
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Prerequisites:
- Ressource Group
- V-Net / Sub-Net (including a gateway subnet)
- VM
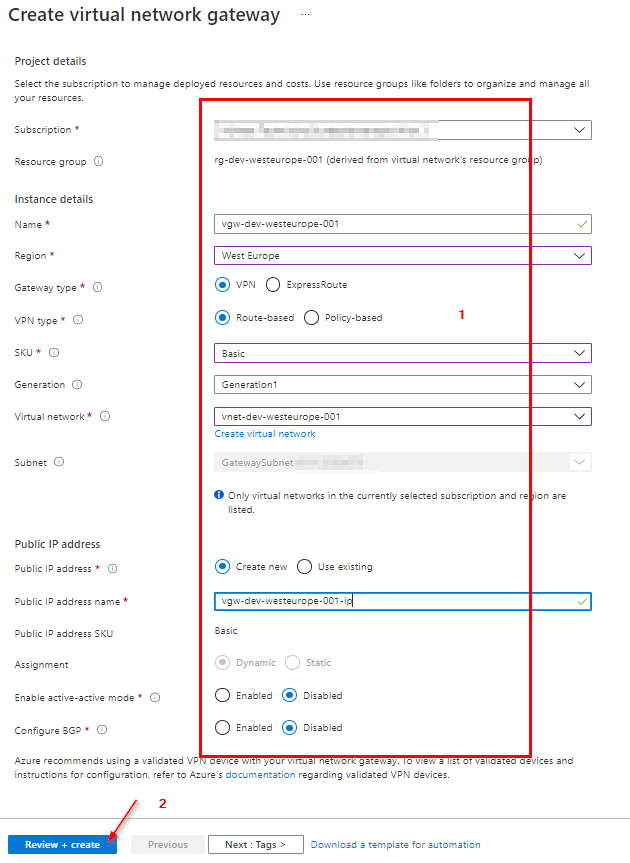
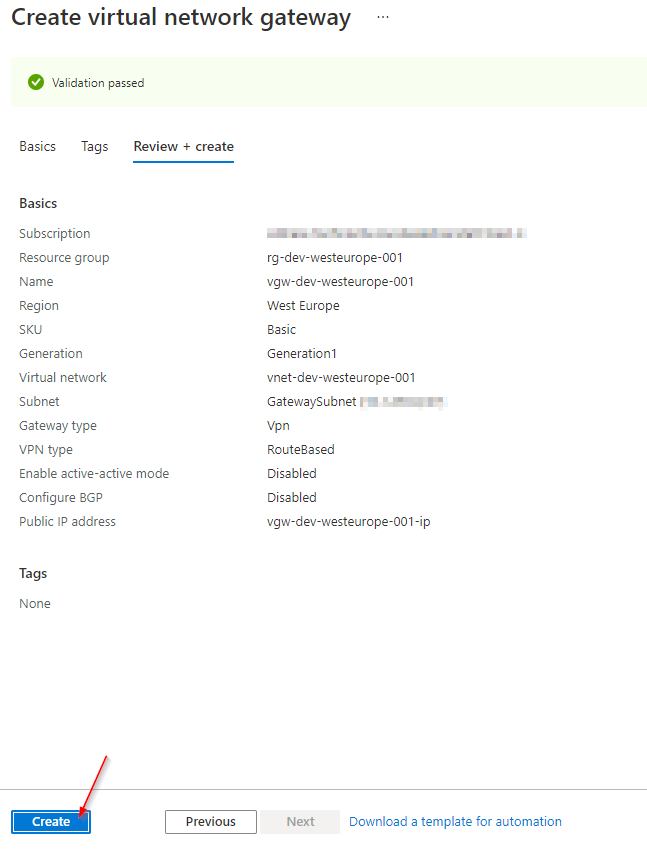
Create Virtual Network Gateway
Creating the needed Certs:
Root - Cert:
$cert = New-SelfSignedCertificate -Type Custom -KeySpec Signature `
-Subject "CN=<Some Value>" -KeyExportPolicy Exportable `
-HashAlgorithm sha256 -KeyLength 2048 `
-CertStoreLocation "Cert:\CurrentUser\My" -KeyUsageProperty Sign -KeyUsage CertSign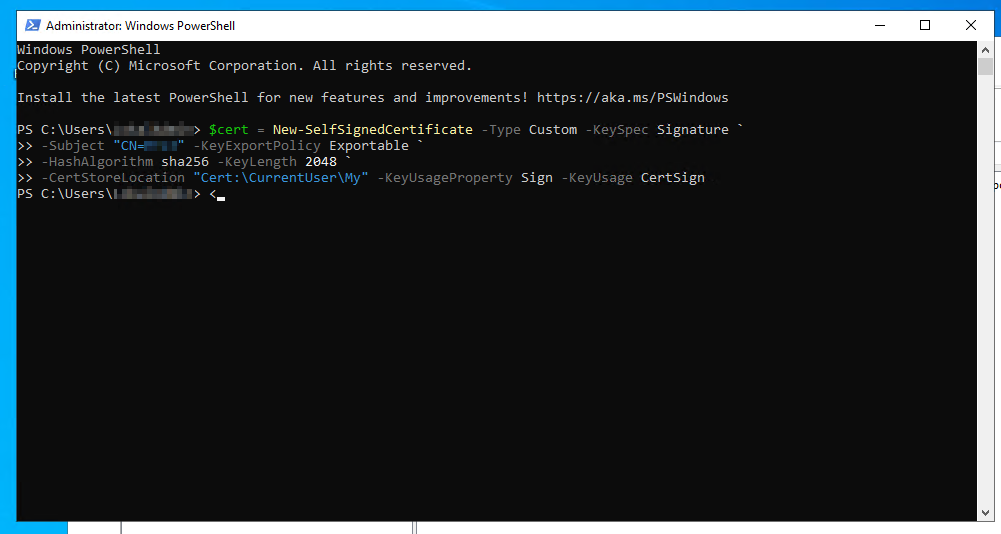
Client - Cert:
New-SelfSignedCertificate -Type Custom -DnsName <Some Value> -KeySpec Signature `
-Subject "CN=<Some Value>" -KeyExportPolicy Exportable `
-HashAlgorithm sha256 -KeyLength 2048 `
-CertStoreLocation "Cert:\CurrentUser\My" `
-Signer $cert -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.2")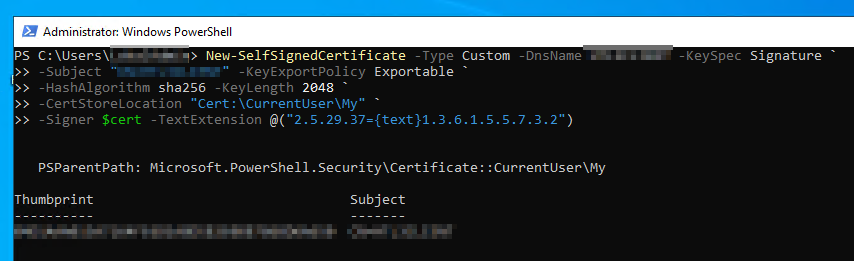
Export:
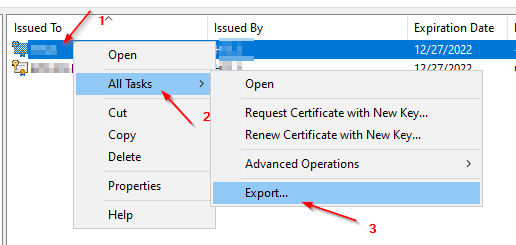
Client-Cert:
Root-Cert:
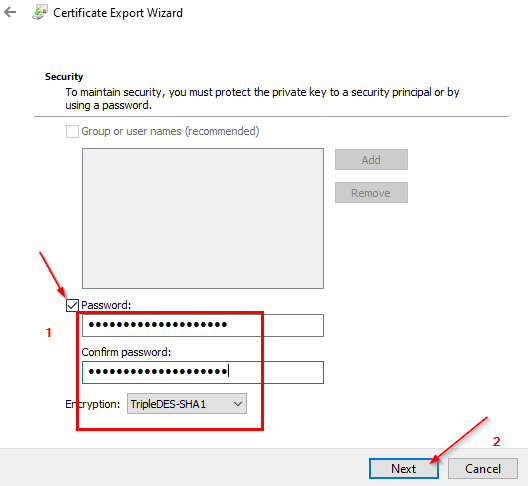

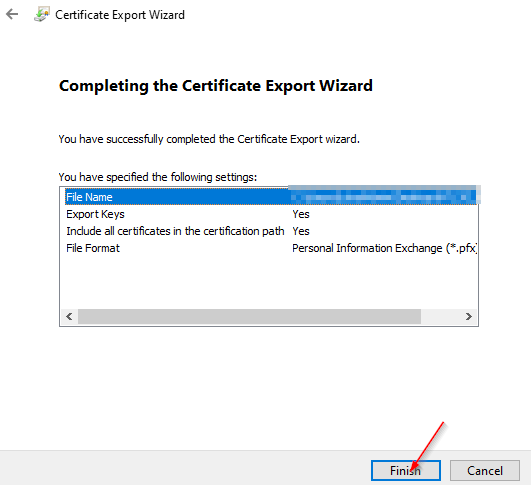

Note – Only root cert will use in Azure VPN, client certificate can install on other computers which need P2S connections.
PowerShell Way:
Get-ChildItem -Path Cert:\CurrentUser\My\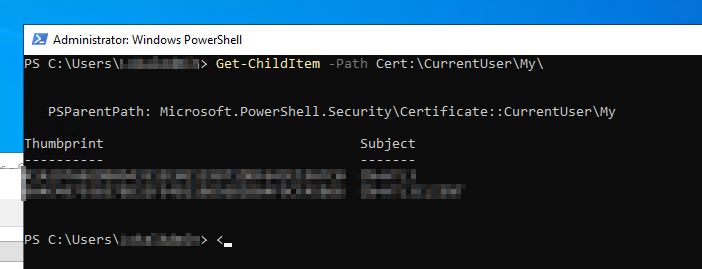
$password= "<Password>" | ConvertTo-SecureString -AsPlainText -Force
Get-Item -Path Cert:\CurrentUser\My\<Thumbprint> | Export-PfxCertificate -FilePath "<Path>" -Password $password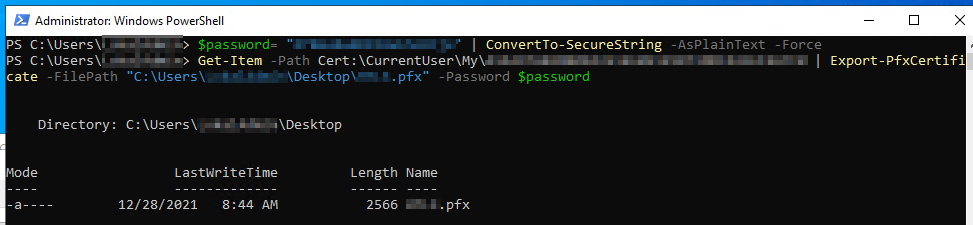
Get-Item -Path Cert:\CurrentUser\My\<Thumbprint> | Export-Certificate -Type CERT -FilePath "<Path>"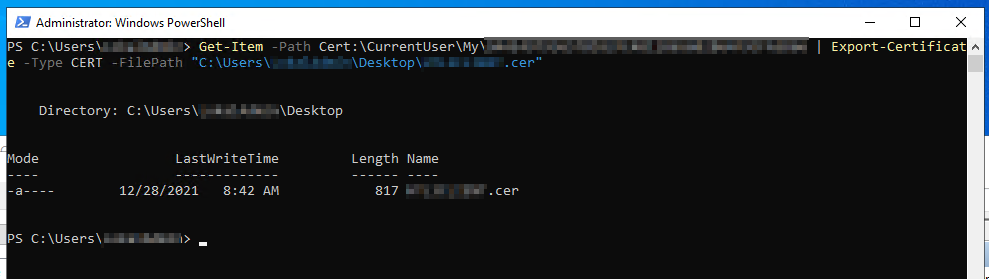
Note – Only root cert will use in Azure VPN, client certificate can install on other computers which need P2S connections.
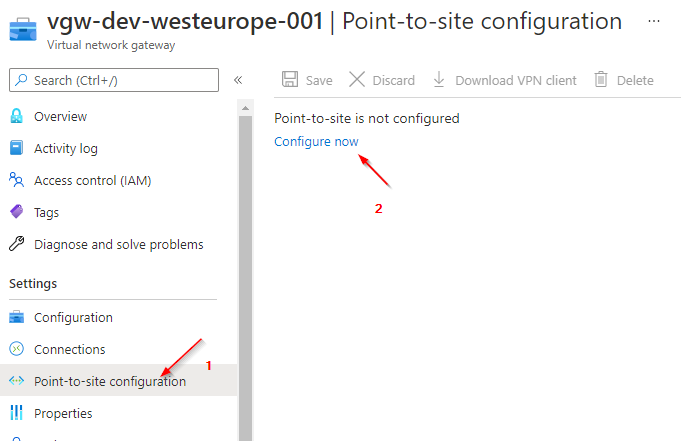
Configure Point-to-Site Connection
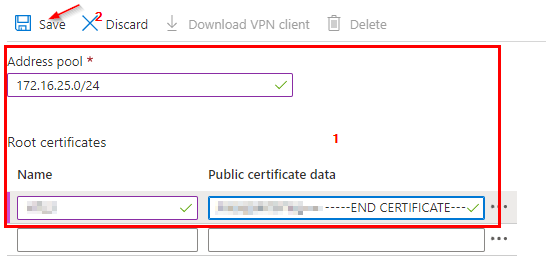
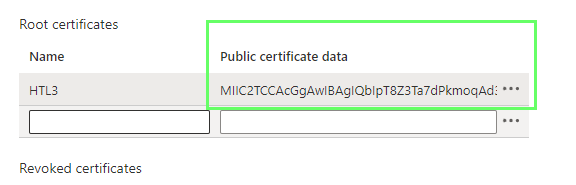
Note : when you paste certificate data, do not copy -----BEGIN CERTIFICATE----- & -----END CERTIFICATE----- text.
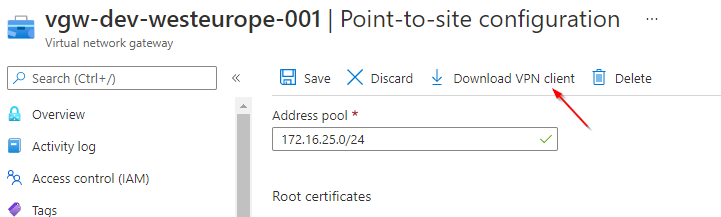
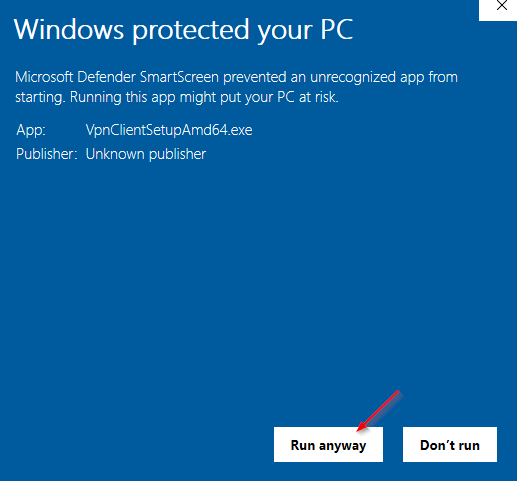
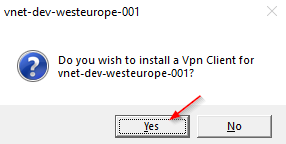
Note : Azure VPN Client require full (local) admin rights
Tutorial: Erstellen und Verwalten eines VPN-Gateways – Azure-Portal - Azure VPN Gateway
In diesem Tutorial erfahren Sie, wie Sie mithilfe des Portals ein Azure-VPN-Gateway erstellen, bereitstellen und verwalten.

Herstellen einer Verbindung mit einem VNet unter Verwendung eines Point-to-Site-VPN und der Zertifikatauthentifizierung: Portal - Azure VPN Gateway
Erfahren Sie, wie Sie Windows-, macOS- und Linux-Clients anhand von VPN Gateway Point-to-Site-Verbindungen und selbstsignierten oder von einer CA ausgestellten Zertifikaten sicher mit einem VNet verbinden.

Step-By-Step: Creating an Azure Point-to-Site VPN
Site-to-Site VPN is the most common method organizations use to connect on-premises network to Azure vNet. This VPN connection is initiated in your edge firewall or router level. But what if you connecting from remote location such as home? We can use point-to-site method to do that. In this method …


