
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
1)

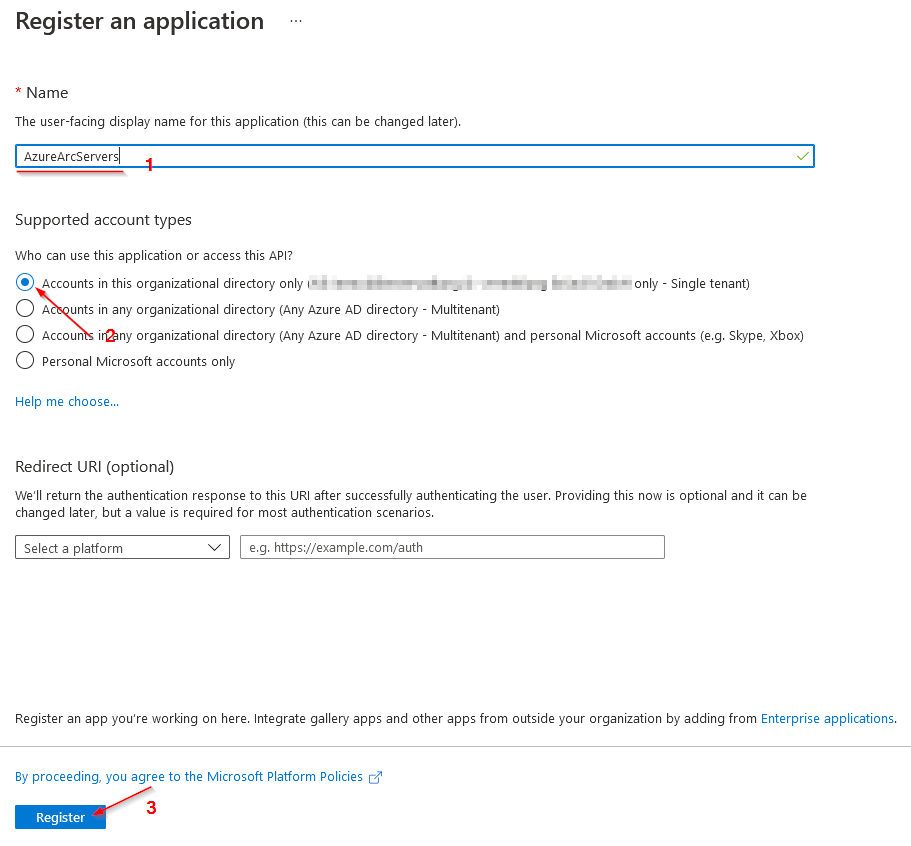
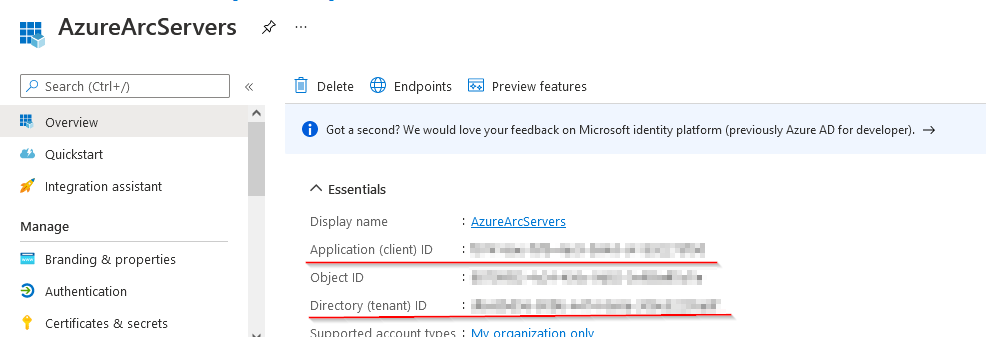
# servicePrincipalTenantId
(Get-AzContext).Tenant.Id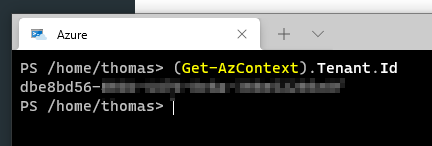
2)

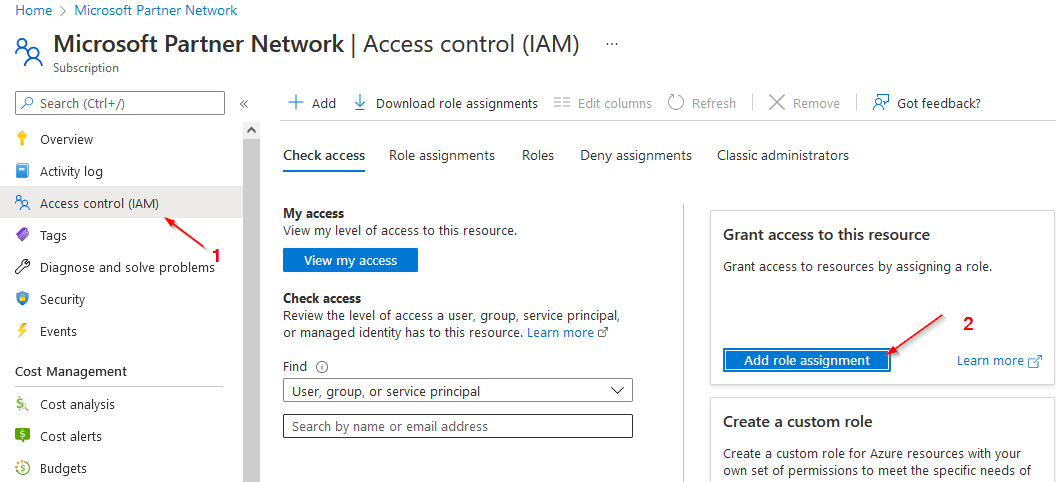
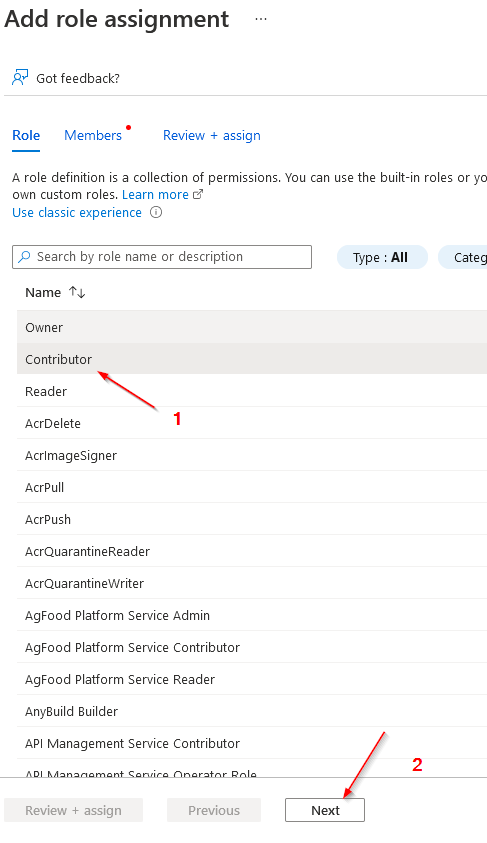
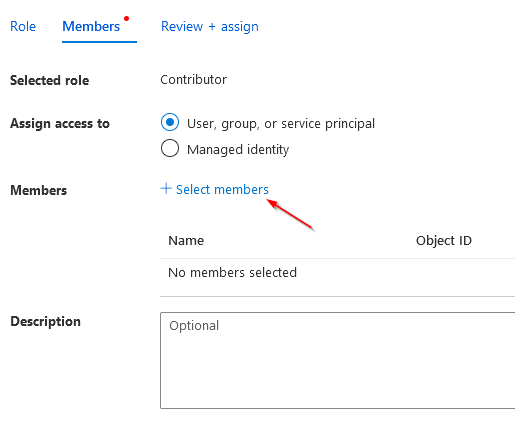
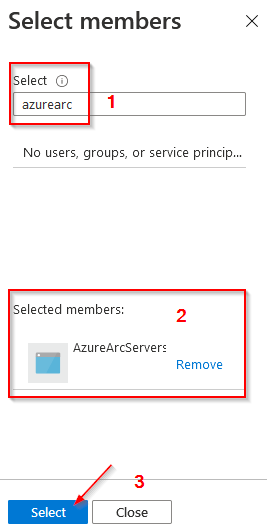
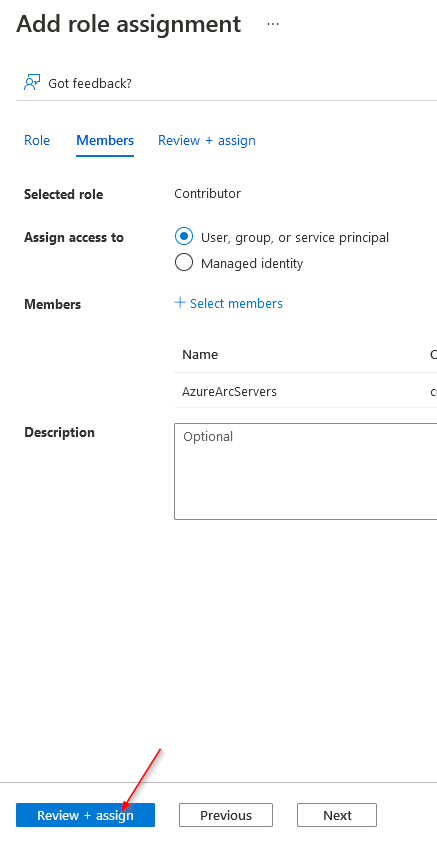
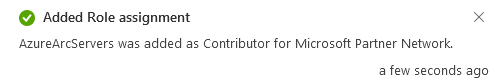
3)
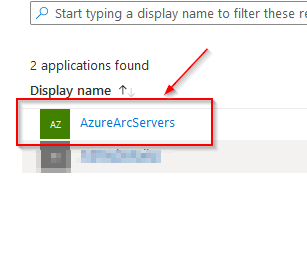
