
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Deploy VPN - Gateway:
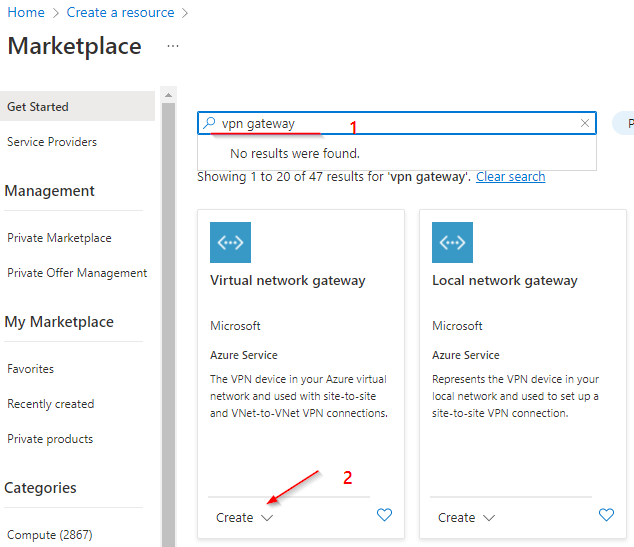
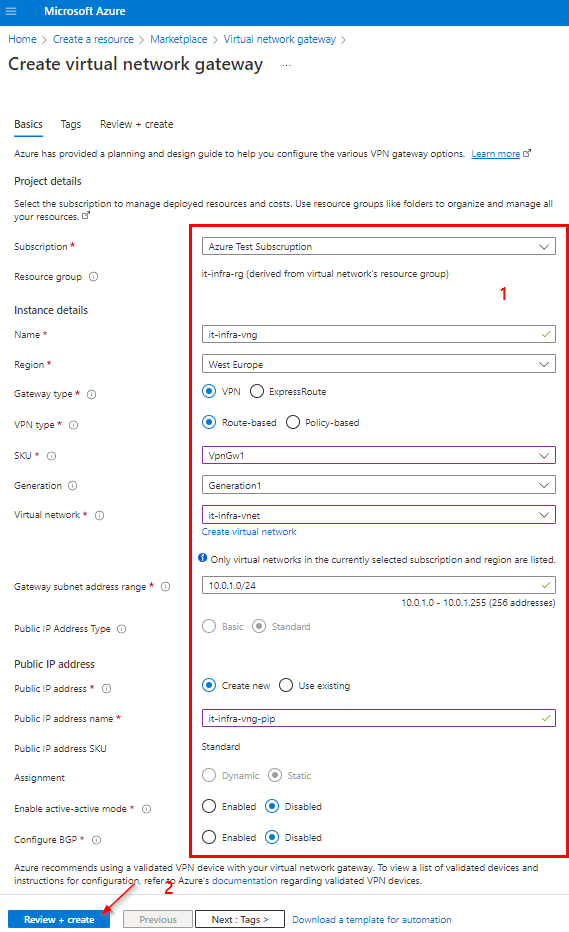
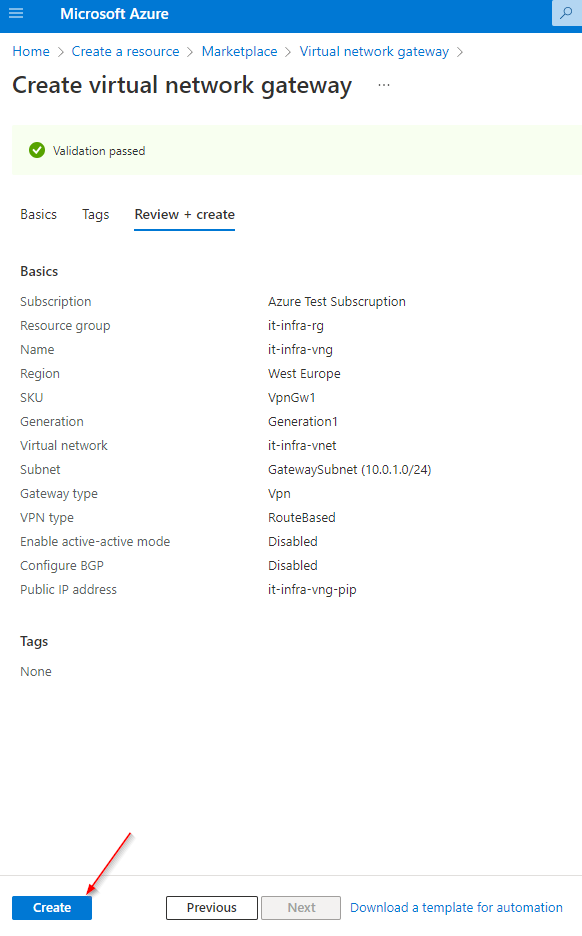
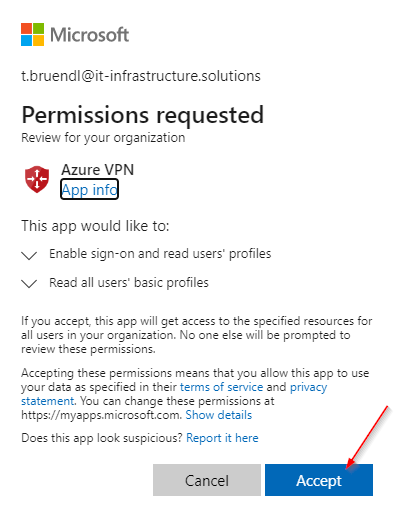
Grant Admin Consent :
https://login.microsoftonline.com/common/oauth2/authorize?client_id=41