
❕This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage
KQL OPERATOR: SEARCH
Description:
The search operator in Kusto Query Language (KQL) allows you to search for a specific text or value across the entire database or within specific tables. For a security analyst working with Microsoft Defender for Endpoint (MDE), this operator is particularly useful for quickly finding relevant information about a specific indicator or threat.
Syntax
[T |] search [kind= CaseSensitivity ] [in (TableSources)] SearchPredicateUse-Cases (leveraging the DeviceNetworkEvents Table):
#1 Basic usage:
This command 👇 searches for the value "192.168.1.1" in all tables and returns all related events.
search "192.168.1.1"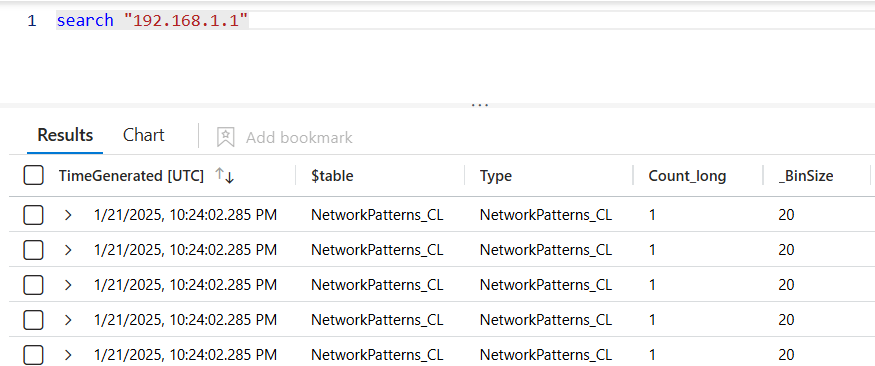
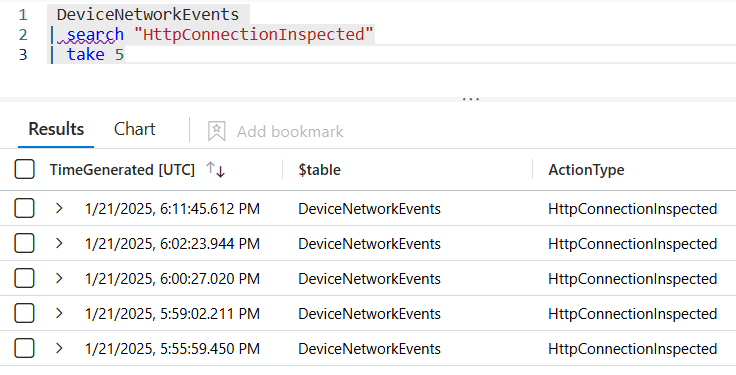
#2 Search for specific action types:
With this 👇, the analyst receives all network events where the action was 'HttpConnectionInspected'.
DeviceNetworkEvents
| search "HttpConnectionInspected"
| take 5✏️ Note: If you want to learn more about the take operator, follow this link to a previously created blog post.
WHEN TO USE IT:
- to quickly find relevant information about a specific indicator or threat.
- in combination with other operators, to define specific search criteria.
THINGS TO KEEP IN MIND
- The
searchoperator scans the entire database or table, which can lead to performance issues with large amounts of data. - It is important to narrow down the search scope as much as possible to increase efficiency.
References:





