
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Prerequisites:
- An operational Azure Key Vault
- An imported certificate
- The right permissions
- An Azure Arc enabled server
Links that might be useful in this case:
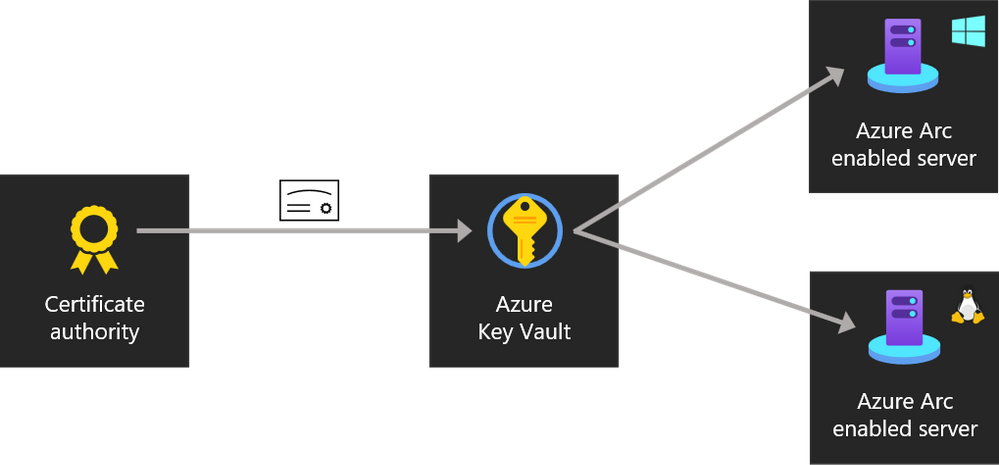
Architectural outline:
# PSVersion Check - at least Version 5.1 required
$PSVersionTable
# Installing the Azure Connected Machine PowerShell module
Install-Module Az.ConnectedMachine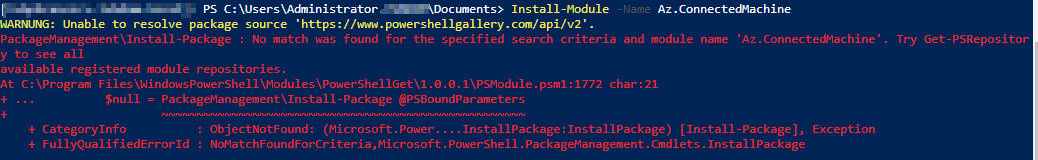
# Security Protocol Check
[Net.ServicePointManager]::SecurityProtocol
# Modifying the Security Protocol Settings
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12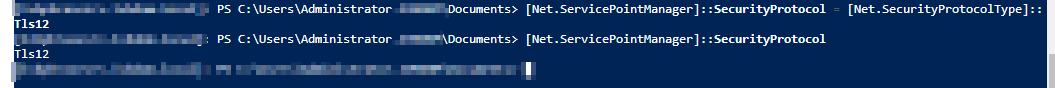
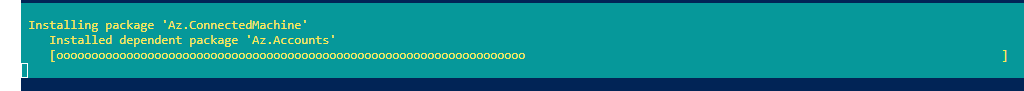
# Installing the Azure Connected Machine PowerShell module
Install-Module Az.ConnectedMachine
# Alternatively, you can install the entire module
Install-Module -Name Az -AllowClobber -Scope AllUsers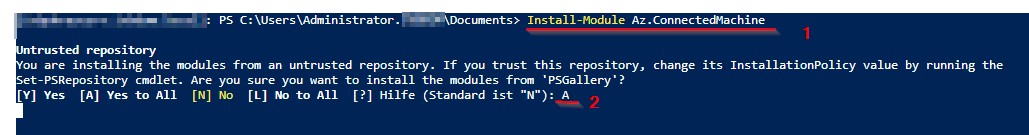
# Importing the newly installed module
Import-Module Az.ConnectedMachine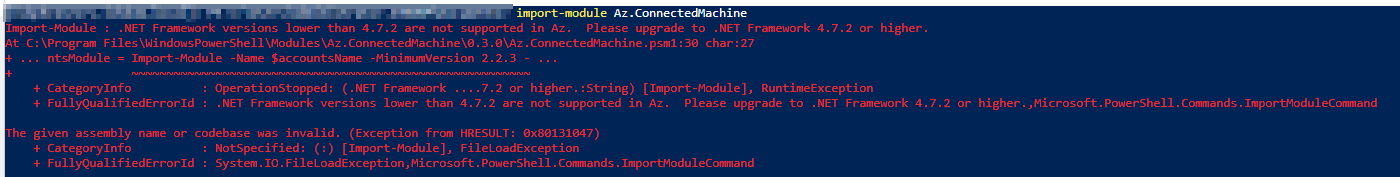
# Checking Net Framework Version
Get-ChildItem 'HKLM:\SOFTWARE\Microsoft\NET Framework Setup\NDP' -Recurse | Get-ItemProperty -Name version -EA 0 | Where { $_.PSChildName -Match '^(?!S)\p{L}'} | Select PSChildName, version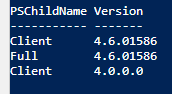