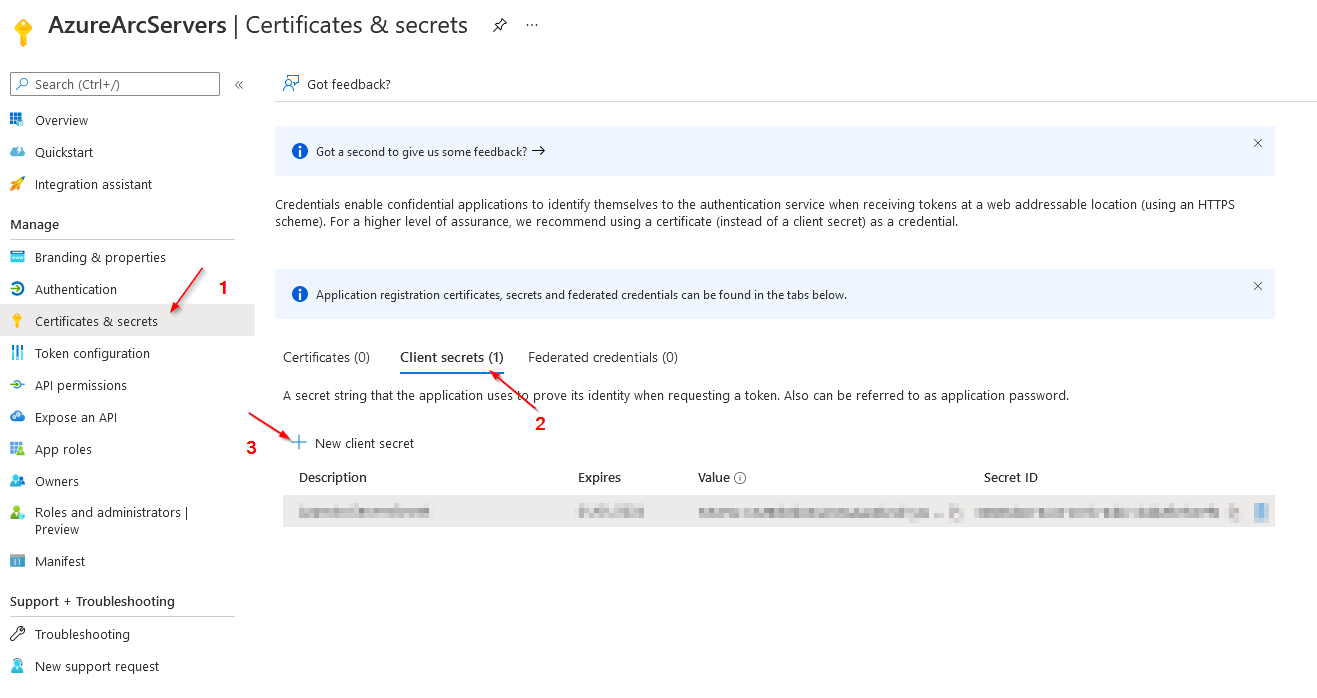
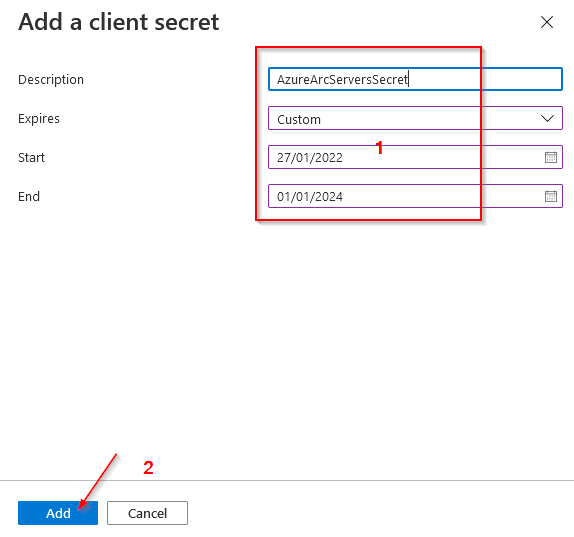
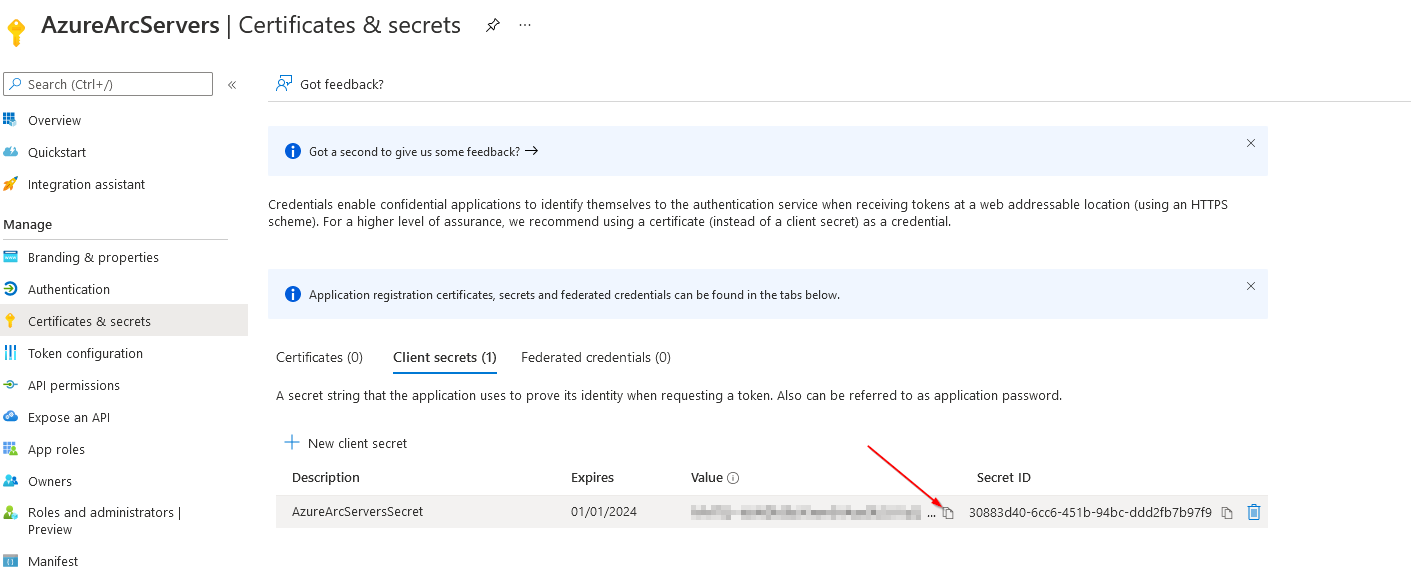
4)
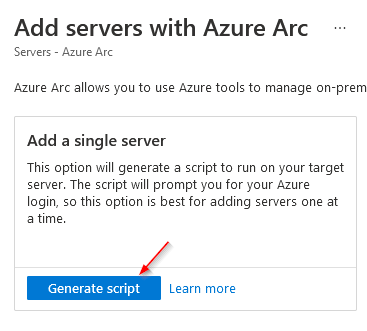
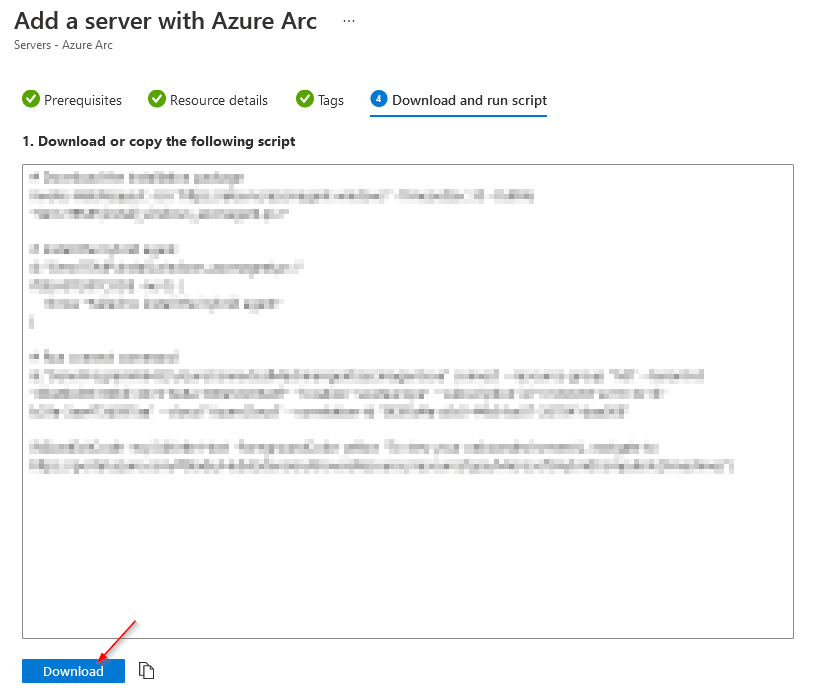
# Download the installation package
Invoke-WebRequest -Uri "https://aka.ms/azcmagent-windows" -TimeoutSec 30 -OutFile "$env:TEMP\install_windows_azcmagent.ps1"
# Install the hybrid agent
& "$env:TEMP\install_windows_azcmagent.ps1"
if($LASTEXITCODE -ne 0) {
throw "Failed to install the hybrid agent"
}
