This article has not been completed yet. However, it may already contain helpful Information and therefore it has been published at this stage.
Prerequesites
- An Azure Tenant with Global Administrator Permissions
- An Azure Arc enabled Server
Assigning a tag to a resource
In this first step we will tag a random resource. In this case, I chose an Azure Arc enabled server because I want to continue using this setup for another project. Let's go.

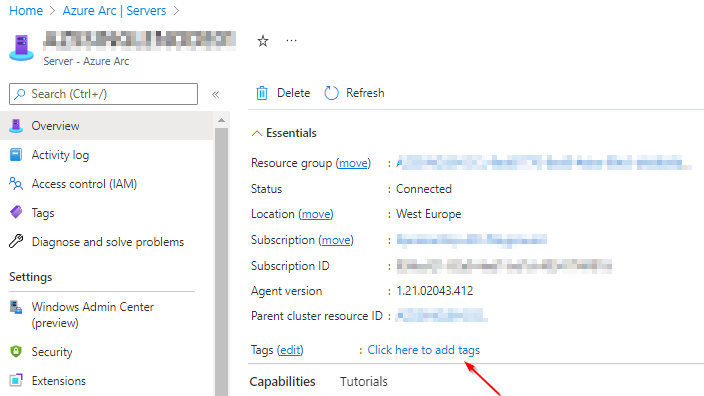
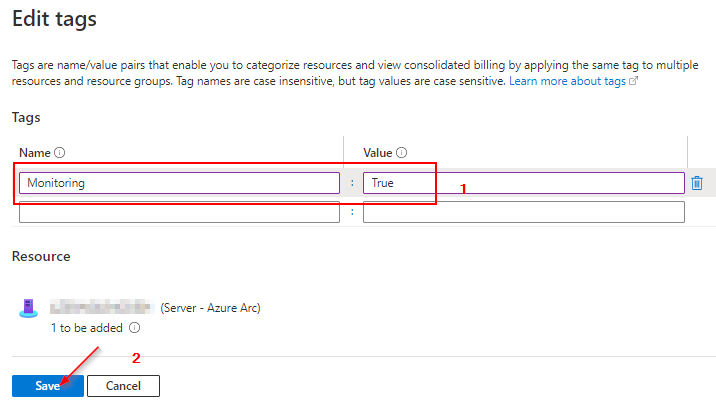
Designing the Ressource Graph Query
Now that we have a tagged resource, I want to be able to search for it via KQL. So the question is, what will this query look like with this goal in mind?

Below you will find the ready-made query that I created. If you want to learn more about KQL you can consult one of my other blog posts here.
https://it-infrastructure.solutions/kql-kusto-quick-start-guide-azure/