b23e61-6c1e-4545-b367-cd054e0ed4b4&response_type=code&redirect_uri=https://portal.azure.com&nonce=1234&prompt=admin_consent
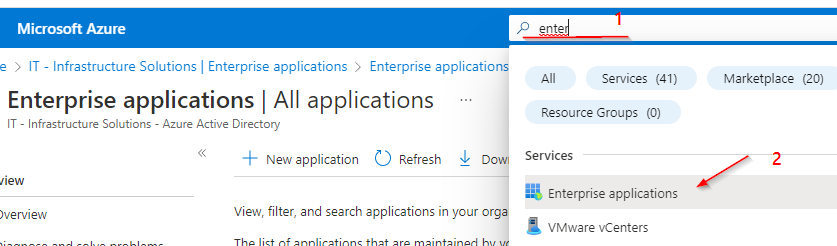
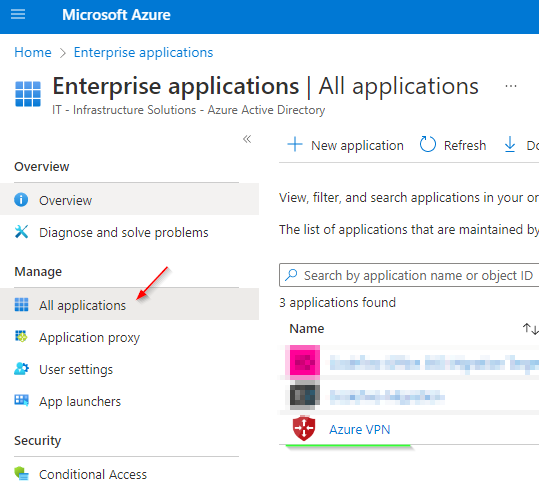
Retrieving the Tenant ID:
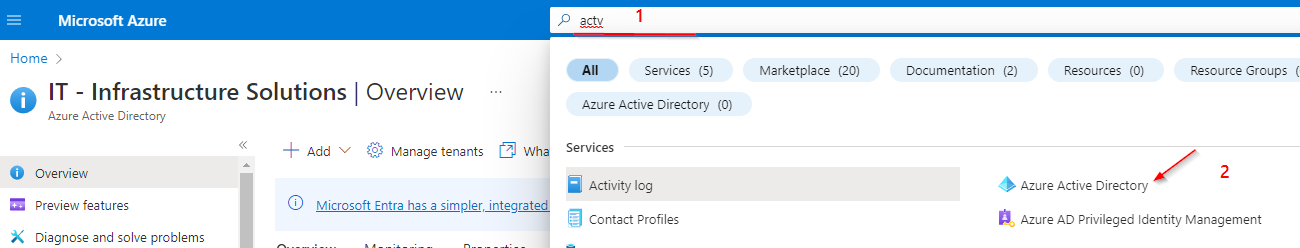
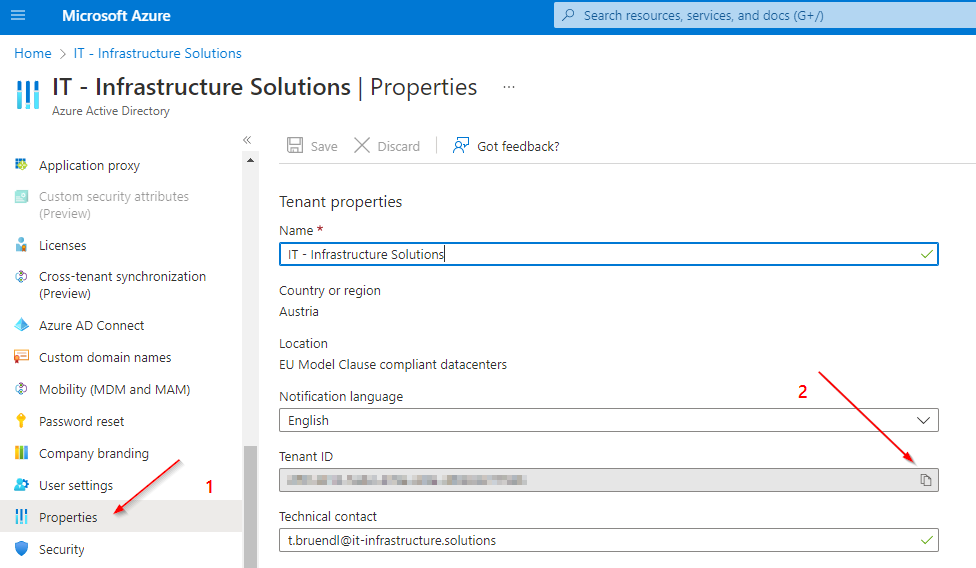