# Run connect command
& "$env:ProgramW6432\AzureConnectedMachineAgent\azcmagent.exe" connect --resource-group "<RG>" --tenant-id "<Tenant-ID>" --location "westeurope" --subscription-id "<Subscription-ID>" --cloud "AzureCloud" --correlation-id "<Correlation-ID>"
if($LastExitCode -eq 0){Write-Host -ForegroundColor yellow "To view your onboarded server(s), navigate to https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines"}
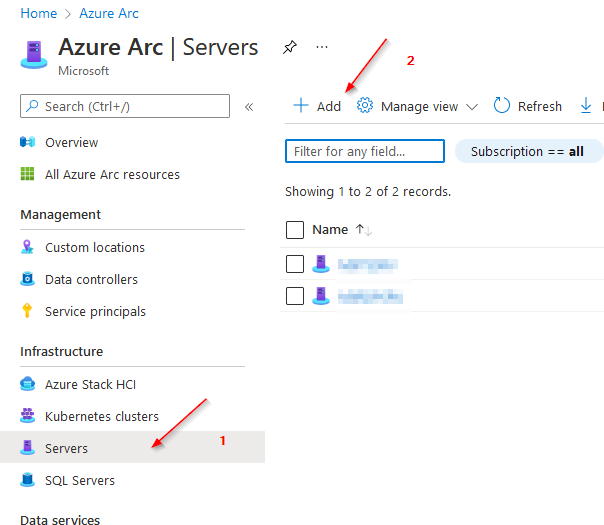
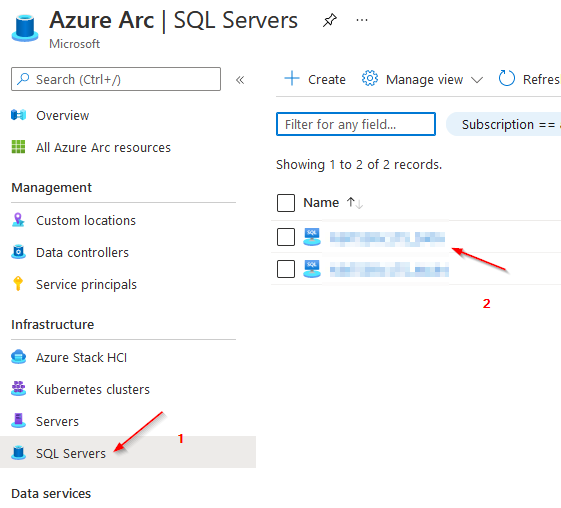
