
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
# Activate Hyper-V as the main virtualization environment
bcdedit /set hypervisorlaunchtype auto
# Deactivate Hyper-V as the main virtualization environment
bcdedit /set hypervisorlaunchtype off 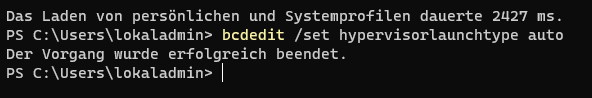
# Install Multipass
choco install multipass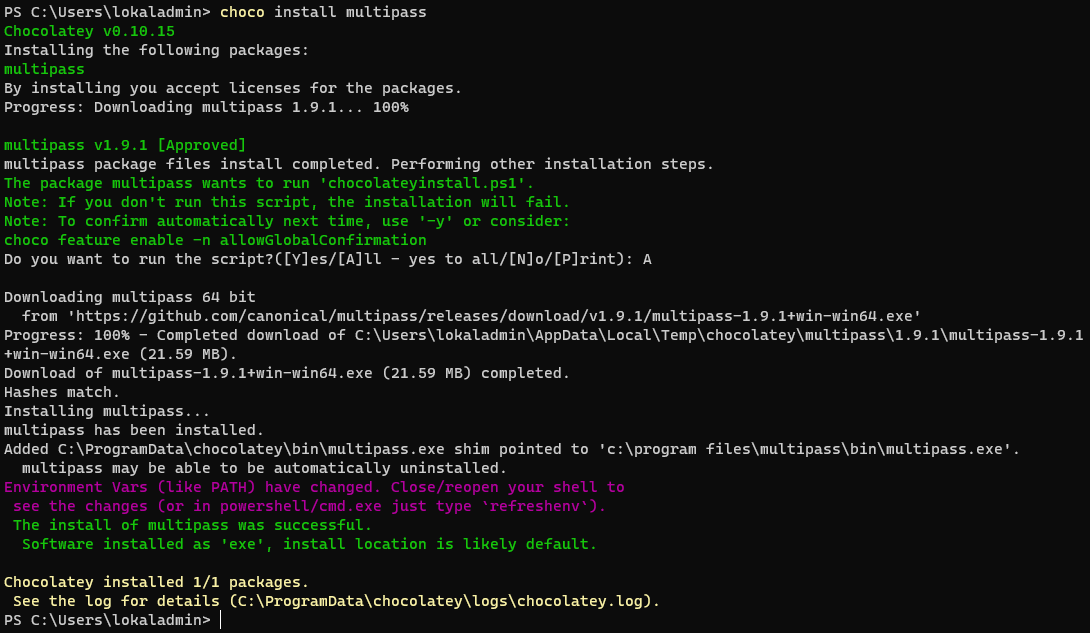
# Creating the necessary infrastructure
# Main- / Master node
multipass launch -n nmk8m1 -c 4 -m 6gb -d 20gb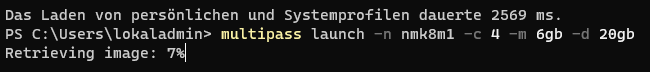
# Worker node
multipass launch -n nmk8w1 -c 2 -m 2gb -d 5gb
multipass launch -n nmk8w2 -c 2 -m 2gb -d 5gb
# Connecting to the master node
multipass shell nmk8m1
# Connecting to the worker nodes
multipass shell nmk8w1
multipass shell nmk8w2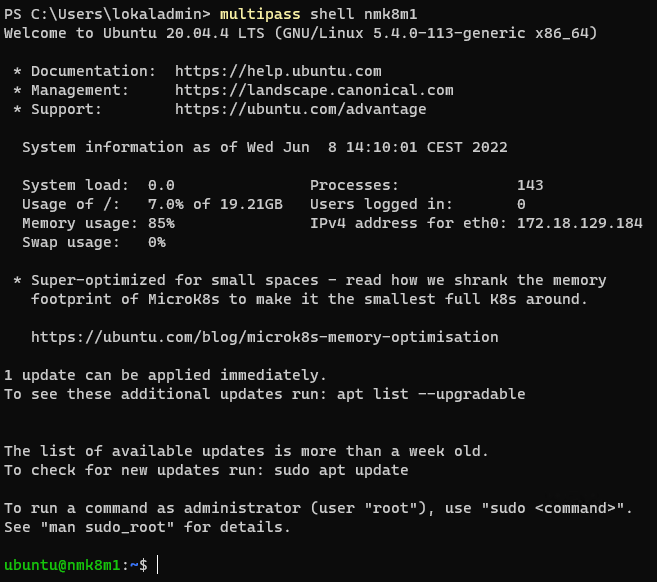
# Installing Microk8s (on each node)
sudo snap install microk8s --classic
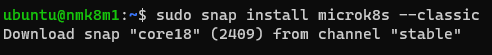
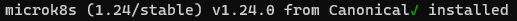
# Getting Microk8s Status (on each node)
sudo microk8s status --wait-ready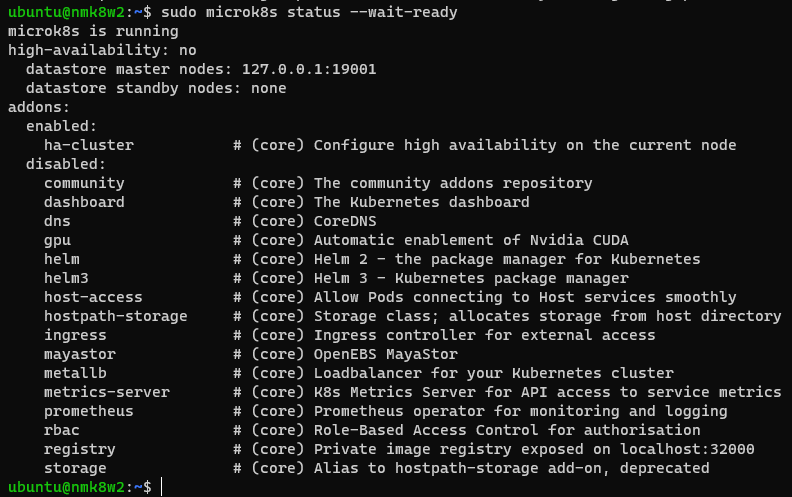
# Assign Userpermissions to use the microk8s command (on each node)
sudo usermod -aG microk8s $USER
sudo chown -f -R $USER ~/.kube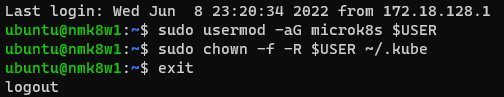
