❕This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage
Prerequisite:
- Nothing

Pic 1
The castle-and-moat theory forms the basis of conventional IT network security. Castle-and-moat security makes it difficult for outsiders to access the network, but by default, everyone on the network is trusted. This strategy has the drawback that an attacker has complete control over everything on the network once they get access to it.
Zero Trust Principles:
To implement Zero Trust in your organization, Microsoft defines 3 principles to follow.
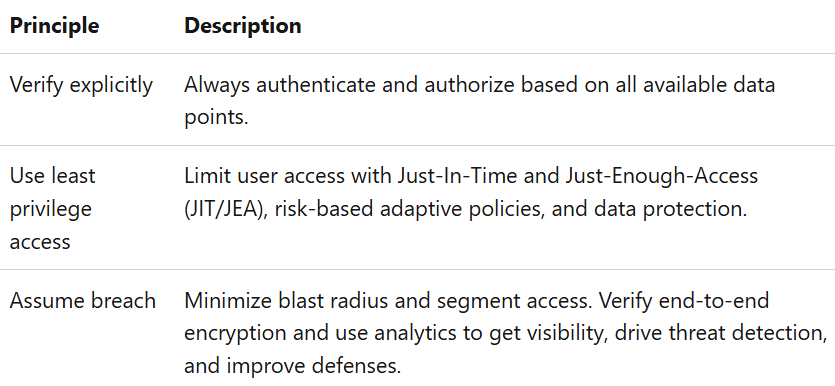
Tab 1
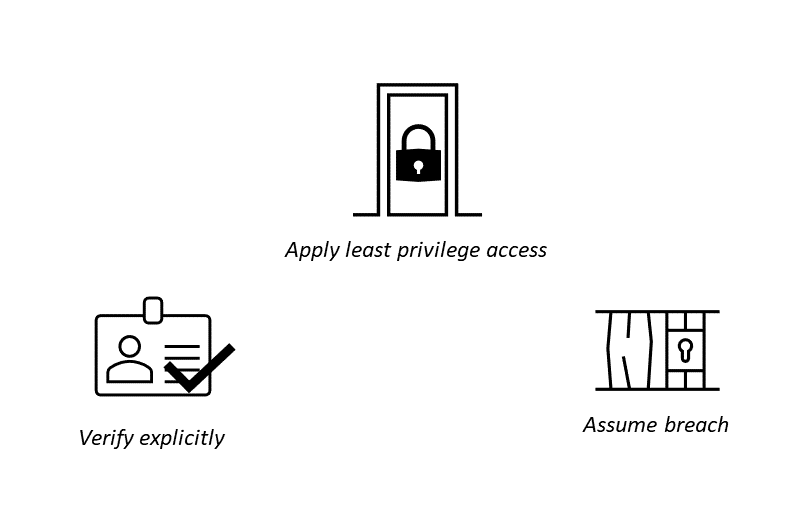
Pic 2
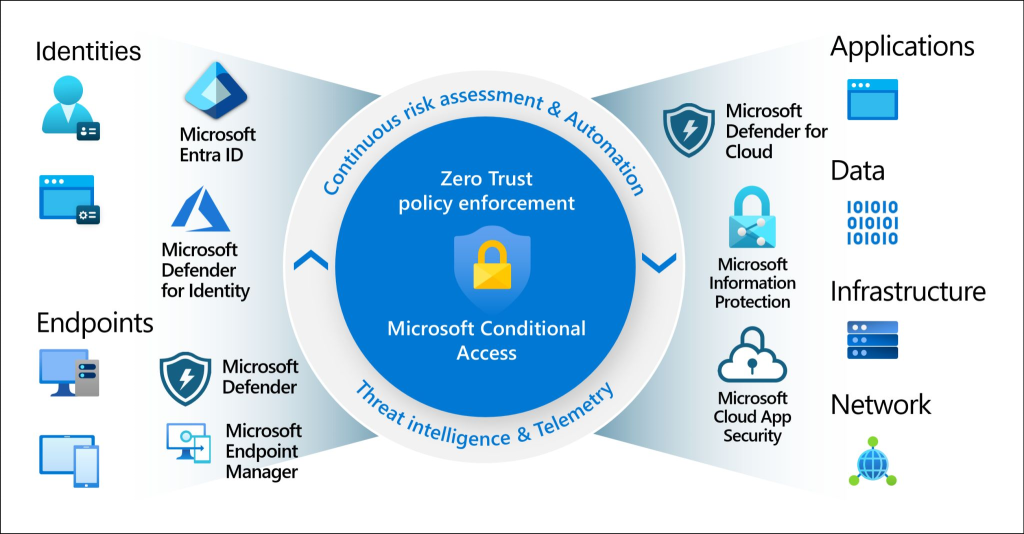
The question is how to implement these principles. Microsoft is one of the few vendors, that offer an integrated END 2 End strategy.