If more than one machine needs to be onboarded to Azure, this can of course be done via script as well. The required steps for this are described here.
https://it-infrastructure.solutions/connect-hybrid-machines/
5)
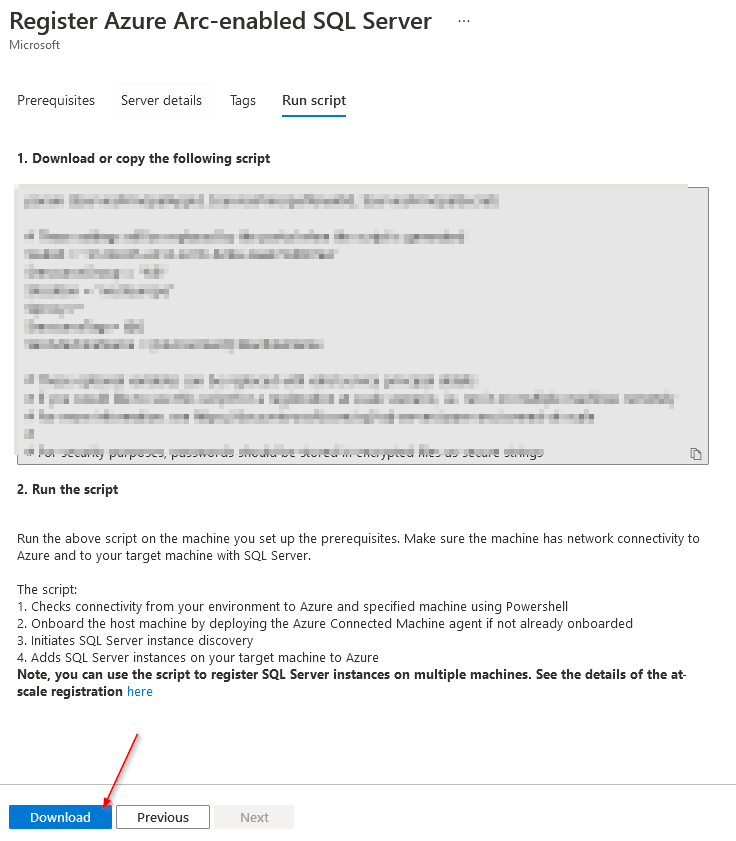
param ($servicePrincipalAppId, $servicePrincipalTenantId, $servicePrincipalSecret)
# These settings will be replaced by the portal when the script is generated
$subId = "<Subscription-ID>"
$resourceGroup = "<RG>"
$location = "westeurope"
$proxy=""
$resourceTags= @{}
$arcMachineName = [Environment]::MachineName
# These optional variables can be replaced with valid service principal details
# if you would like to use this script for a registration at scale scenario, i.e. run it on multiple machines remotely
# For more information, see https://docs.microsoft.com/sql/sql-server/azure-arc/connect-at-scale
#
# For security purposes, passwords should be stored in encrypted files as secure strings
#
#$servicePrincipalAppId = '<SPA-ID>'
#$servicePrincipalTenantId = '<SPT-ID>'
#$servicePrincipalSecret = '<SPS>'
........