# Enable Addons (on the master node)
microk8s enable dns storage helm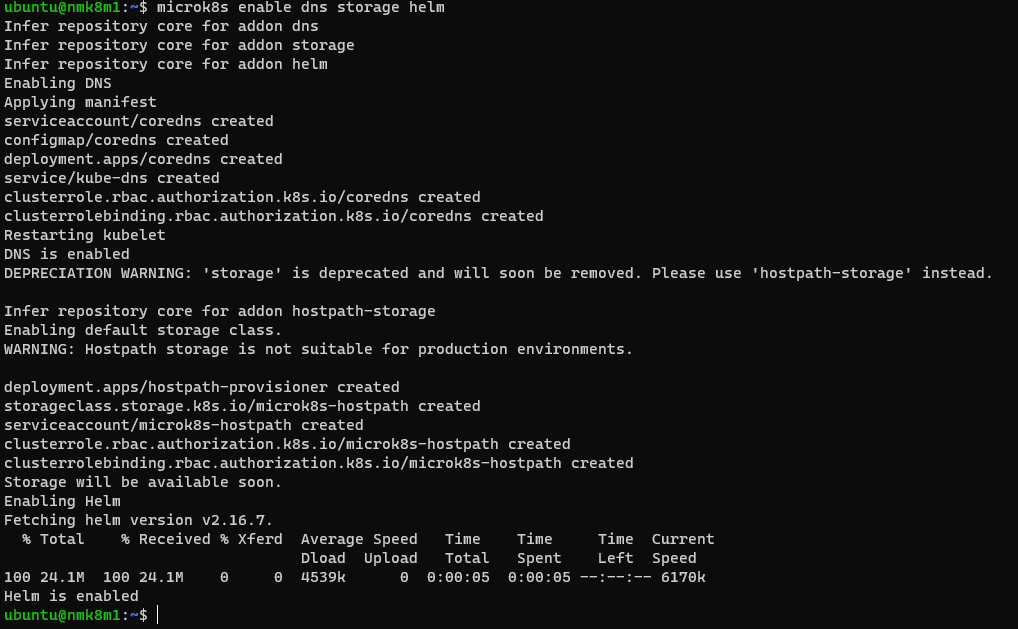
# Clustering
# @ master node
microk8s add-node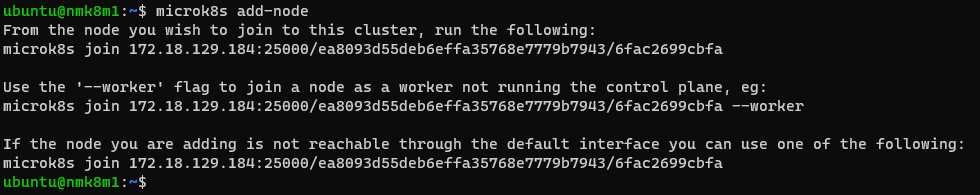
# Clustering
# @ worker nodes
microk8s join 172.18.129.184:25000/ea8093d55deb6effa35768e7779b7943/6fac2699cbfa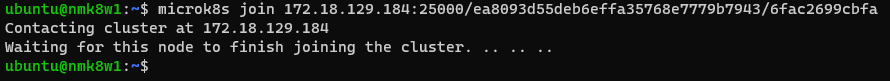
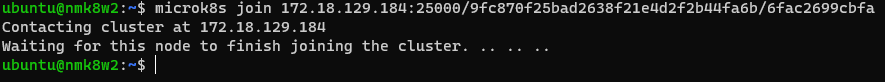
# Checking Cluster & Nodes
microk8s kubectl get nodes -o wide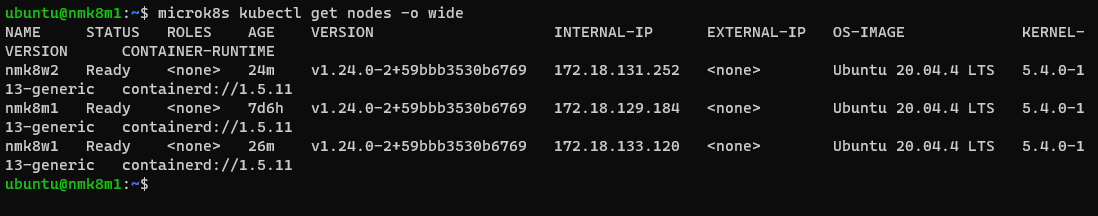
# Setting an Alias (on the master node)
alias kubectl='microk8s kubectl'
# Exporting kubeconfig (on the master node)
microk8s config >> ~/.kube/config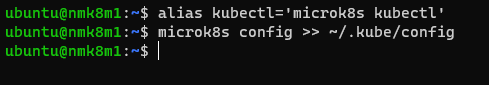
# Get & Set Cluster Context (on the master node)
kubectl config get-contexts
kubectl config use-context microk8s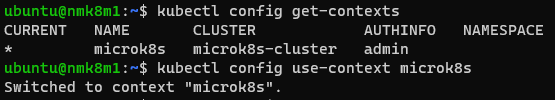
# Installing Azure CLI
curl -sL https://aka.ms/InstallAzureCLIDeb | sudo bash
source $HOME/.bashrc
# Azure CLI - Extension Installation
az extension add --name connectedk8s
# Login
az login
# Activating needed Resource Providers
az provider register --namespace Microsoft.Kubernetesa
az provider register --namespace Microsoft.KubernetesConfiguration
az provider register --namespace Microsoft.ExtendedLocation
# Ressource Group Creation
az group create --name test-kube-arc --location westeurope