If you need to install "Chocolatey" follow this Link
# Installing NET Framework (latest Version)
choco install dotnetfx -y -f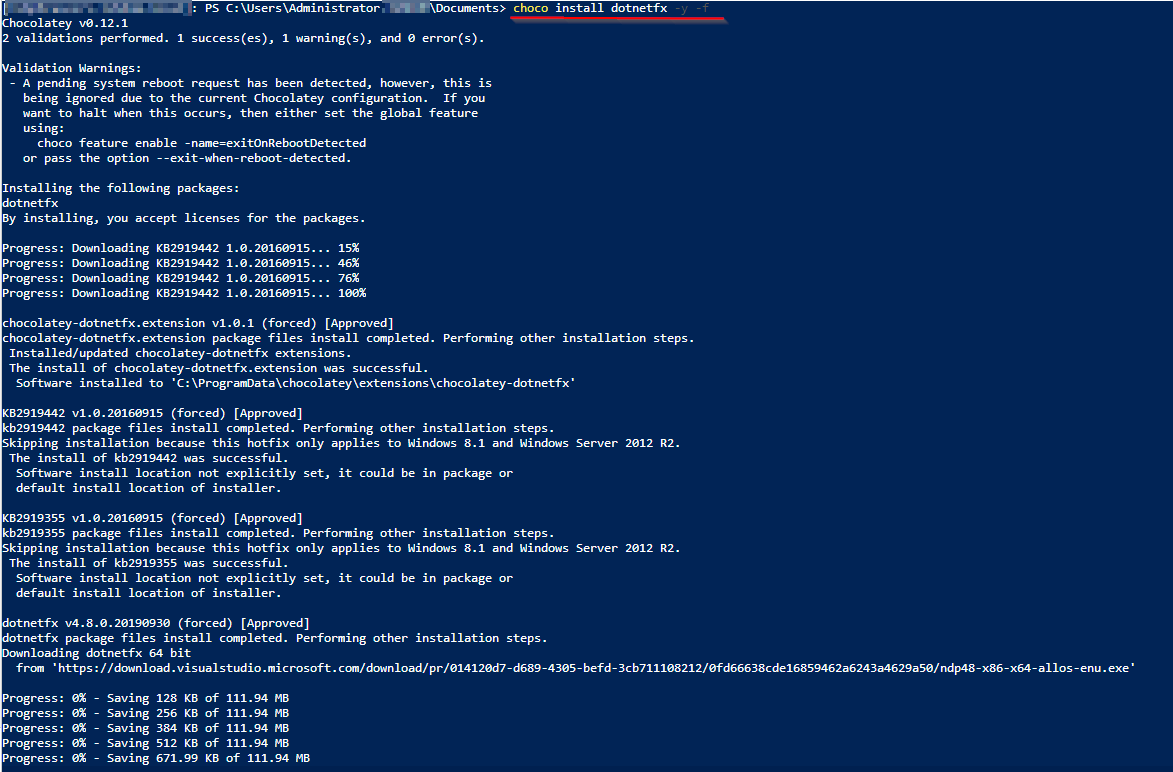
......
Permission Setup:
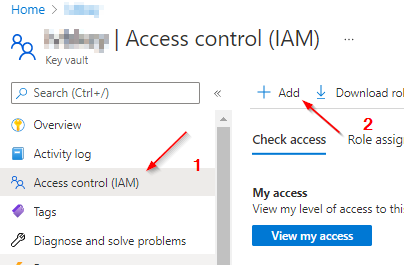
Grant the Arc enabled server the Key Vault Secrets User role in Access control (IAM) for the vault
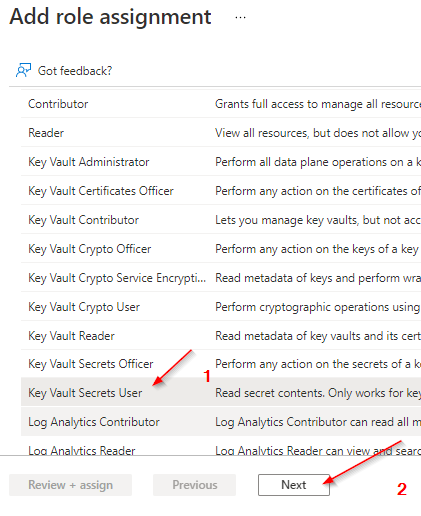
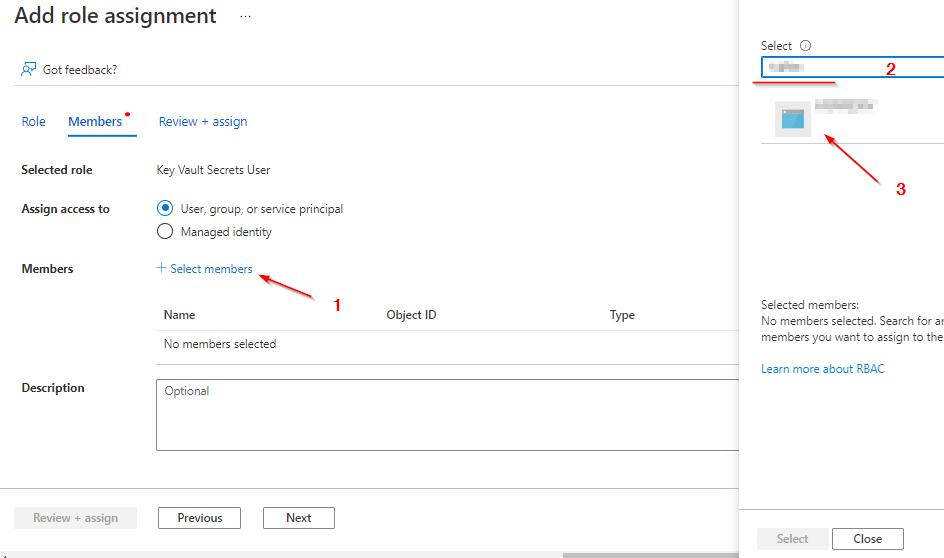

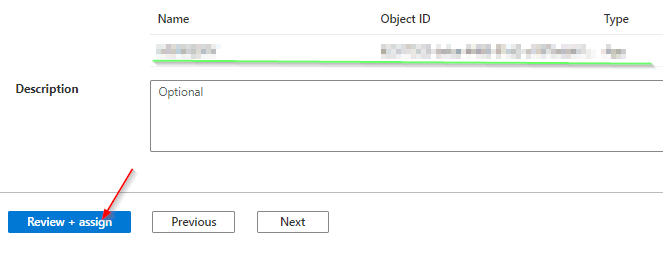
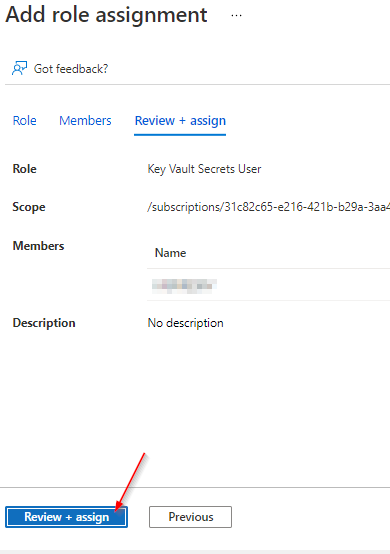
Deploy the Azure Arc Key Vaultextension
# Connecting to Azure
Connect-AzAccount -UseDeviceAuthentication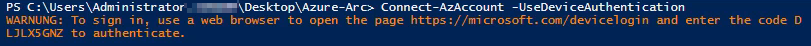



$Settings = @{
secretsManagementSettings = @{
observedCertificates = @(
"https://YOURVAULTNAME.vault.azure.net/secrets/YOURCERTIFICATENAME"
# Add more here in a comma separated list
)
certificateStoreLocation = "LocalMachine"
certificateStoreName = "My"
pollingIntervalInS = "3600" # every hour
}
authenticationSettings = @{
# Don't change this line, it's required for Arc enabled servers
msiEndpoint = "http://localhost:40342/metadata/identity"
}
}
$ResourceGroup = "ARC_SERVER_RG_NAME"
$ArcMachineName = "ARC_SERVER_NAME"