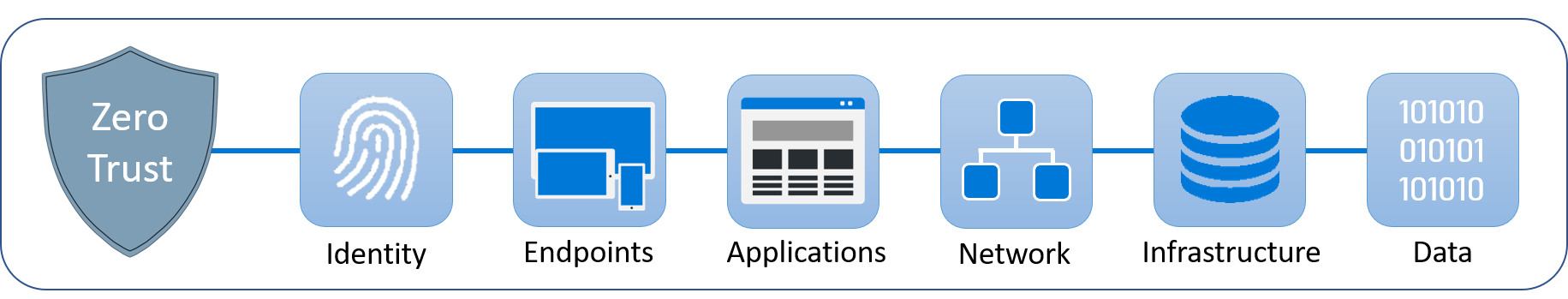
Pic 3
This is also known as defence in depth, because security happens on many different levels.
Let's stick with our castle and moat theory. This is not to say that there are no other security measures besides the network-related ones. In most cases, there are also other security products such as third-party antivirus solutions. However, the problem is that these products and solutions do not communicate with each other and this is where the great advantage of the Microsoft Security Suite comes into play.
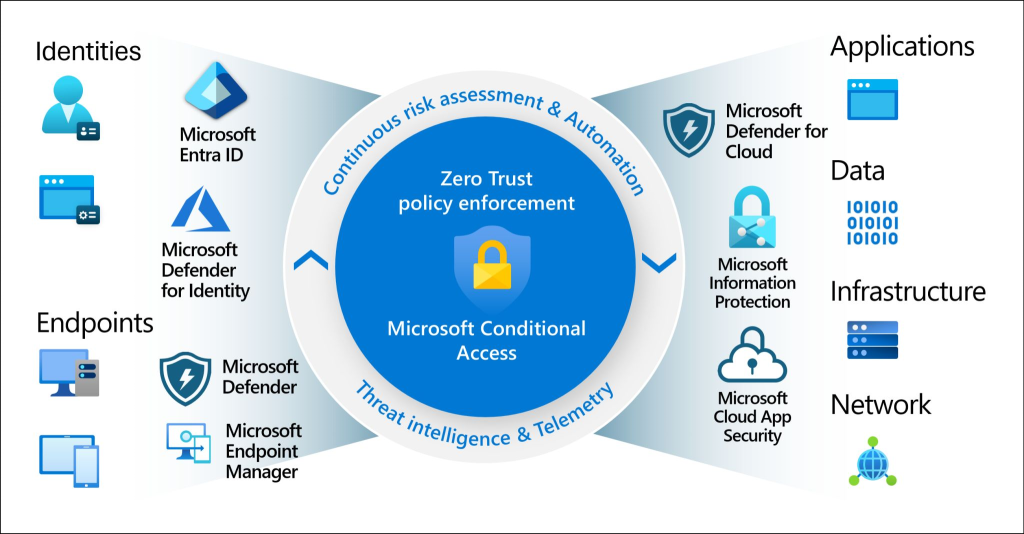
Pic 4
Let's map the objects / entities worth protecting from Pic 3/4 👆.