# Create a Kubernetes - Azure Arc resource and connect your cluster
az connectedk8s connect \
--name testkube \
--resource-group test-kube-arc \
--location westeurope \
--tags type=microk8s location=TestLab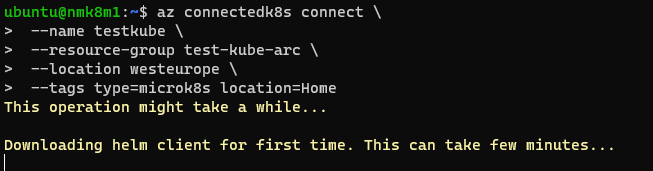
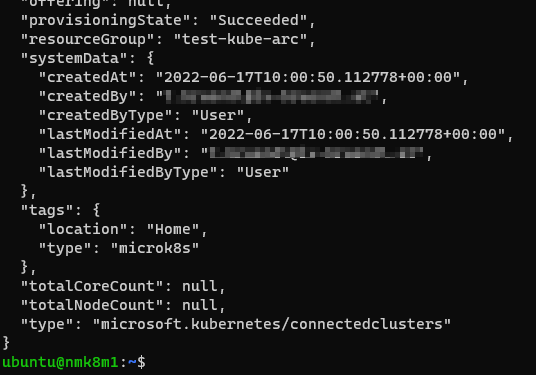
# Check Status
az connectedk8s show --name testkube --resource-group test-kube-arc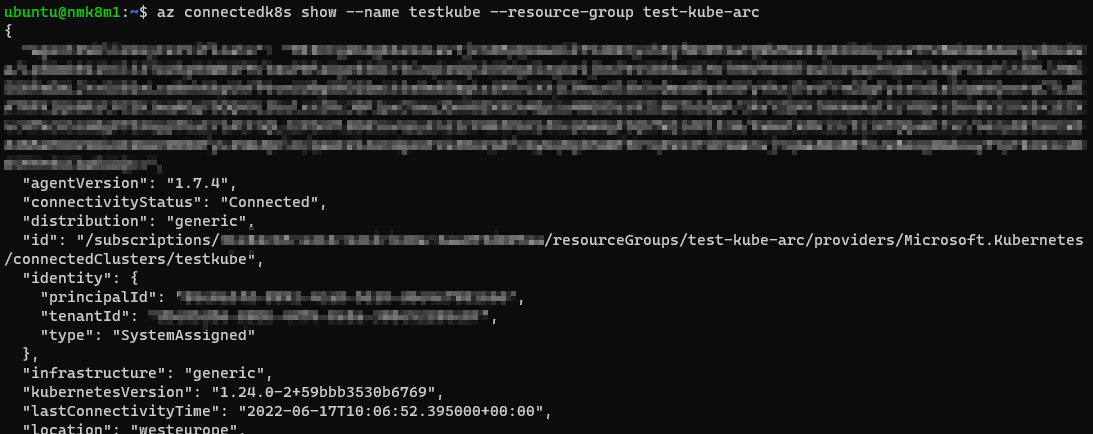
# Creating a Service User
kubectl create serviceaccount admin-user
# Assigning permissions
kubectl create clusterrolebinding admin-user-binding --clusterrole cluster-admin --serviceaccount default:admin-user# Receiving a bearer token (without creating a secret)
microk8s kubectl create token admin-user --duration=999999h# Generating a secret
microk8s kubectl apply -f - <<EOF
apiVersion: v1
kind: Secret
metadata:
name: admin-user
annotations:
kubernetes.io/service-account.name: admin-user
type: kubernetes.io/service-account-token
EOF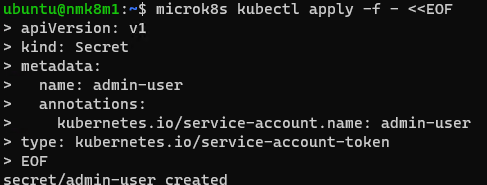
# Receiving a bearer token from secret
microk8s kubectl describe secrets/admin-user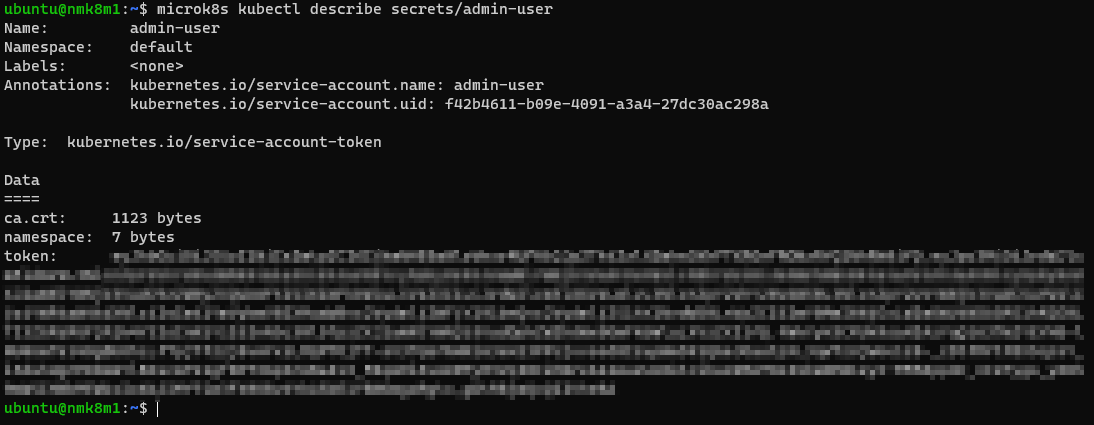
References:
Multi-cloud experiment with Azure Arc Kubernetes and Raspberry Pi cluster | LinkedIn