Store the tenant ID temporarily. We will need it again later.
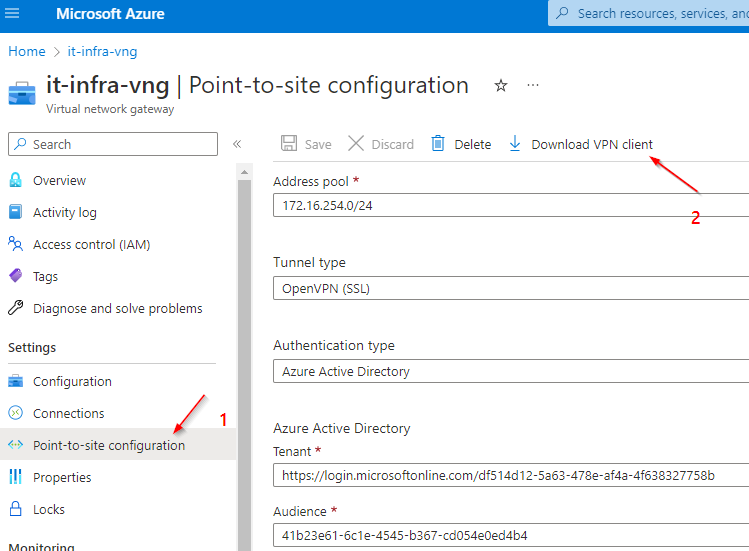
Setting Up the P2S - Configuration:
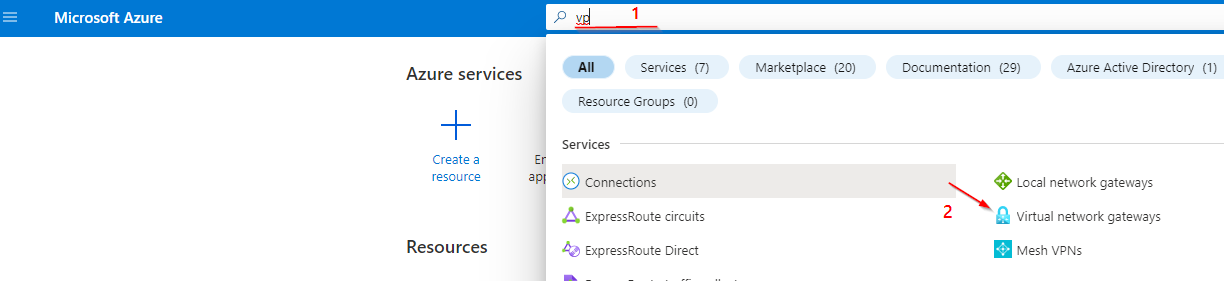
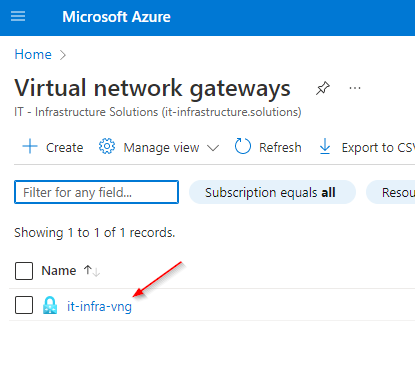
https://login.microsoftonline.com/<Tenant_ID>41b23e61-6c1e-4545-b367-cd054e0ed4b4
https://sts.windows.net/<Tenant_ID>/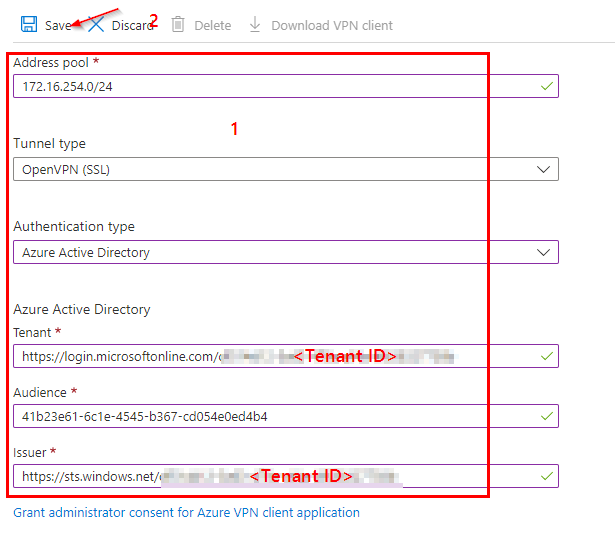