https://it-infrastructure.solutions/how-to-set-up-a/
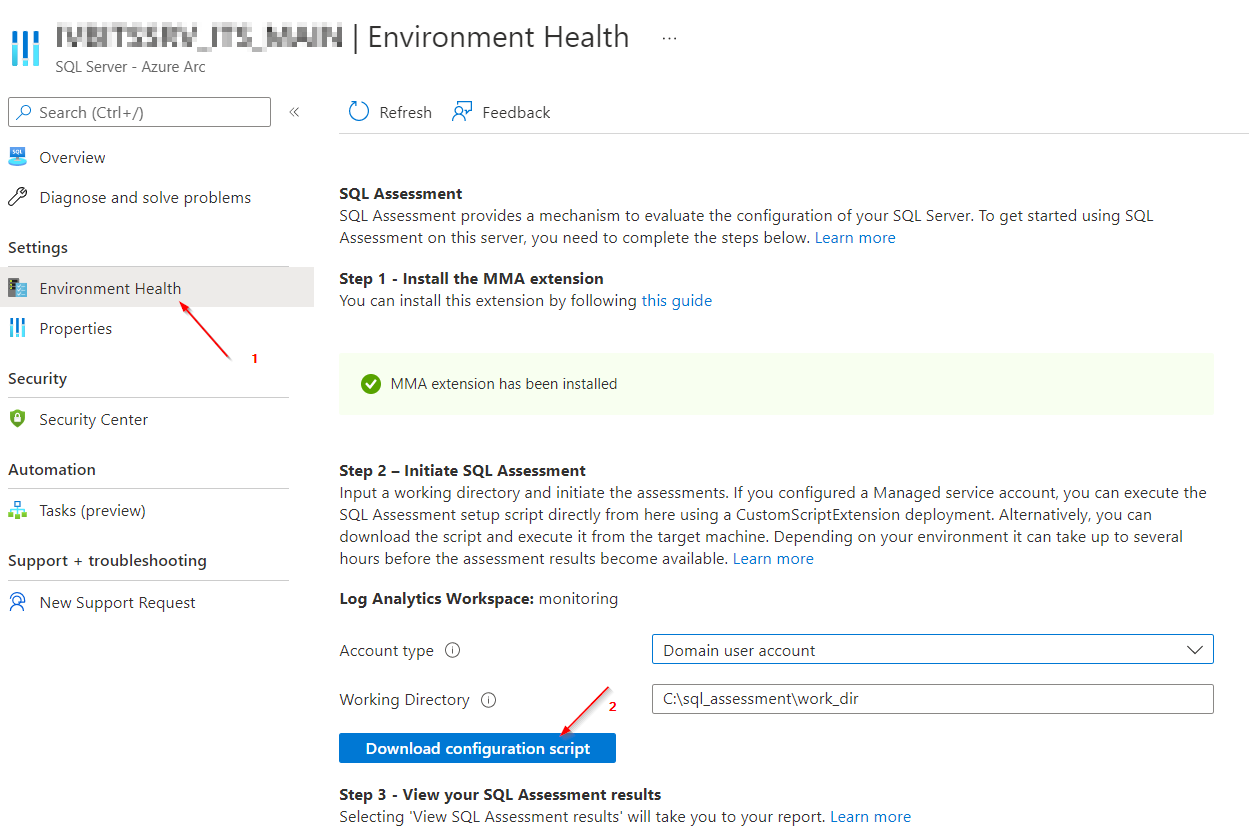
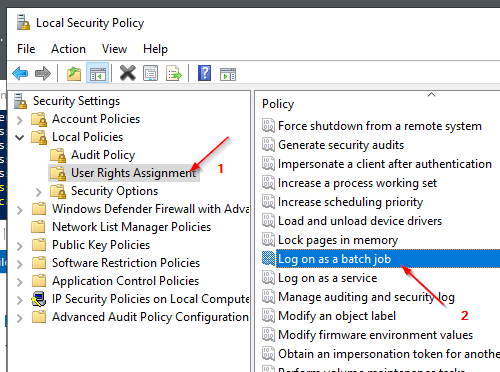
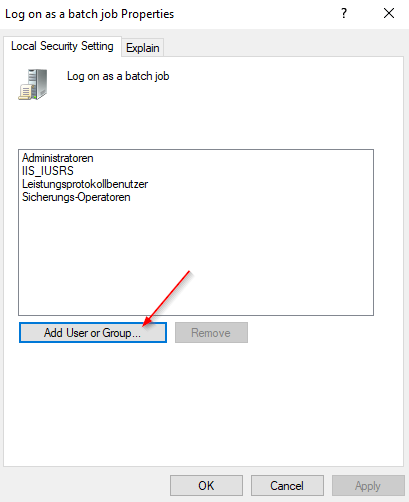
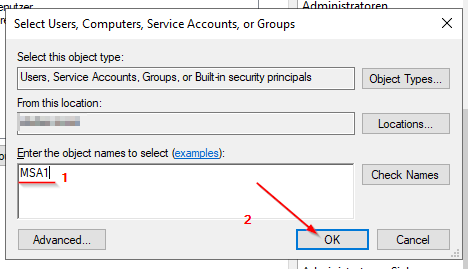
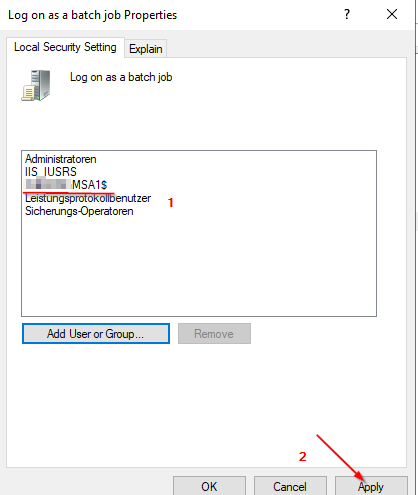
The Managed Service Account (MSA) should have the following rights:
- Member of the local Administrators group on all servers in the environment
- SysAdmin role on all Microsoft SQL Servers in the environment.
