
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Prerequisites:
- Some linux based environment
Links that might be useful in this case:
Anyone who has been using the Windows Admin Center for longer than 60 days will probably run into a certificate problem. The latest browser from Microsft, called Edge, will then no longer allow access to the WAC portal at all.
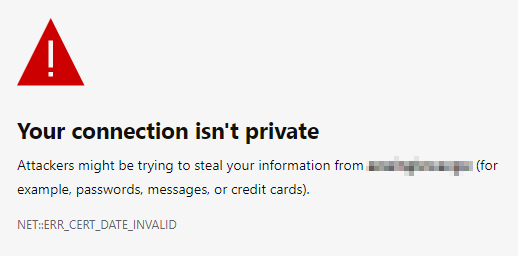
1) Scenario 1 - Local WAC Installation
The easiest way to get a new certificate is to initiate a repair installation. Enclosed are the necessary steps, if you have a local WAC - installation.
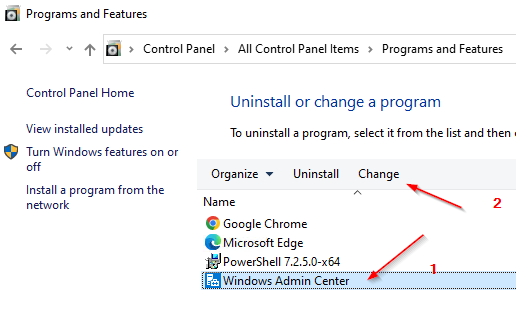
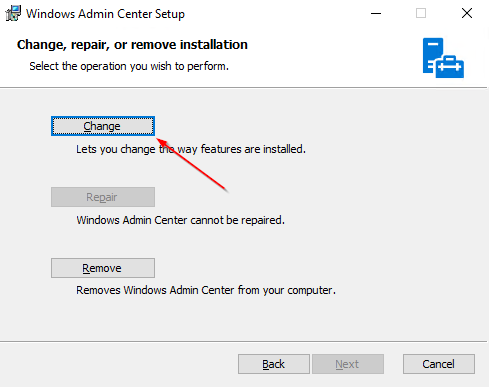
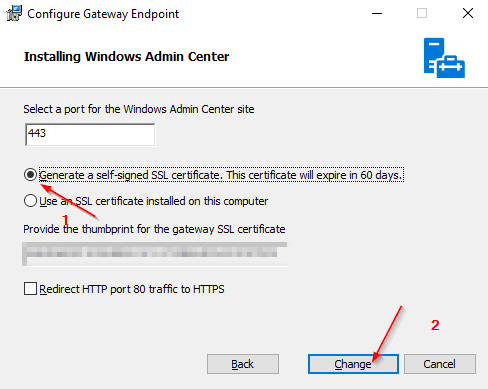
You could also use a separately created certificate at this point by providing its Thumprint ID to perform the necessary reassignment.
2) Scenario 2 - WAC - Gateway Installation
In order to avoid getting an expired certificate again in 60 days, I create myself a certificate which is valid for 10 years.
For this I switch to my Linux environment. In my case a WSL installation based on Ubuntu.