resources
| where type == "microsoft.hybridcompute/machines"
| extend tagKey = tostring(bag_keys(tags)[0])
| extend tagValue = tostring(tags[tagKey])
| project name, tags, tagKey, tagValue
| where tagKey == "Monitoring"
| where tagValue == "True"
# Comment
# | where type == "microsoft.hybridcompute/machines" = Filters for Arc Enabled Machines
# | extend tagKey = tostring(bag_keys(tags)[0]) = Conversion from JSON - Data to Plaintext
# | extend tagValue = tostring(tags[tagKey]) = Conversion from JSON - Data to Plaintext
# | project name, tags, tagKey, tagValue = Creating a Table to display the Results
# | where tagKey == "Monitoring" = Filter for the Tag Keys
# | where tagValue == "True" = Filter for the Tag Values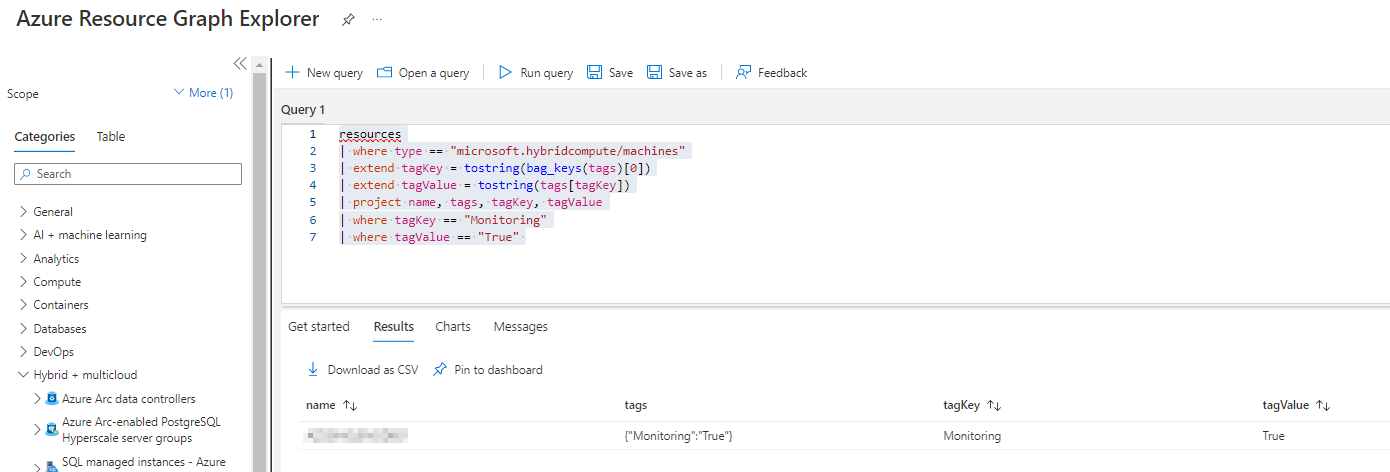
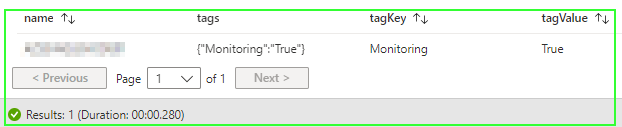
Expected Result:
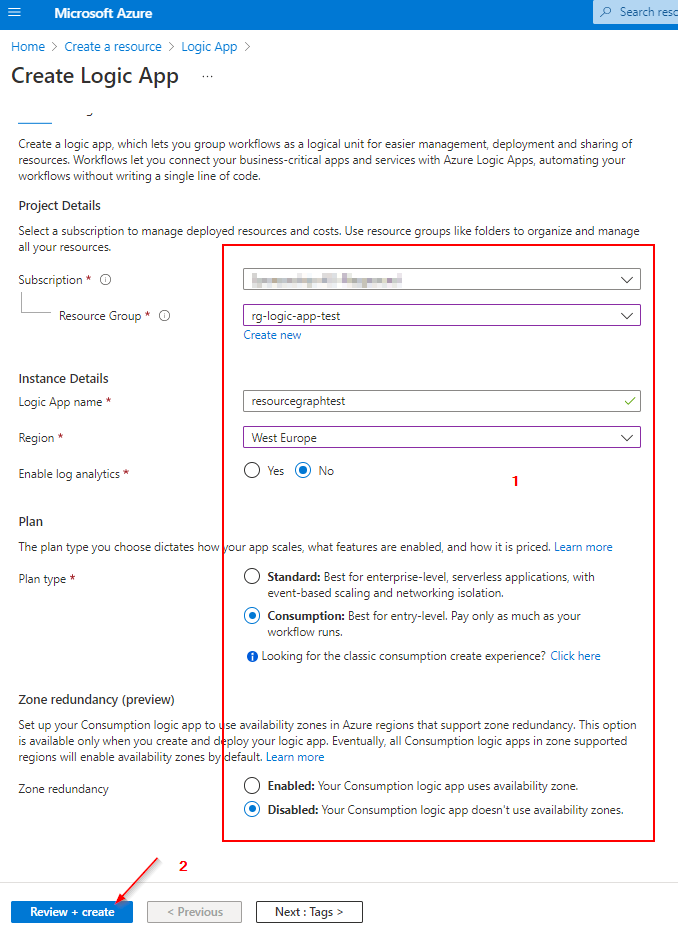
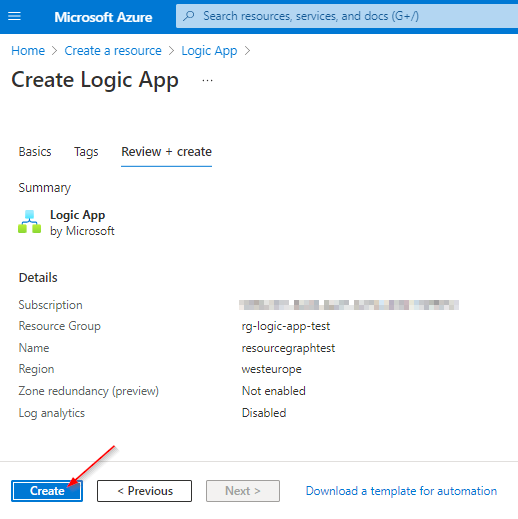