# Configuration Script
# FQDN = Fully Qualified Domain Name
[CmdletBinding()]
Param(
[Parameter(Mandatory=$false)]
[string]$ManagedServiceAccountName
)
if ($ManagedServiceAccountName)
{
Add-SQLAssessmentTask -SQLServerName "<FQDN>" -WorkingDirectory "C:\sql_assessment\work_dir" -RunWithManagedServiceAccount $True -ScheduledTaskUsername $ManagedServiceAccountName -ScheduledTaskPassword (new-object System.Security.SecureString)
}
else
{
Add-SQLAssessmentTask -SQLServerName "<FQDN>" -WorkingDirectory "C:\sql_assessment\work_dir"
}
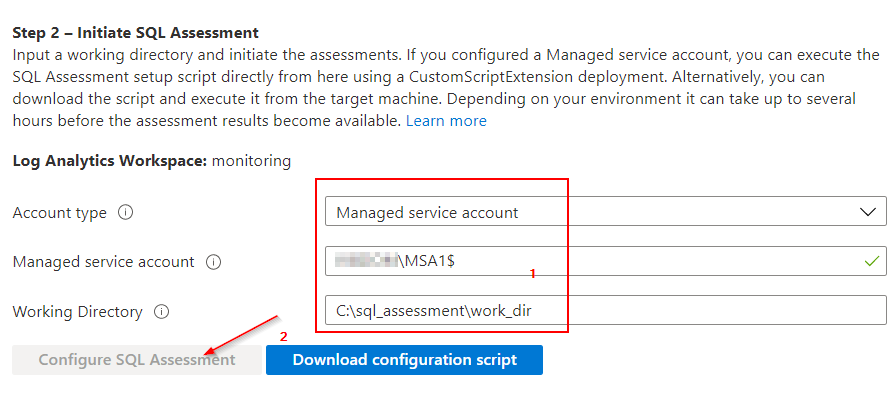
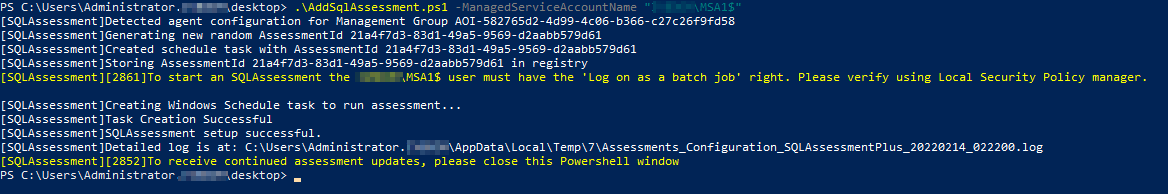
Sources:
Create an Azure AD app and service principal in the portal - Microsoft identity platform
Create a new Azure Active Directory app and service principal to manage access to resources with role-based access control in Azure Resource Manager.

Connect SQL Servers on Azure Arc-enabled servers at scale
In this article, you learn different ways of connecting SQL Server instances to Azure Arc at scale.

