
This article has not been completed yet. However, it may already contain helpful information and therefore it has been published at this stage.
https://it-infrastructure.solutions/how-to-set-up-ubuntu-20-04-1-desktop-amd64-in-a-virtualbox/
Rsyslog is the default syslogd on Debian systems and is usually installed on Ubuntu 20.04 by default.
You can verify this by checking the version of installed rsyslog.
# Getting root - Access
sudo su
# Looking for an installed Application
apt list -a rsyslog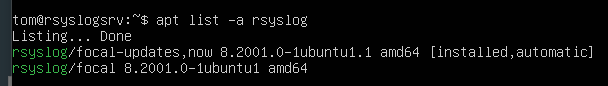
If for any reasons it is not installed, run the command below to install it.
# repo update
apt update
# installing rsyslog
apt install rsyslog -y
# start and enable the rsyslog service
systemctl enable --now rsyslogSetup Rsyslog Server on Ubuntu 20.04
Now that rsyslog is installed and running, you need to configure it to run in server mode. As stated above, rsyslog can be configured as client to sent logs to a central logging server or a server to receive and store logs from other systems.
Open the ryslog configuration file for editing;
nano /etc/rsyslog.confDefine Rsyslog Server Protocol and Port
Note that TCP syslog reception is way more reliable than UDP syslog and still pretty fast. The main reason is, that UDP might suffer of message loss. This happens when the syslog server must receive large bursts of messages. If the system buffer for UDP is full, all other messages will be dropped. With TCP, this will not happen. But sometimes it might be good to have a UDP server configured as well. That is, because some devices (like routers) are not able to send TCP syslog by design. In that case, you would need both syslog server types to have everything covered.
# provides UDP syslog reception
module(load="imudp")
input(type="imudp" port="514")
# provides TCP syslog reception
module(load="imtcp")
input(type="imtcp" port="514")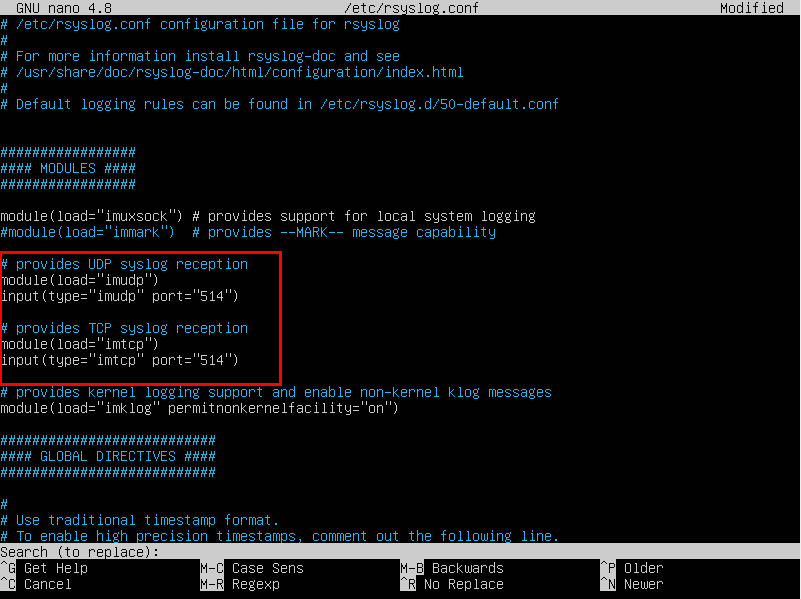
- CTRL + X
- Y
- Enter
TCP syslog may need to use a different port because often the RPC service is using this port as well.