# Creating a cert - folder
mkdir certs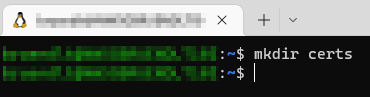
# Changing Directory
cd certs
# Generating the Cert
openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 -nodes \
-keyout cert.key -out cert.crt -extensions san -config \
<(echo "[req]";
echo distinguished_name=req;
echo "[san]";
echo subjectAltName=DNS:<fqdn>
) \
-subj "/CN=<fqdn>"
# Looking for the new generated certs
ls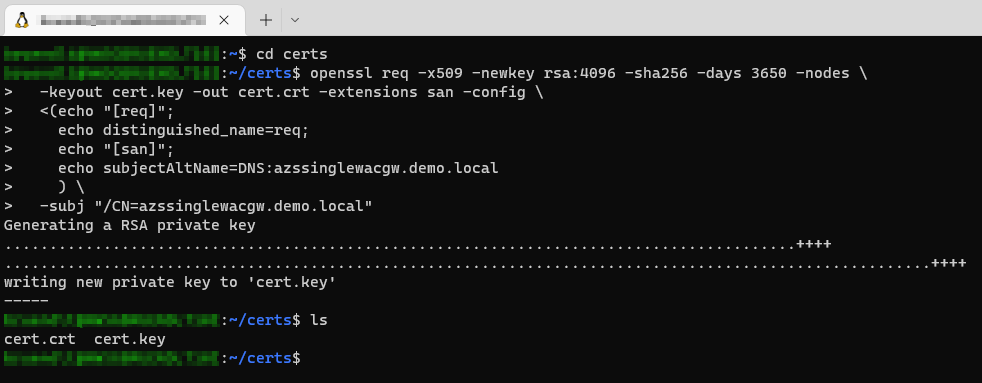
# Certificate conversion - CRT+Key = PFX
openssl pkcs12 -export -in cert.crt -inkey cert.key -out wac.pfx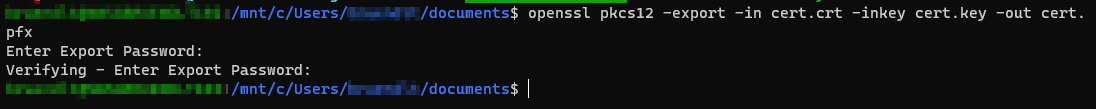
# Obtaining the certificates via Windows Explorer
\\wsl$\Ubuntu\home\bruendlt\certs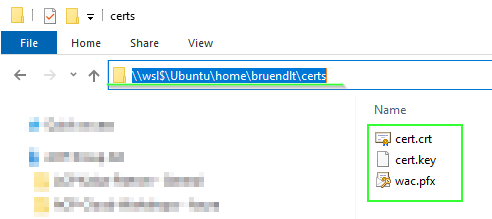
The changeover process:
# var
$GatewayServerName="<Hostname WAC - Gateway>"
# session
$Session=New-PSSession -ComputerName $GatewayServerName
# copy
Copy-Item -Path "$env:USERPROFILE\Downloads\wac.pfx" -Destination "$env:USERPROFILE\Downloads\wac.pfx" -ToSession $Session
# cert import
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Import-PfxCertificate -FilePath "$env:USERPROFILE\Downloads\wac.pfx" -CertStoreLocation Cert:LocalMachine\My -Exportable -Password (ConvertTo-SecureString -String '<PFX - File Password>' -AsPlainText -Force)}
# extract appId
$pattern = '(?<=\{).+?(?=\})'
$appId=[regex]::Matches((Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {netsh http show sslcert})[8], $pattern).Value