$Location = "ARC_SERVER_LOCATION (e.g. eastus2)"
$SubID = "Subscription ID "
New-AzConnectedMachineExtension -SubscriptionId $SubID -ResourceGroupName $ResourceGroup -MachineName $ArcMachineName -Name "KeyVaultForWindows" -Location $Location -Publisher "Microsoft.Azure.KeyVault" -ExtensionType "KeyVaultForWindows" -Setting (ConvertTo-Json $Settings)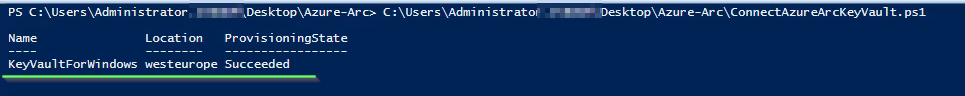

References:
https://it-infrastructure.solutions/how-to-create-an-azure-key-vault/
https://it-infrastructure.solutions/importing-an-certificate-to-azure-key-vault/
Manage Certificates on your Hybrid Servers using Azure Arc Key Vault Extension
Managing certificates is an important scenario when it comes to server management. You want to make sure you can roll out certificates to your servers and manage these from a central place. In a pure on-premises environment, we have done this for example by using Group Policies (GPOs). But if you wa…

Connect a Hybrid Server to Azure using Azure Arc
No match was found for the specified search criteria and module name ‘Az’
Here are three ways to check the .NET Framework version on Windows 10
In this guide, we’ll show you the easy steps to determine the version of .NET available on your installation of Windows 10.