# Restarting rsyslog - service
systemctl restart rsyslog
# Checking Listeners
ss -4altunp | grep 514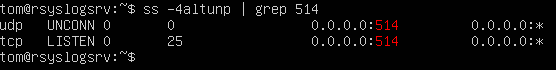
# Checking firewall
ufw status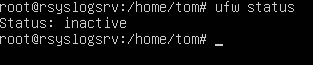
# Open firewall
ufw allow 514/udp
ufw allow 514/tcpNAT - Netzwerk
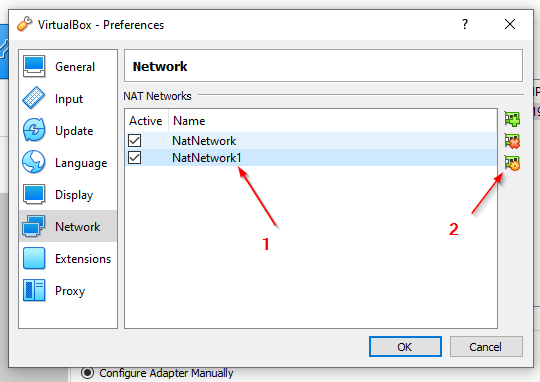
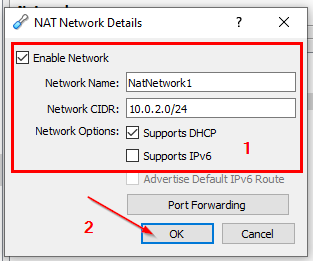
# Shutting down VMs
shutdown -h now
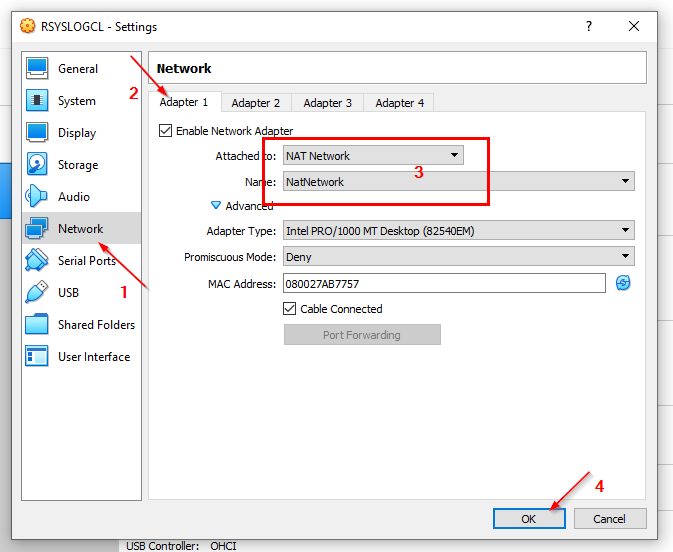
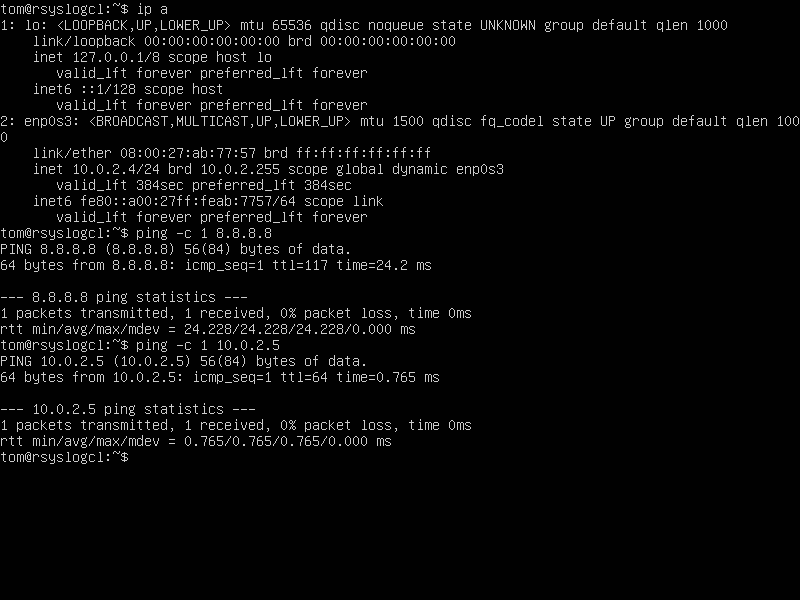
ip addrConnection Test
# Showing IP configuration
ip a
# Testingt Internet
ping -c 1 8.8.8.8
# Testing Connection between VMs
ping -c 1 10.0.2.X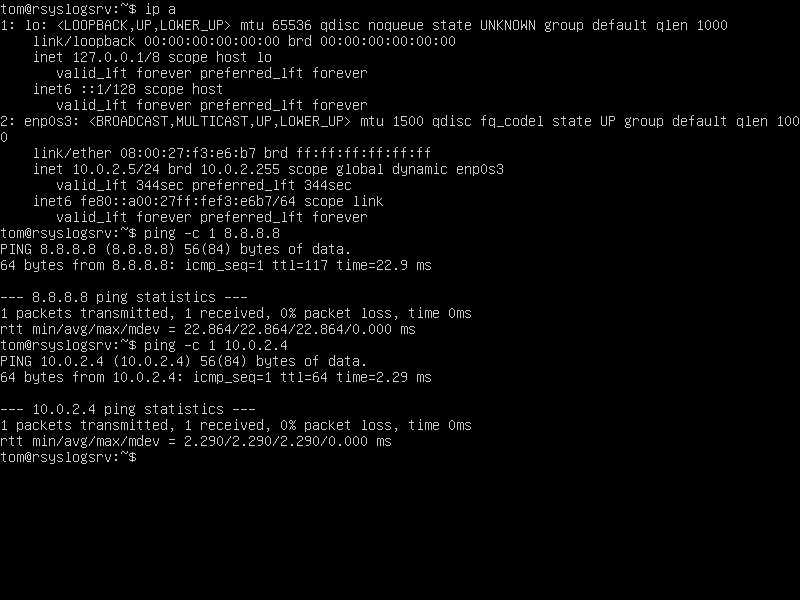
You may also want to explicitly set the remote clients that are allowed to to send syslog messages to rsyslogd.