# thumprint
$Thumbprint = (Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem -Path Cert:\LocalMachine\MY | Where-Object {$_.Subject -Match "$GatewayServerName"} | Select-Object FriendlyName, Thumbprint, Subject, NotBefore, NotAfter| Sort-Object -Property NotAfter -Descending | Select-Object -first 1}).Thumbprint
# delete old binding
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {netsh http delete sslcert ipport=0.0.0.0:443}
# add new binding
$NetshArgumentList = "http add sslcert ipport=0.0.0.0:443 certhash="+$Thumbprint+" appid=`'{"+$appId+"}`'"
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Invoke-Expression "netsh $using:NetshArgumentList"}
# restart
Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Restart-Service ServerManagementGateway}
#add certificate to trusted root certs
$Subject = (Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem -Path Cert:\LocalMachine\MY | Where-Object {$_.Subject -Match "$GatewayServerName"} | Select-Object FriendlyName, Thumbprint, Subject, NotBefore, NotAfter| Sort-Object -Property NotAfter -Descending | Select-Object -first 1}).Subject
start-sleep 10
$cert = Invoke-Command -ComputerName $GatewayServerName -ScriptBlock {Get-ChildItem Cert:\LocalMachine\My\ |where subject -eq "$using:Subject"}
$cert | Export-Certificate -FilePath $env:TEMP\WACCert.cer
Import-Certificate -FilePath $env:TEMP\WACCert.cer -CertStoreLocation Cert:\LocalMachine\Root\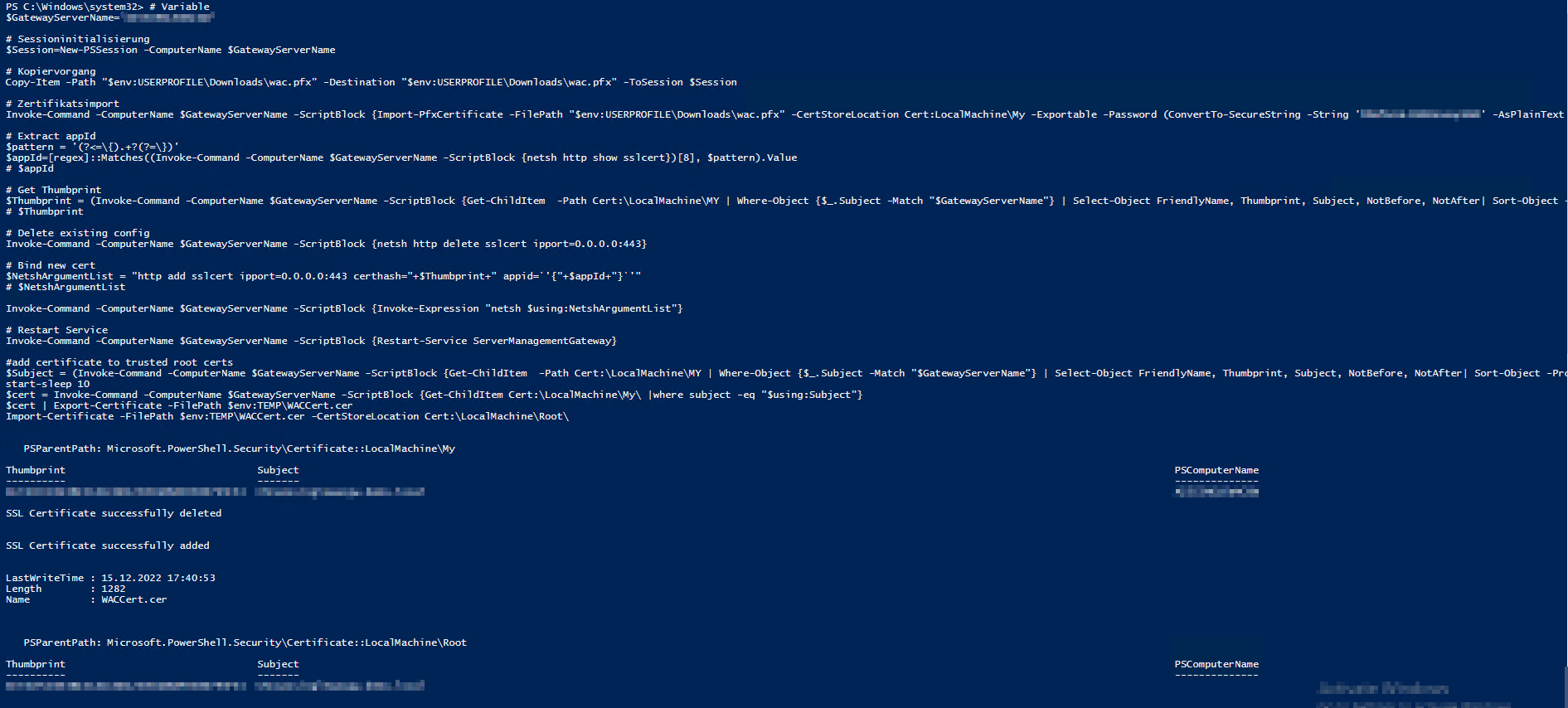
References:

https://it-infrastructure.solutions/windows-admin-center-hybrid-hub-to-the-cloud-azure-part-2/
Setting up WSL2 (Windows Subsytem for Linux) on Windows 10
Generating self-signed certificate files (Linux - Debian)