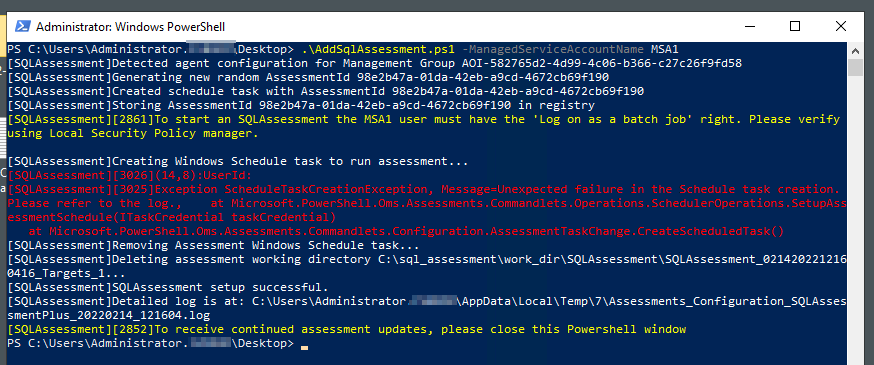
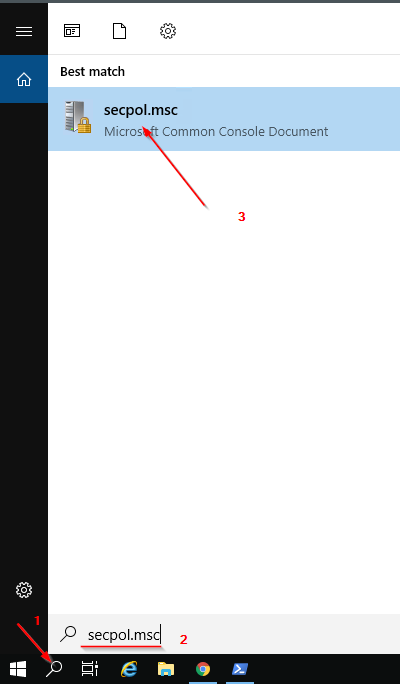
Granting “Logon as a batch job” | Brooksnet
If you have a Windows service that accesses shared resources, such as shared drives and shared printers, you need to launch a process as a user with “Logon as batch” enabled.

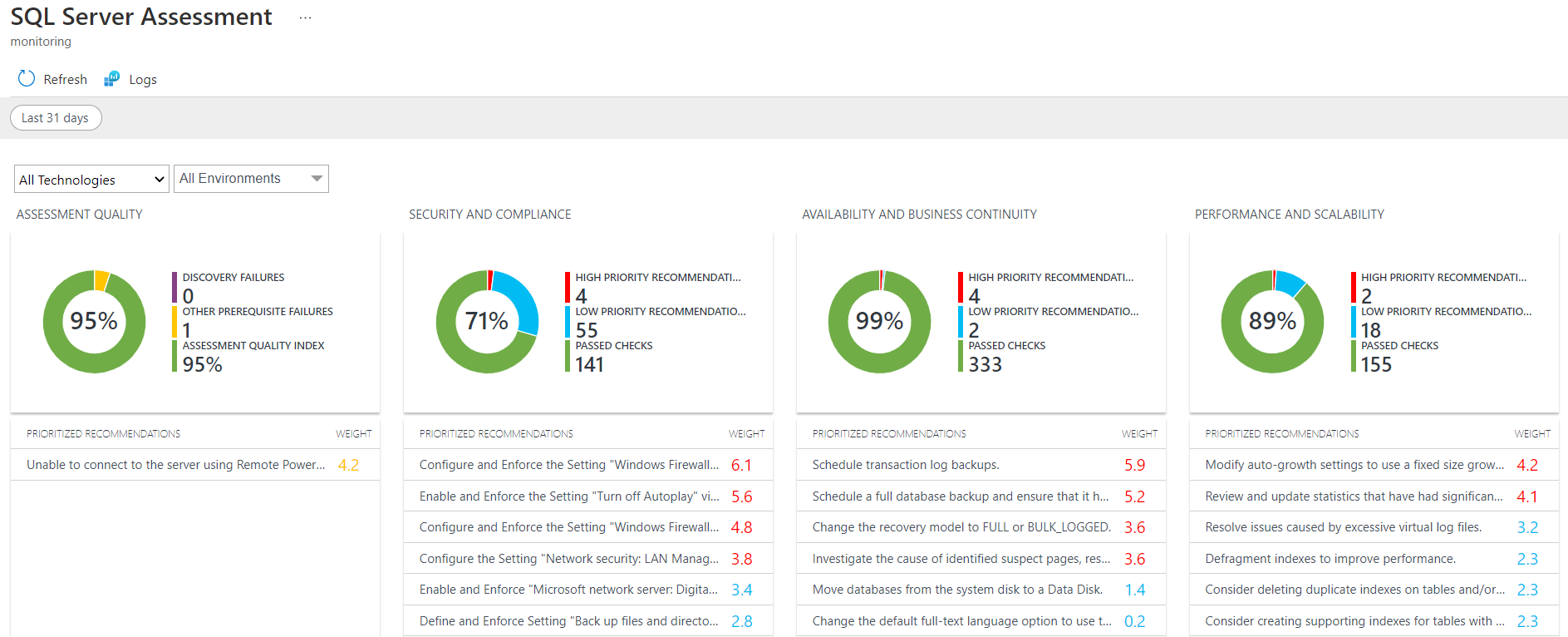
https://docs.microsoft.com/en-us/services-hub/health/getting-started-sql
https://docs.microsoft.com/en-us/services-hub/health/assessment_prereq_docs/prereqssqlassessment.pdf