Creating the Logic App

Editing the Logic App
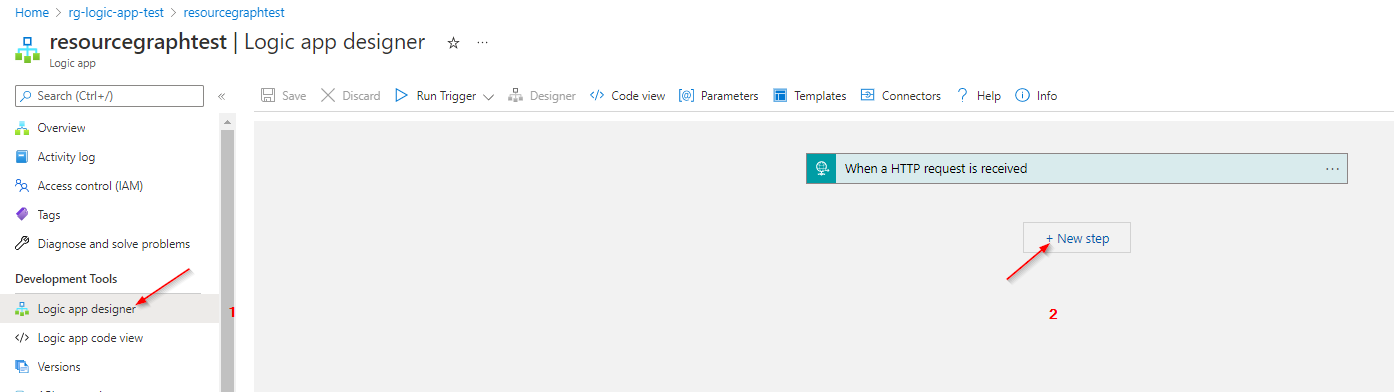
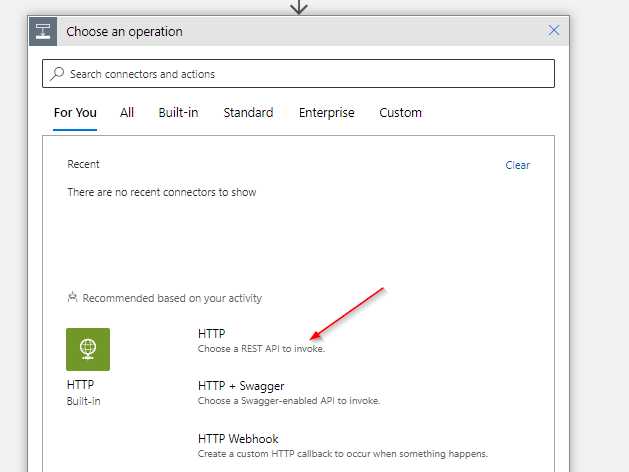
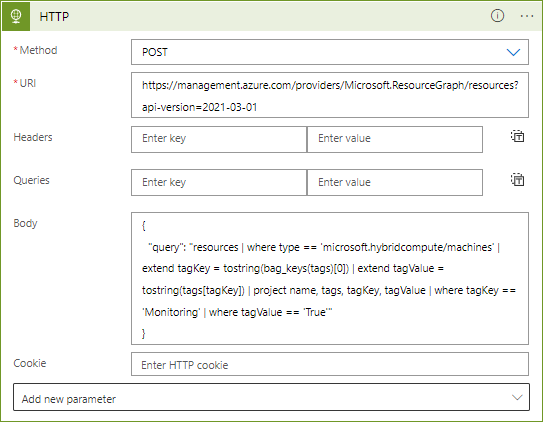
Below you can find the parameters I prepared and applied.
# Method
POST
# URI
https://management.azure.com/providers/Microsoft.ResourceGraph/resources?api-version=2021-03-01
# Body
{
"query": "resources | where type == 'microsoft.hybridcompute/machines' | extend tagKey = tostring(bag_keys(tags)[0]) | extend tagValue = tostring(tags[tagKey]) | project name, tags, tagKey, tagValue | where tagKey == 'Monitoring' | where tagValue == 'True'"
}
At this point it is advisable to save the progress made so far.
Performing a first test run
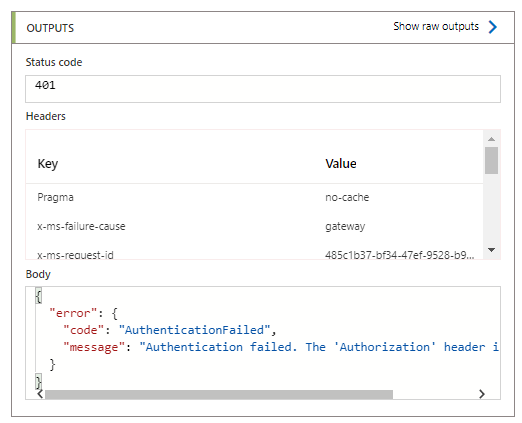
So after trying to send the query to the Resource Graph Explorer's Rest API via a Logic app, we notice that apparently some permissions are missing.