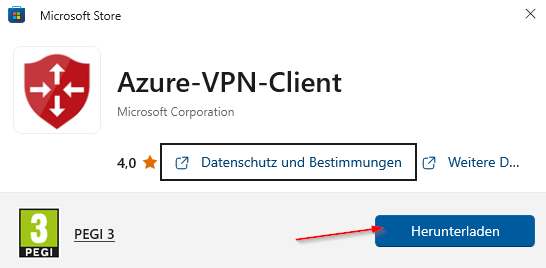
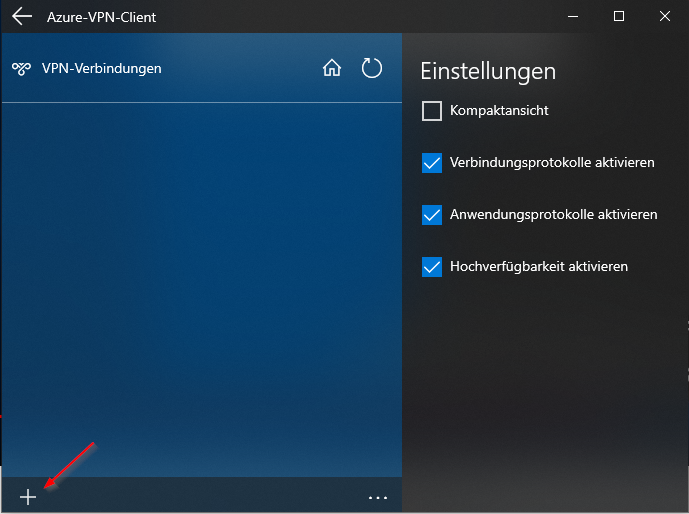
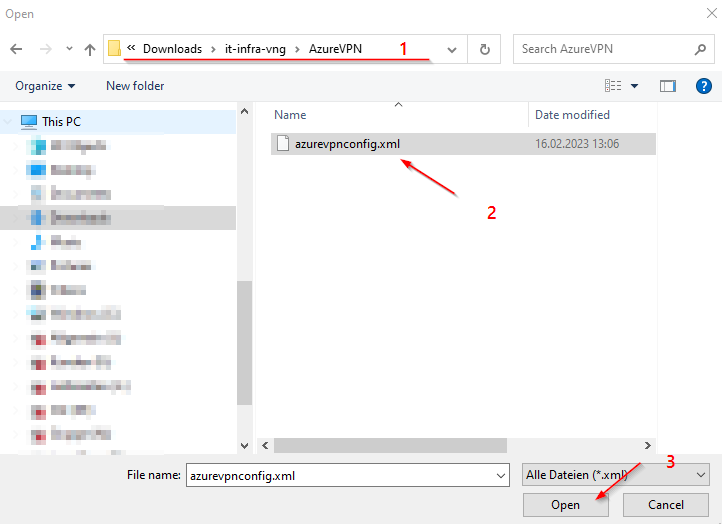
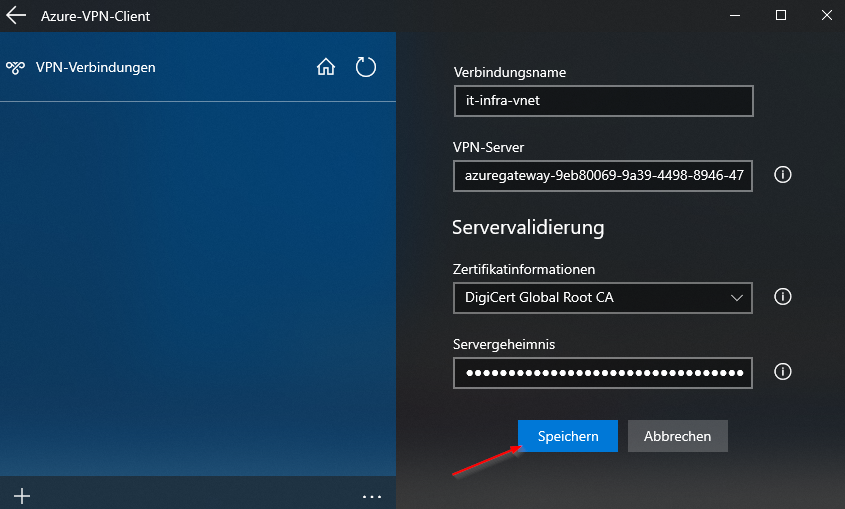
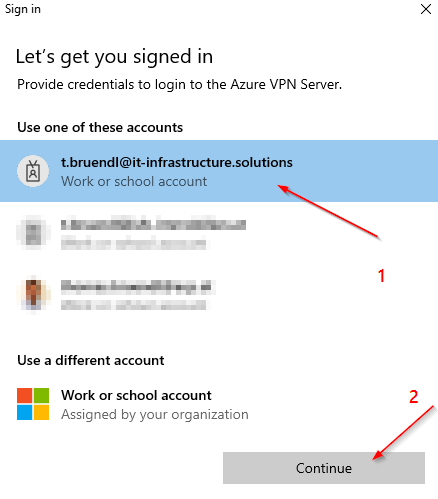
Configure Client:
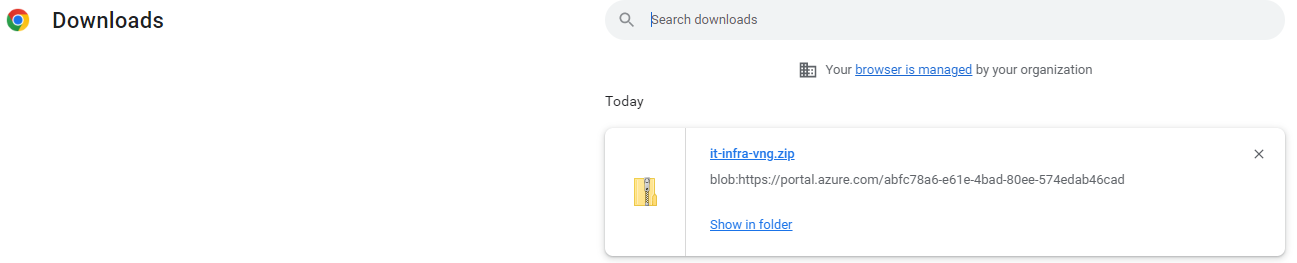
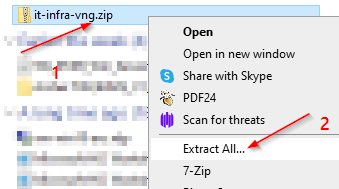