MicroK8s notes on installation with Azure ARC
MicroK8s - MicroK8s Addons | MicroK8s
MicroK8s is the simplest production-grade upstream K8s. Lightweight and focused. Single command install on Linux, Windows and macOS. Made for devops, great for edge, appliances and IoT. Full high availability Kubernetes with autonomous clusters.
Multipass 1.9.1
Multipass orchestrates virtual Ubuntu instances

MicroK8s - Working with kubectl | MicroK8s
MicroK8s is the simplest production-grade upstream K8s. Lightweight and focused. Single command install on Linux, Windows and macOS. Made for devops, great for edge, appliances and IoT. Full high availability Kubernetes with autonomous clusters.
https://it-infrastructure.solutions/how-to-create-a-service-account-bearer-token/
Verwenden von Cluster Connect zum Herstellen einer Verbindung mit Kubernetes-Clustern mit Azure Arc-Unterstützung - Azure Arc
Verwenden von Cluster Connect zum sicheren Herstellen einer Verbindung mit Kubernetes-Clustern mit Azure Arc-Unterstützung

BIG change in K8s 1.24 about ServiceAccounts and their Secrets
I created a SCENARIO where you can follow simple steps to see the changes interactively in your browser. Once the Pod is running you can see that there is still a token inside, so if your application…