- Identities
Are strengthened using Entra ID (formerly Azure AD) & Microsoft Defender for Identity providing robust (onprem) authentication and authorization. - Endpoints
Services like Microsoft Intune (formerly Microsft Endpoint Manager) and Entra ID Join as well Microsft Defender for Endpoint manage the corporate and BYOD devices with strict compliance. - Applications
Azure Defender for Cloud, Azure Web Application Firewall (WAF) or Defender for Cloud Apps protects app services by using bleeding-edge security features. - Network
Azure network services like Azure Firewall and Virtual Networks are ensuring traffic is secure and segmented - Infrastructure
Secrets and certificates can be protected with Azure Key Vault services and Microsoft Defender for Cloud offers comprehensive threat protection from day zero - Data
Remains top priority in transit and rest with advanced security features of dedicated Storage services including Microsoft Purview (formerly Microsoft Information Protection) by providing secure, reliable, and scalable solutions.
This also maps to the cyber kill chain 👇 (see picture 5 below). There is also a mapping to the right products.
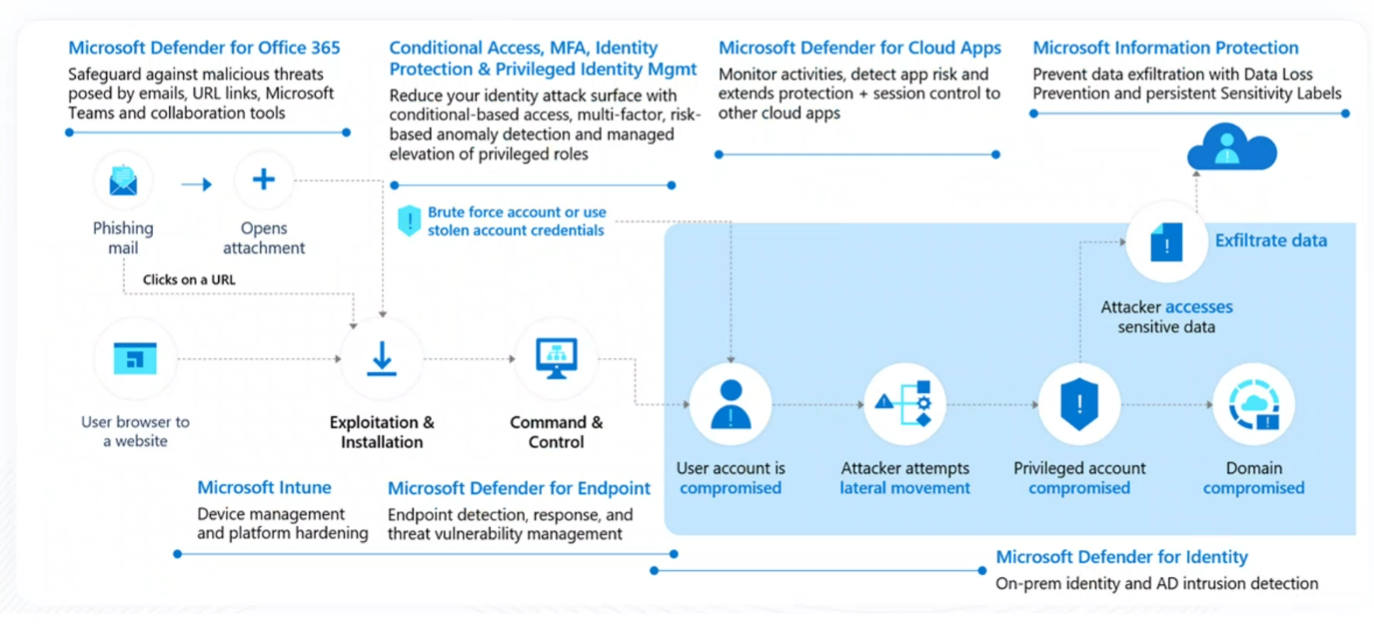
Pic 5
I hope this helps a little and gives an overview of how Microsoft is trying to implement Zero Trust with its products.
References:
https://www.cloudflare.com/learning/security/glossary/what-is-zero-trust/