nano /etc/rsyslog.conf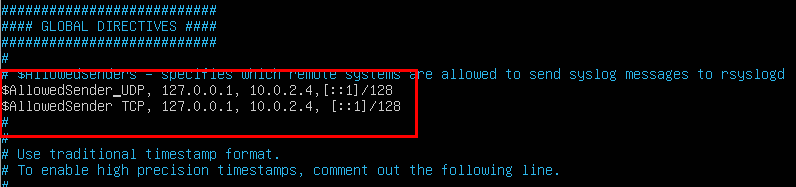
# Defining Allowed Traffic
$AllowedSender UDP, 127.0.0.1, 10.0.2.4, [::1]/128
$AllowedSender TCP, 127.0.0.1, 10.0.2.4, [::1]/128- CTRL + X
- Y
- Enter
# Open Firewall for a specific IP
ufw allow from 10.0.2.4 to any port 514 proto udp
ufw allow from 10.0.2.4 to any port 514 proto tcpConfigure Rsyslog Template
To create a template use the following syntax in /etc/rsyslog.conf:
# How to create a Template
$template TEMPLATE_NAME,"text %PROPERTY% more text", [OPTION]#Custom template to generate the log filename dynamically based on the client's IP address.
$template RemInputLogs, "/var/log/remotelogs/%FROMHOST-IP%/%PROGRAMNAME%.log"
*.* ?RemInputLogs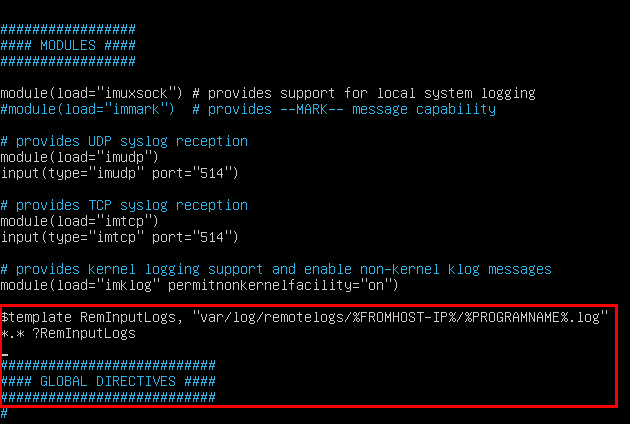
- CTRL + X
- Y
- Enter
# Config Check
rsyslogd -f /etc/rsyslog.conf -N1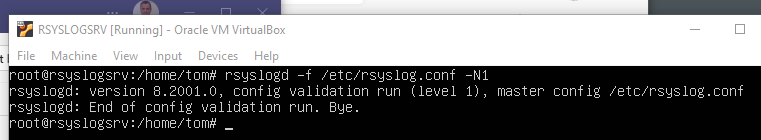
Restart rsyslog - Service (compare already described procedure)
systemctl restart rsyslog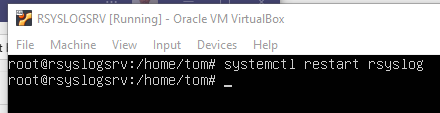
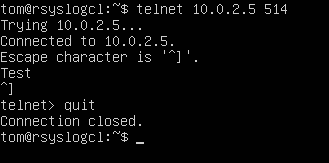
@RSYSLOG Client - VM :
# Send a test message
telnet 10.0.2.5 514- Test
- CTRL + C
- quit
@RSYSLOG Server - VM (RSYSLOGSRV):
# Check for new messages
cd /var/log/remotelogs/10.0.2.4
ls
cat Test#015.log
# Continious Inspection
tail -f /var/log/remotelogs/10.0.2.4/Test#015.log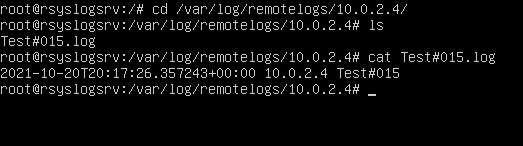

What else should be considered now? If you collect log files, you must also make sure that they are disposed of after some time, if they have lost their usability.
I have dealt with this topic in this further blog:
References:
Setup Rsyslog Server on Ubuntu 20.04