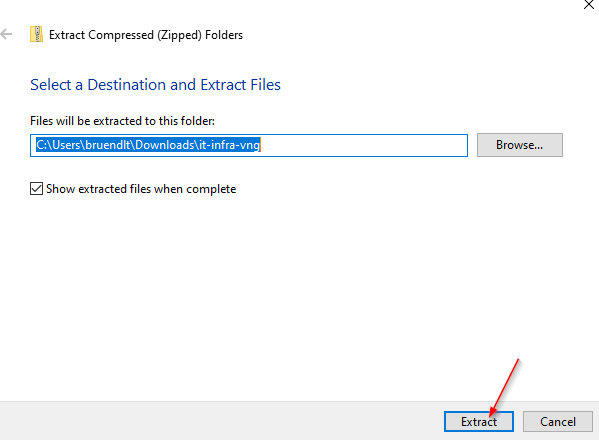
https://apps.microsoft.com/store/detail/9NP355QT2SQB?hl=en-us&gl=US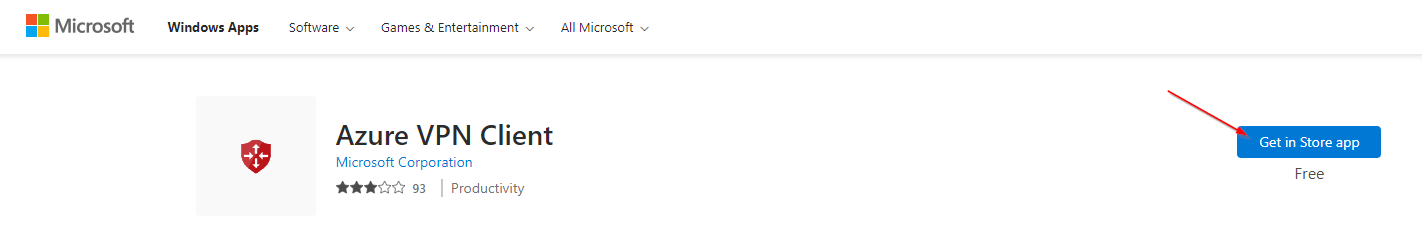
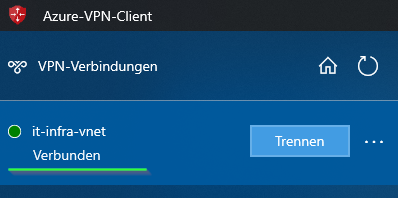
Setting Up MFA:
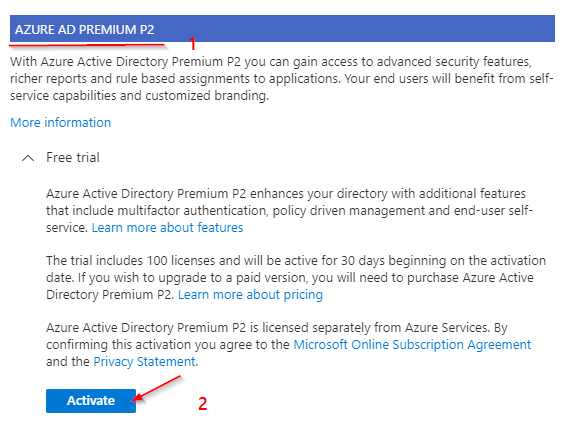

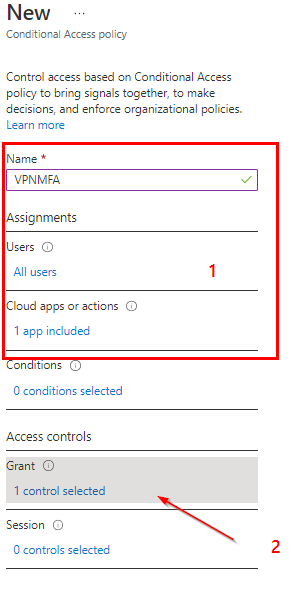
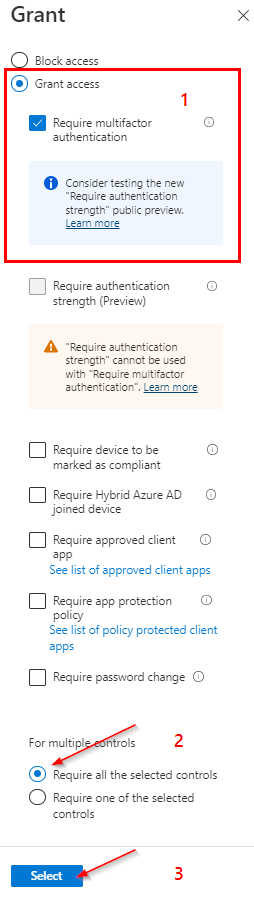