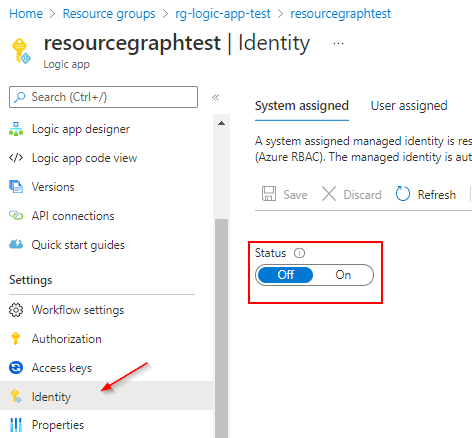
Creating a Logic App Identity
In order to provide an identity to which we can assign some privileges, we activate a so called System Assigned Managed Identity.

Assigning the required permissions
Now you need to assign the necessary permissions to the identity you have just created.
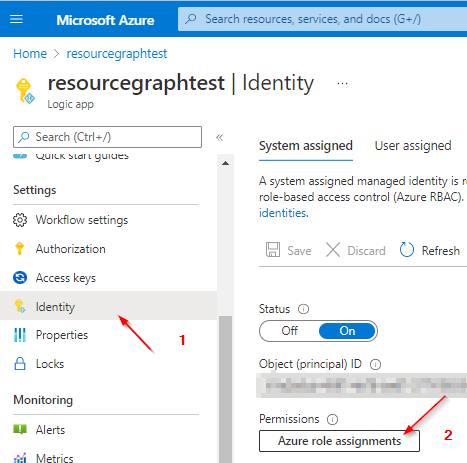

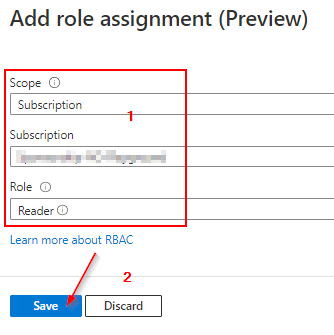
Reader - Permissions on subscription level should be sufficient.
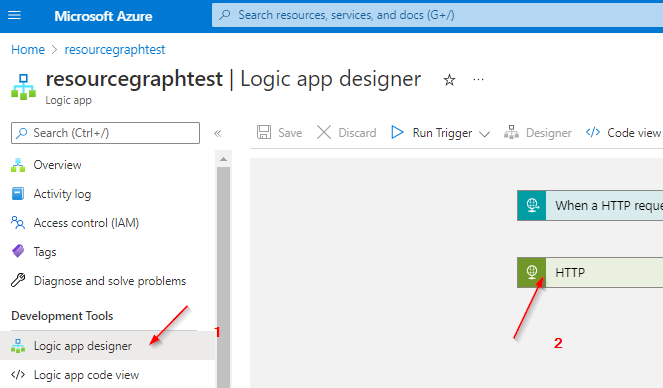
Editing the Logic App for 2nd Time
Now we have to teach our Logic app to use the newly assigned privileges. To do this, we edit the app again and add some authentication properties.
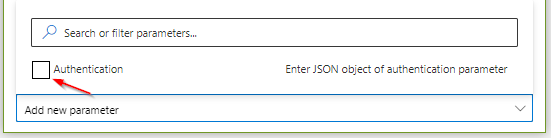
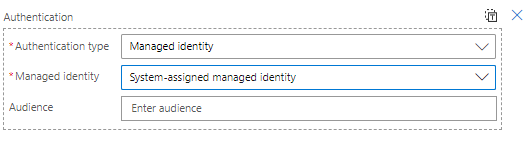
For sure, you have to save the changes to the application again.
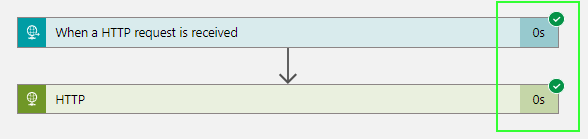
Performing a second and final test run

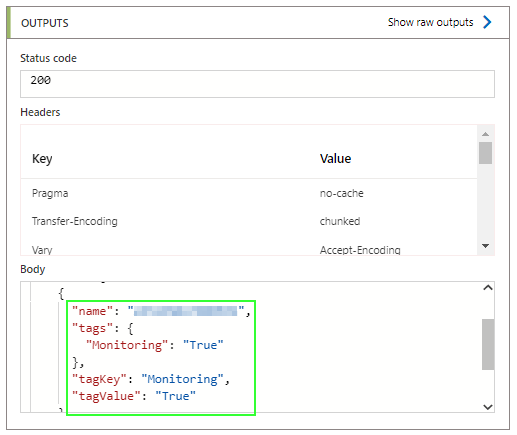
Expected Result:
References: