
This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
1) Trust WAC by supported Browsers
Supported Browsers: Chrome, Edge....
Add the WAC FQDN <https://Hostname Windows Admin Center> to the "Trusted Local Intranet Zone" under Internet Properties.
Click Start and type "inetcpl.cpl" to open the required GUI.
2) Setting Kerberos Contrained Delegation
Var1:
# Variant 1:
##########################################
# Add and import AD PowerShell
Add-WindowsFeature RSAT-AD-PowerShell
Import-Module ActiveDirectory
# Host name of Windows Admin Center
$wac = "<Hostname Windows Admin Center>"
# Server names and Cluster names that you want to manage with Windows Admin Center in your domain
# $servers = "<Server1>", "<Server2>", "<Server3>", "<CLUSTER1>"
# Get the identity object of Windows Admin Center (WAC)
$wacobject = Get-ADComputer -Identity $WAC
# Set the resource-based kerberos constrained delegation for each node
foreach ($server in $servers){
$computerObject = Get-ADComputer -Identity $server
Set-ADComputer -Identity $computerObject -PrincipalsAllowedToDelegateToAccount $wacobject -verbose
}# Clearing KDC Cache
Invoke-Command -ComputerName $servers -ScriptBlock {
klist purge -li 0x3e7
}Var2:
# Variant 2
##########################################
$GatewayServerName="<Hostname Windows Admin Center>"
#Configure Resource-Based constrained delegation
$gatewayObject = Get-ADComputer -Identity $GatewayServerName
$computers = (Get-ADComputer -Filter {OperatingSystem -eq "Azure Stack HCI"}).Name
foreach ($computer in $computers){
$computerObject = Get-ADComputer -Identity $computer
Set-ADComputer -Identity $computerObject -PrincipalsAllowedToDelegateToAccount $gatewayObject
}# Clearing KDC Cache
Invoke-Command -ComputerName $servers -ScriptBlock {
klist purge -li 0x3e7
}Var3:
# Variant 3
##########################################
$GatewayServerName="<Hostname Windows Admin Center>"