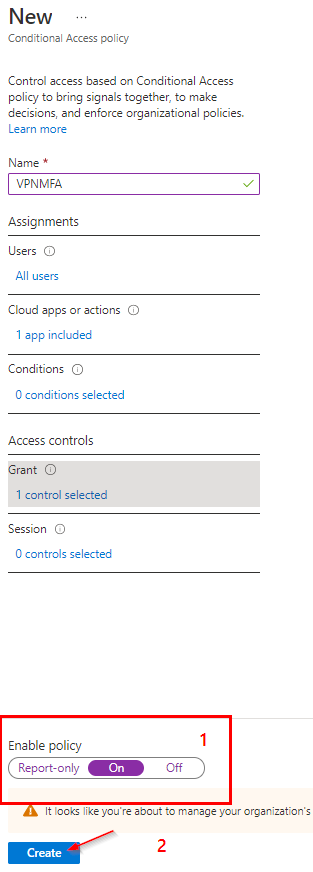
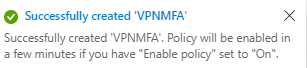
The Result:
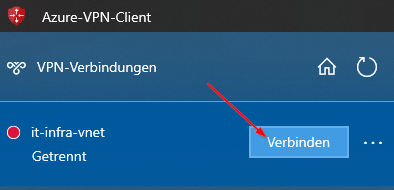
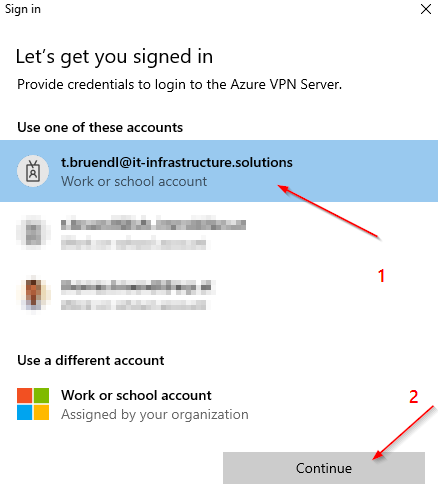
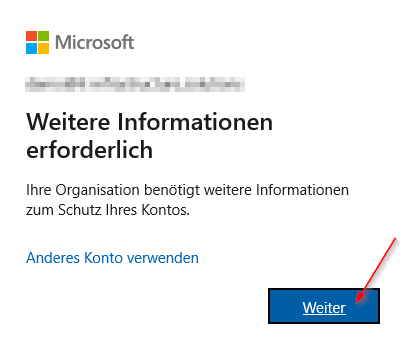
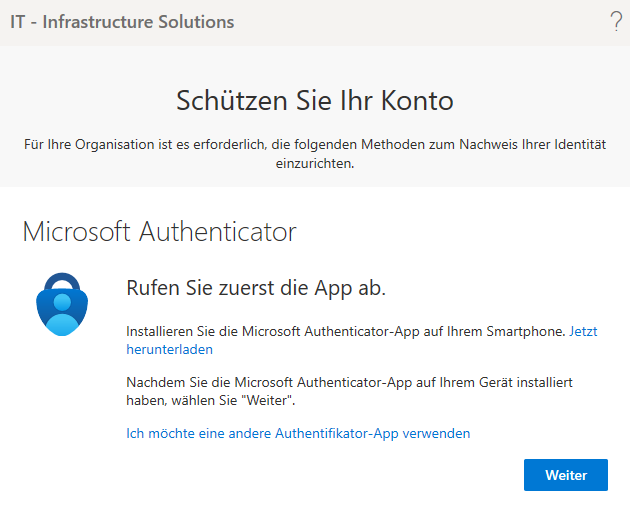
Additional Note:
In order to ensure that the name resolution works over the P2S connection, the Onprem DNS servers must be defined in the VNet where the Azure VPN gateway has been deployed.
References:
Azure AD tenant for User VPN connections: Azure AD authentication -OpenVPN - Azure Virtual WAN
You can use Azure Virtual WAN User VPN (point-to-site) to connect to your VNet using Azure AD authentication


