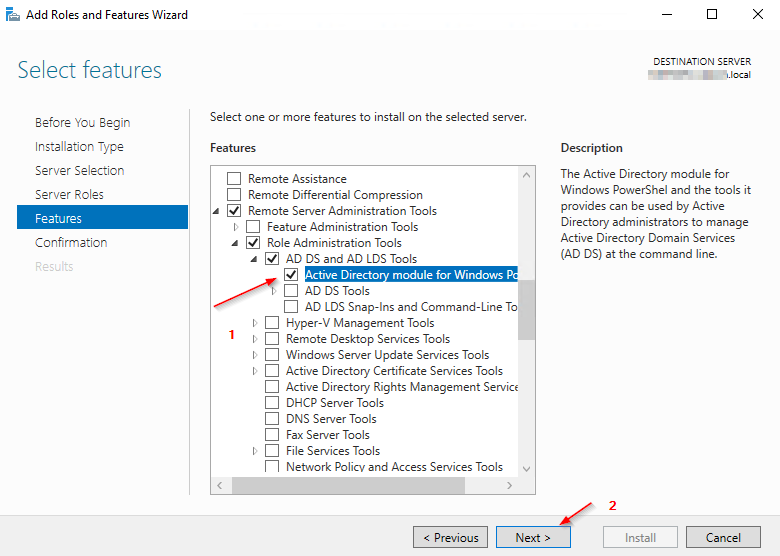
4.2 MSA - Installation
Install-ADServiceAccount -Identity MSA1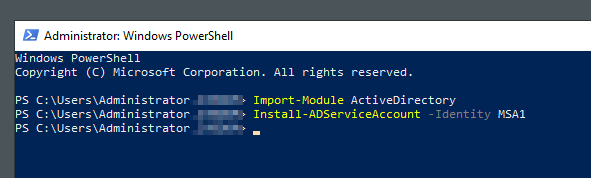
Get-ADServiceAccount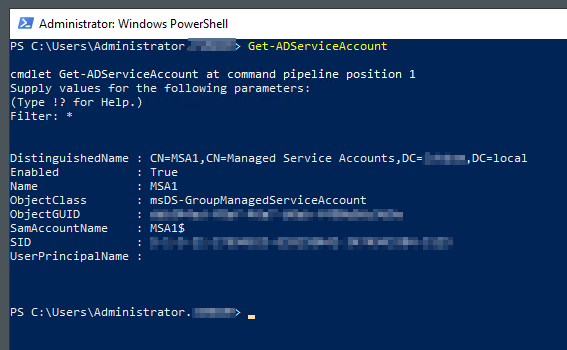
Sources:


Group Managed Service Accounts