#Configure Resource-Based constrained delegation
$gatewayObject = Get-ADComputer -Identity $GatewayServerName
$computers = (Get-ADComputer -Filter 'Description -like "Node" -or Description -like "Cluster"').Name
foreach ($computer in $computers){
$computerObject = Get-ADComputer -Identity $computer
Set-ADComputer -Identity $computerObject -PrincipalsAllowedToDelegateToAccount $gatewayObject
}
# Check the value of the attribute directly
#foreach ($computer in $computers){
#$x = Get-ADComputer -Identity $computerObject -Properties msDS-AllowedToActOnBehalfOfOtherIdentity
#$x.'msDS-AllowedToActOnBehalfOfOtherIdentity'.Access
#}
foreach ($computer in $computers){
Set-ADComputer -Identity (Get-ADComputer -Identity $computer) -PrincipalsAllowedToDelegateToAccount $gatewayObject
}
foreach ($computer in $computers){
$computerObject = Get-ADComputer -Identity $computer
Write-Host $computerObject.Name":"
Get-ADComputer $computerObject.Name -Properties * | Format-List -Property *delegat*,msDS-AllowedToActOnBehalfOfOtherIdentity
}
# Clearing KDC Cache
foreach ($computer in $computers){
Invoke-Command -ComputerName $computerObject.Name -ScriptBlock {
klist purge -li 0x3e7
}
}To Avoid WINRM - Problems in WAC:
# On each Cluster Node:
Disable-WsmanCredSSP -Role Server
Enable-WSManCredSSP -Role Server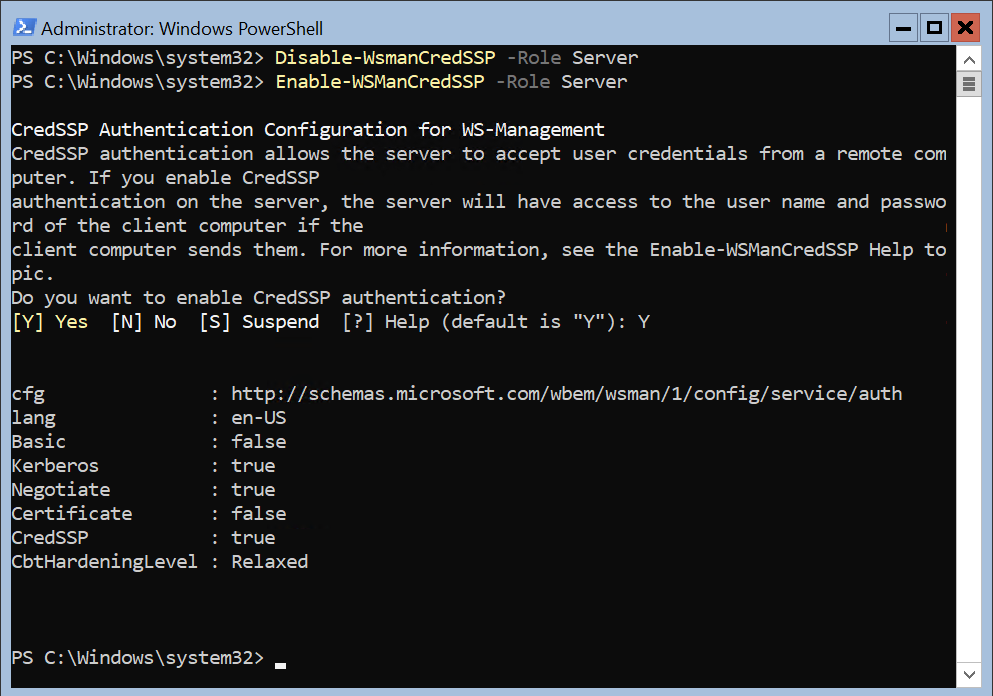
# On the WAC-Server
Enable-WSManCredSSP -Role client -DelegateComputer <Cluster Node X Hostname>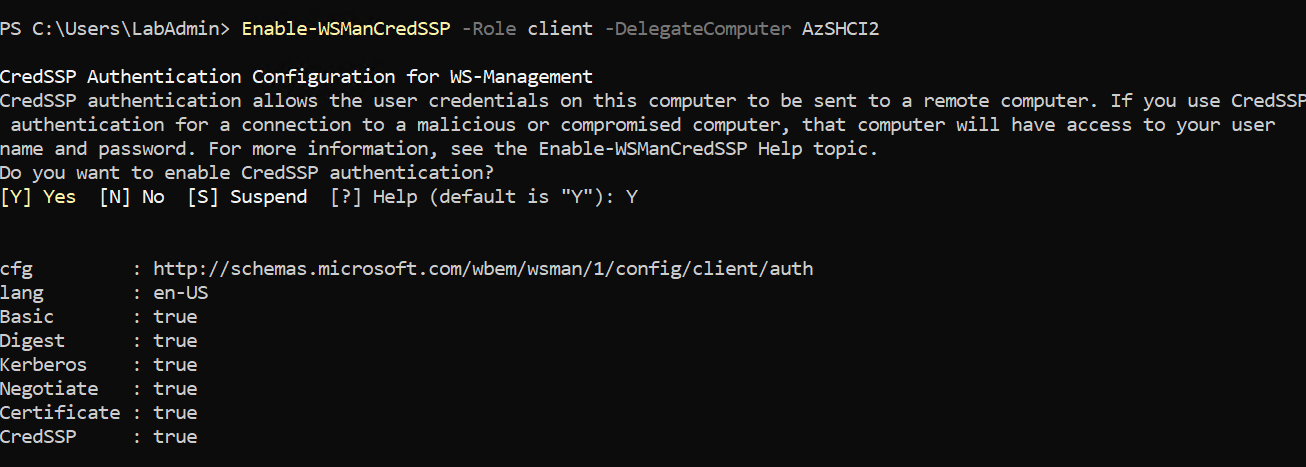
# On the WAC-Server
# Disable Firewall for Remote Management
netsh advfirewall set allprofiles state off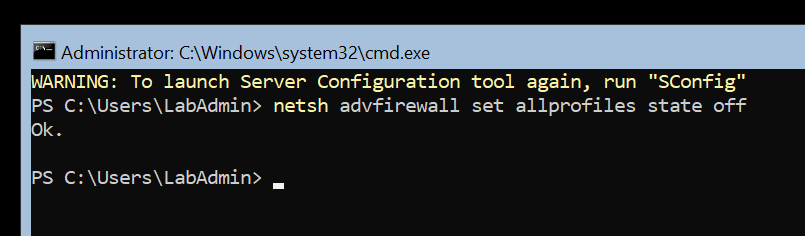
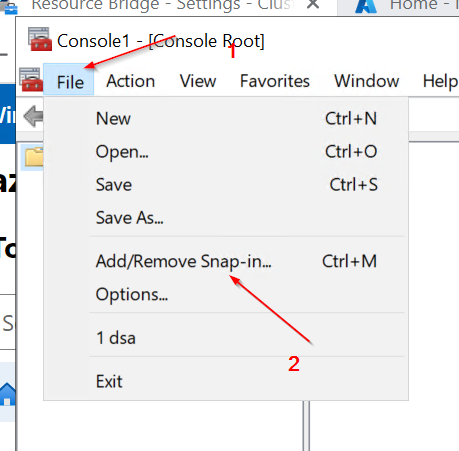
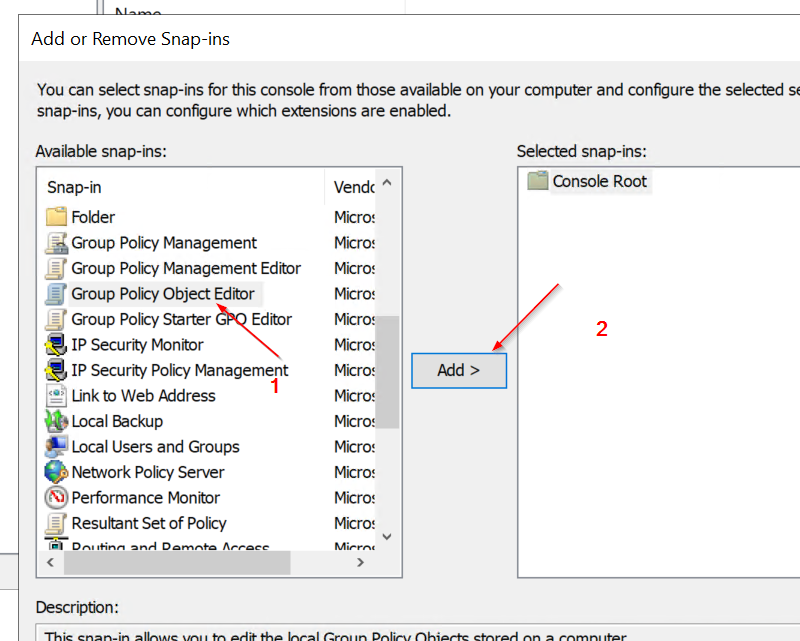
Open gpedit.msc (on DC VM) and go to Local Computer Policy -> Computer Configuration -> Administrative Templates -> System -> Credentials Delegation.
- Enable Allow delegating fresh credentials and set value "wsman/<Cluster Node X Hostname>"
- Enable Allow delegating fresh credentials with NTLM-only server authentication and set value "wsman/<Cluster Node X HostName>"
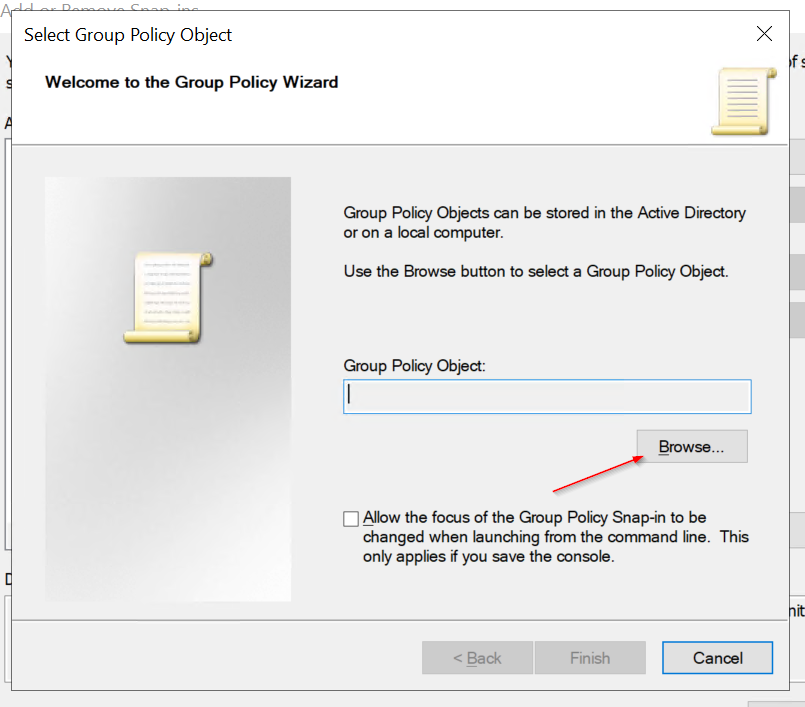
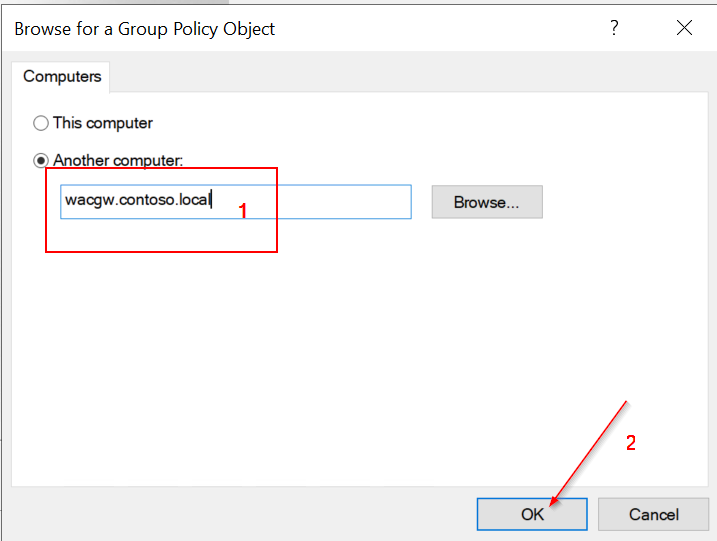
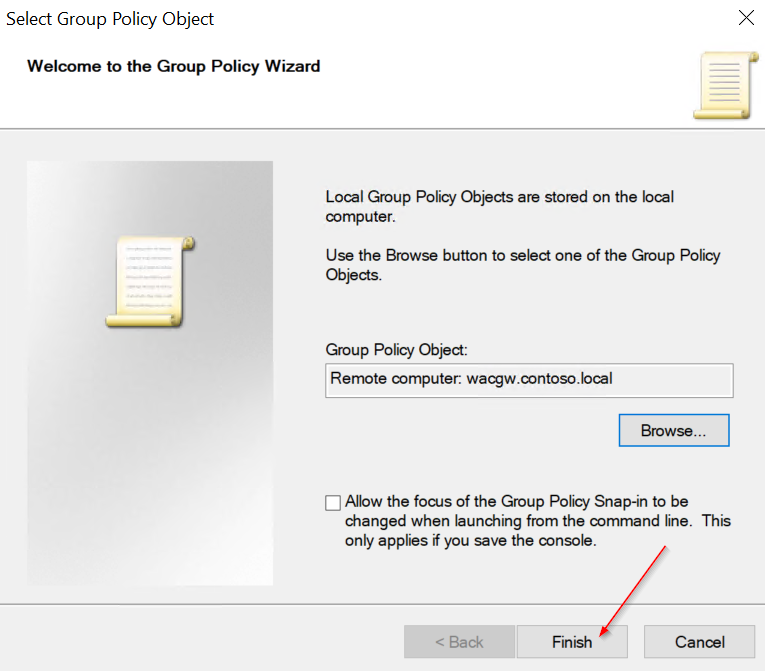
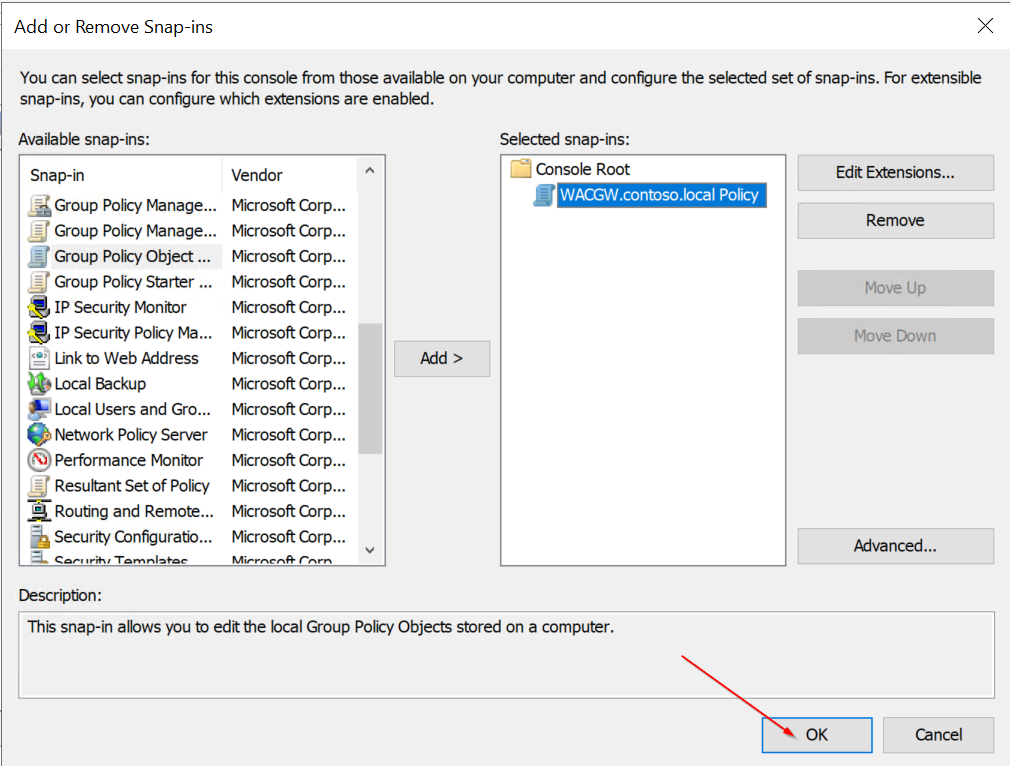
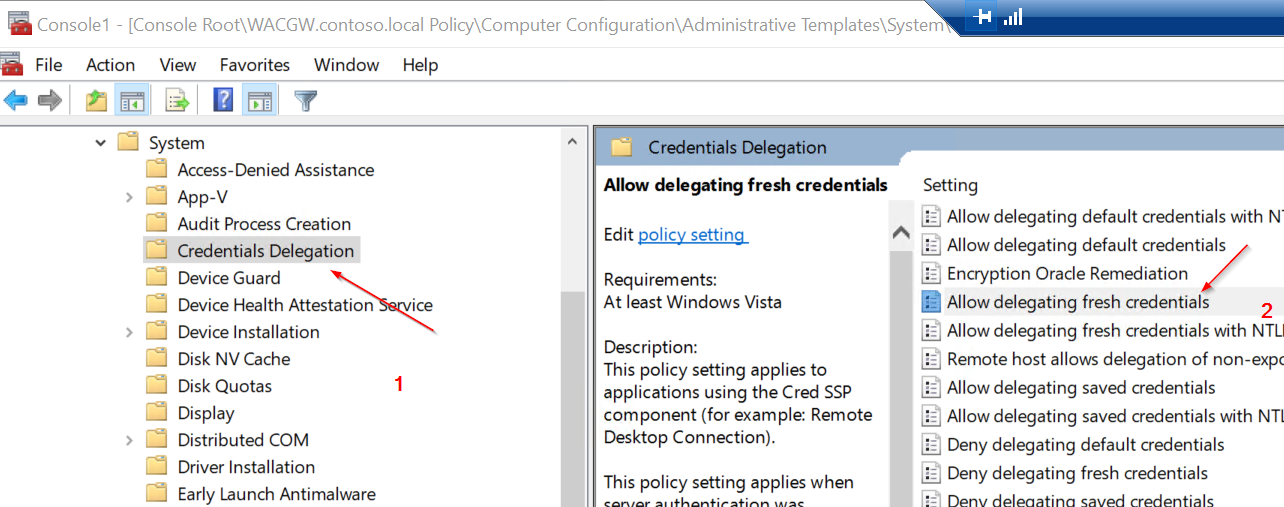
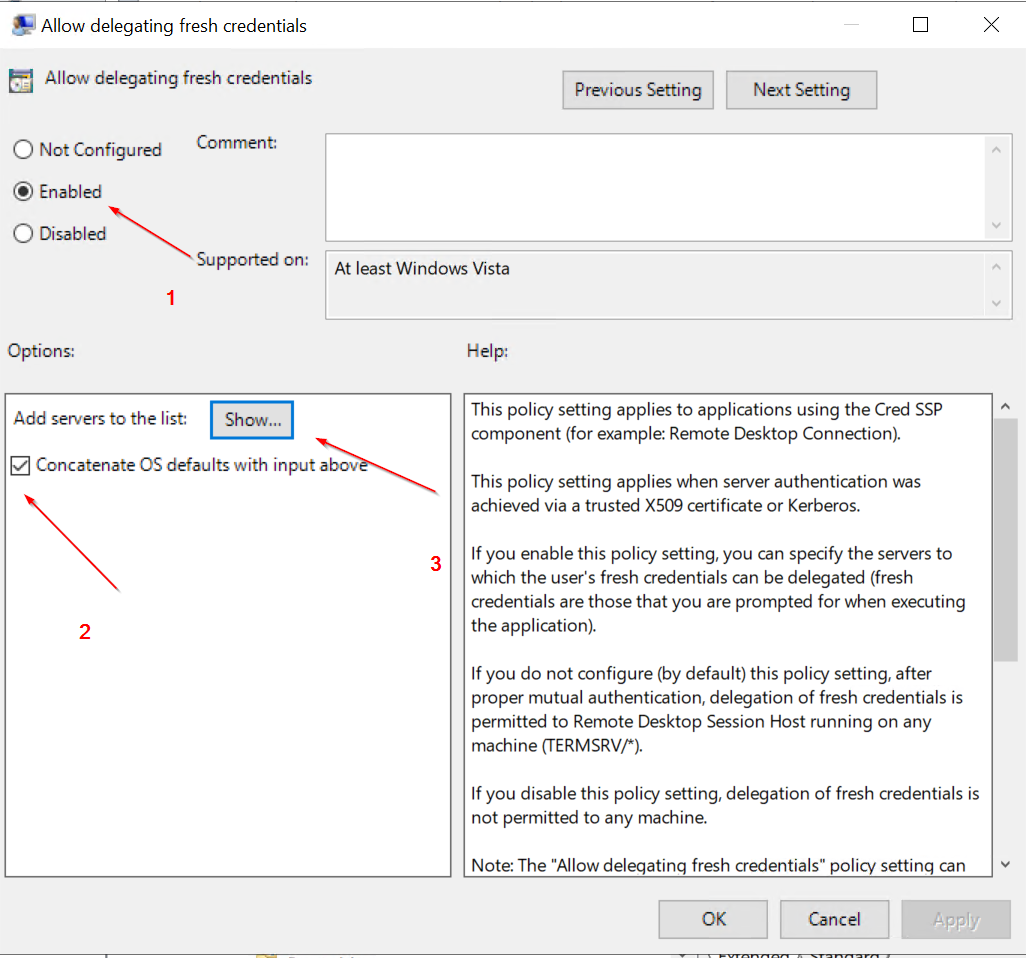
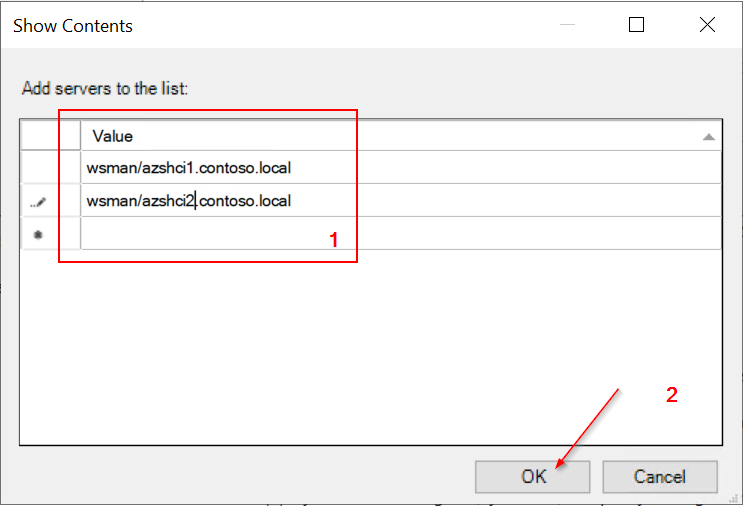
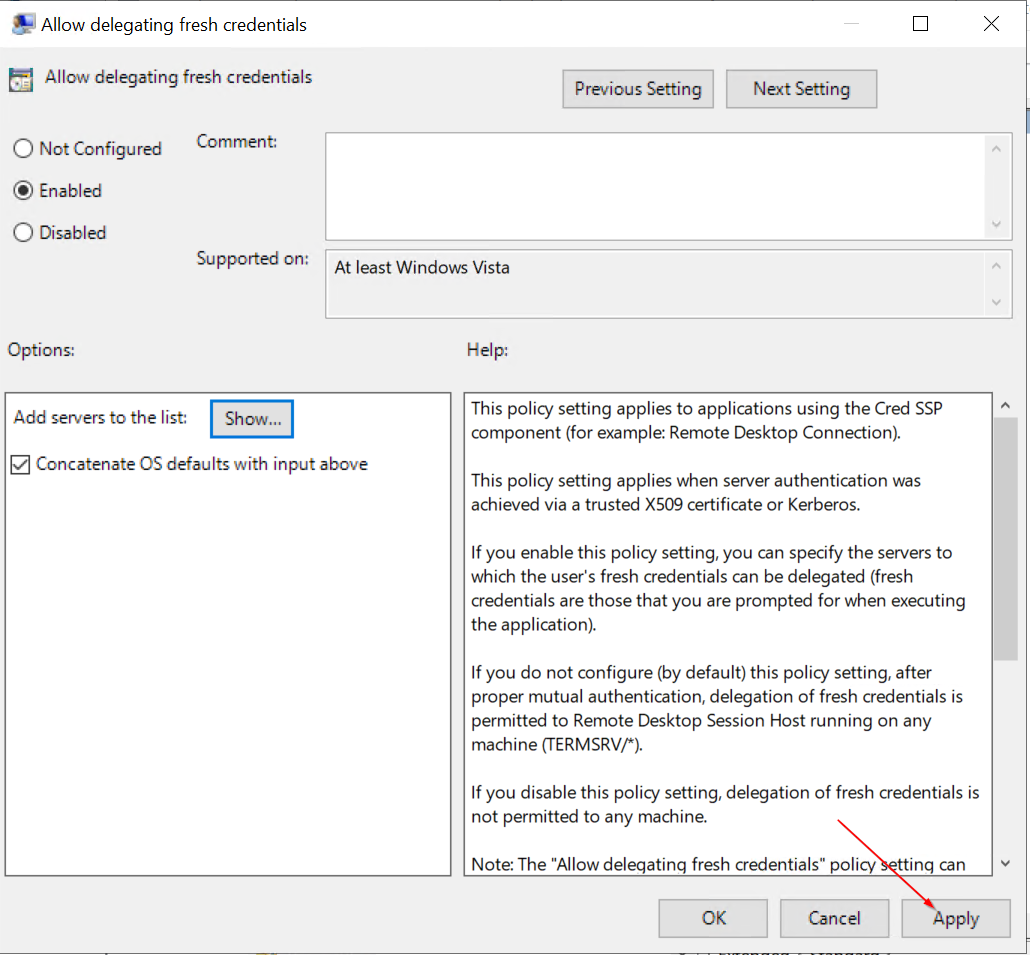
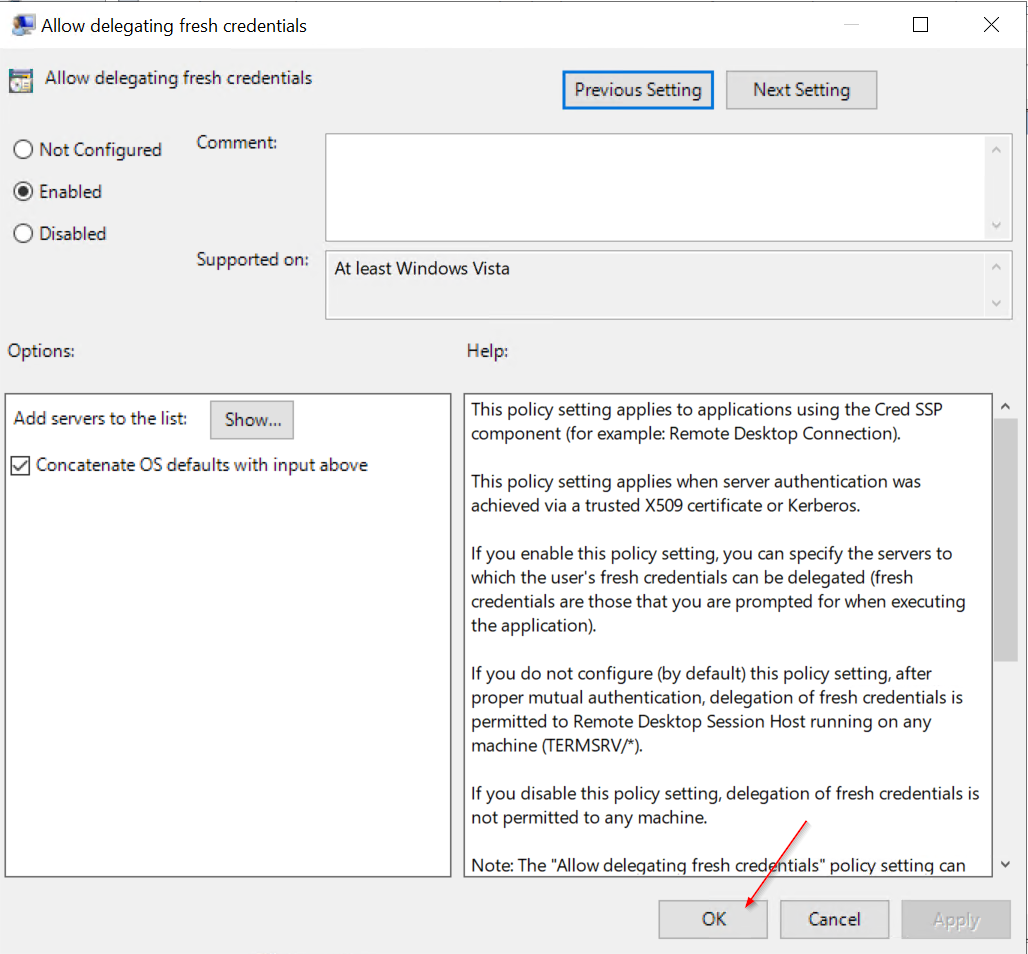
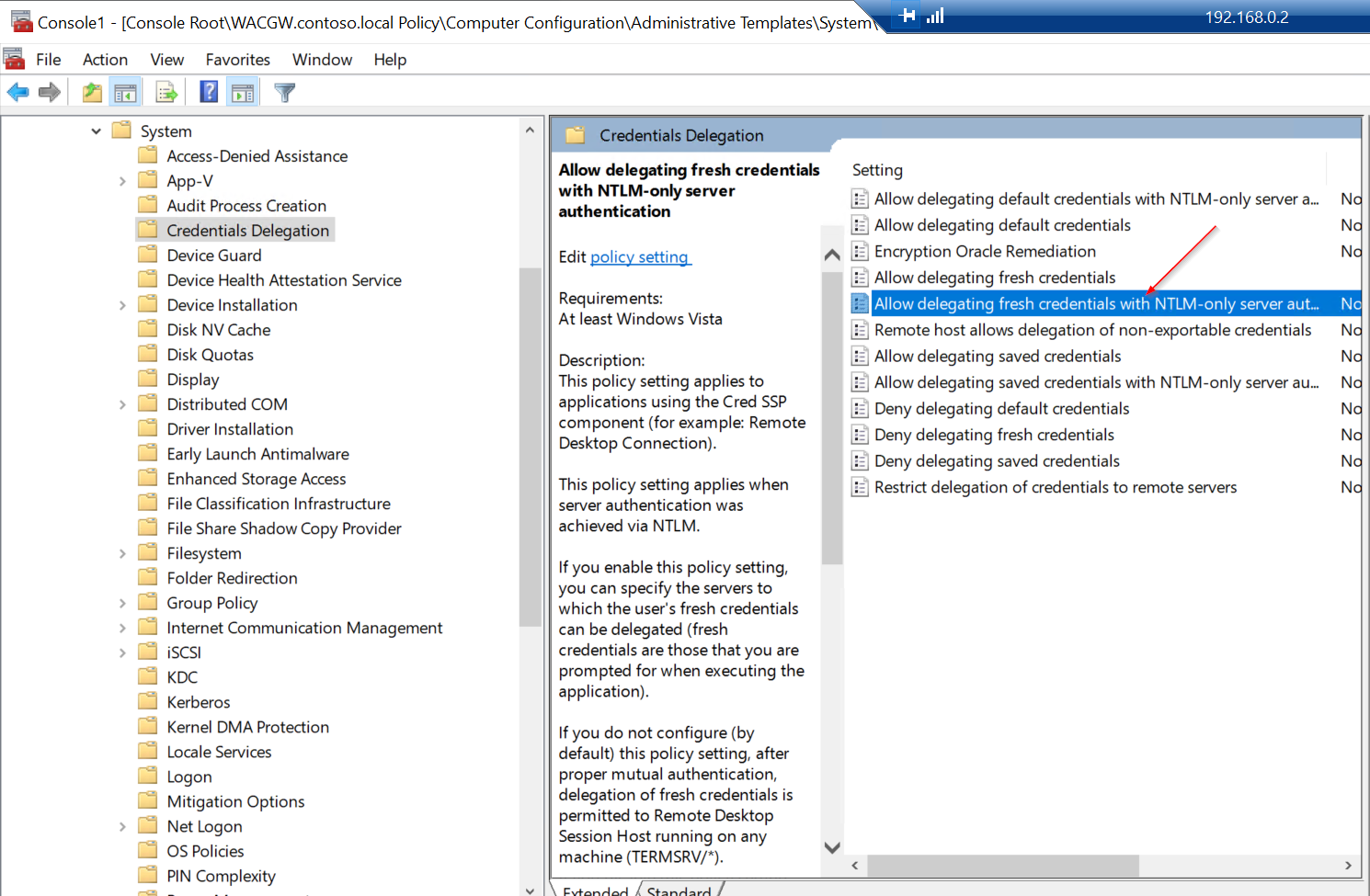
Clone Settings from "Enable Allow delegating fresh credentials"
# On the WAC-Server
# Disable Firewall for Remote Management
netsh advfirewall set allprofiles state on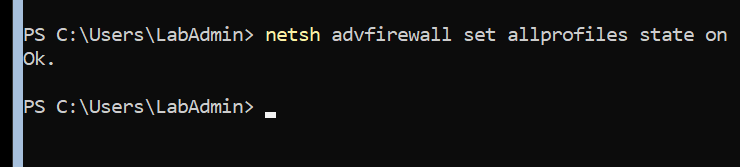
Test - Settings
# On the WAC - Server
$testSession= New-PSSession -ComputerName <Cluster Node X HostName> -Authentication Credssp -Credential (Get-Credential)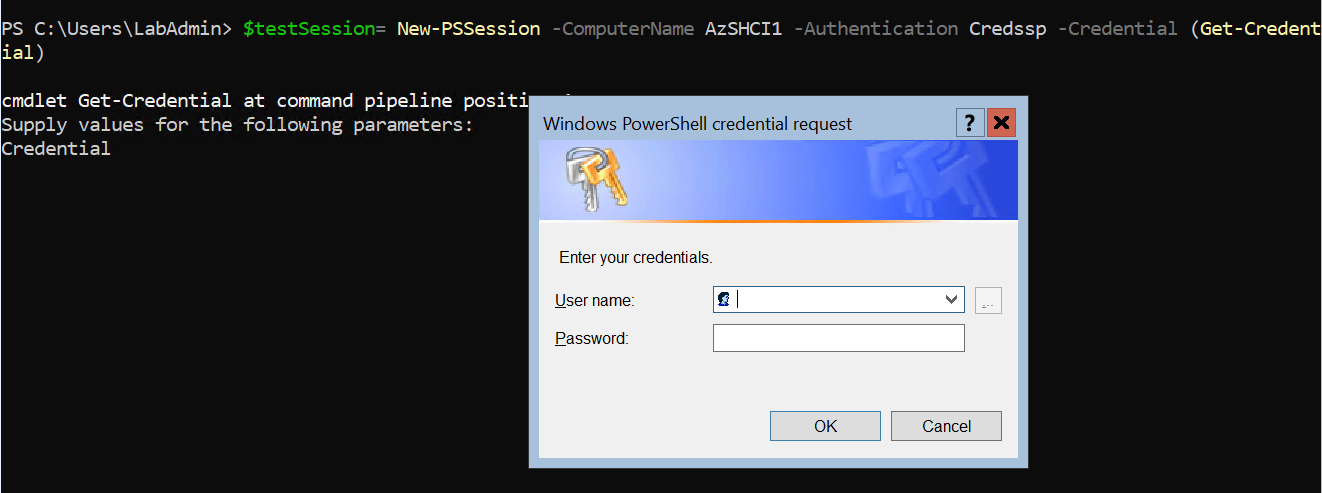
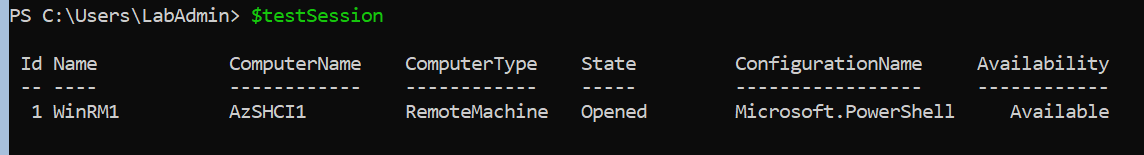
Remove-PSSession $testSession

References:
https://rdr-it.com/en/admin-center-configure-sso-with-a-gateway-configuration/
Getting Started with Azure Stack HCI
How To Enable Single Sign-On (SSO) For Windows Admin Center - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity
Check how to prepare and pass the Official CCSP Exam — Certified Cloud Security Professional by (ISC)² successfully. CCSP Exam Study Guide: https://nemnom.ch/69o

Windows Admin Center: configure Single Sign-On


