Prerequisites:
Installation (serverside):
# Installation via Choco
choco install openssh -y -f
# Neustart
Restart-Computer -Force
# Check Version
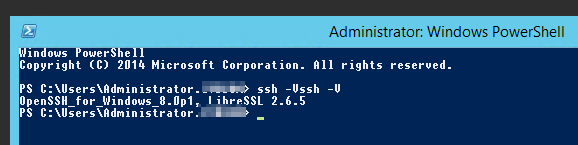
ssh -Vssh -V
# Change folder
cd "C:\Program Files\OpenSSH-Win64"
# Running Installation & Setup-Script
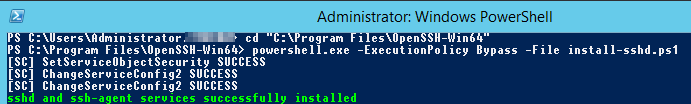
powershell.exe -ExecutionPolicy Bypass -File install-sshd.ps1
# Creating needed Firewall Rule
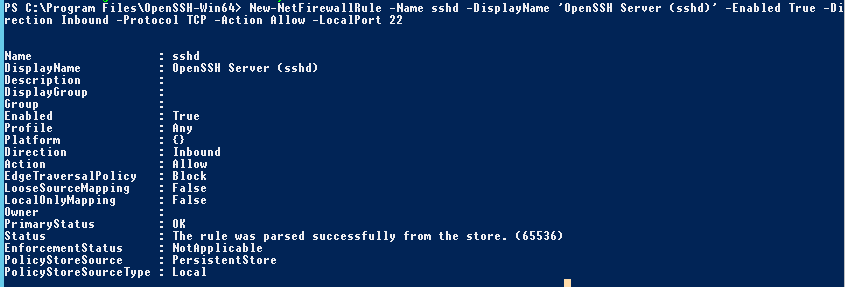
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
# Starting OpenSSH - Service
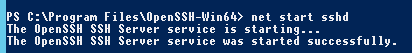
net start sshd
# Modifying Service-Startup Type
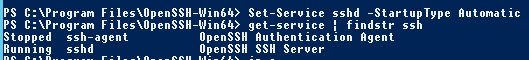
Set-Service sshd -StartupType Automatic
# Checking Service Status
get-service | findstr ssh
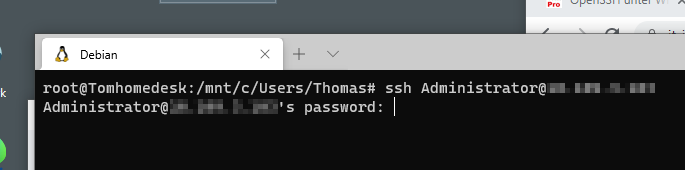
Access via password:
ssh Administrator@<ip or hostname>
ssh Administrator@<domain>@<ip or hostname>
Access via Cert:
On the clientside:
ssh-keygen
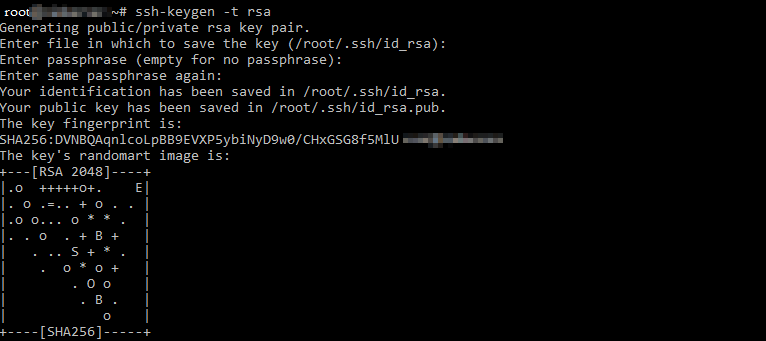
Ssh-keygen will create 2 files:
- ~/.ssh/id_rsa – a private key
- ~/.ssh/id_rsa.pub – a public key
On the serverside (Windows Server 2012 R2):
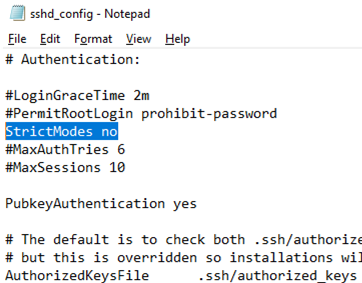
Edit "C:\ProgramData\ssh\sshd_config"
# Uncomment this line:
AuthorizedKeysFile __PROGRAMDATA__/ssh/administrators_authorized_keys
# Allow access Windows using RSA keys in the sshd_config file:
PubkeyAuthentication yes
# And disable ssh password login:
PasswordAuthentication no
Don’t forget to restart the sshd service after saving changes in sshd_config.
restart-service sshd
Copy the contents of the file (~/.ssh/id_rsa.pub) to clipboard.
Paste the key you copied into this file "C:\ProgramData\ssh\administrators_authorized_keys"
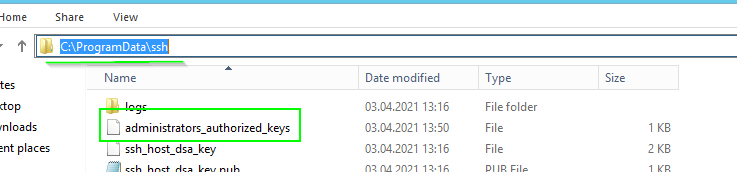
# Adjustment of the permissions for administrators_authorized_keys - file
$acl = Get-Acl C:\ProgramData\ssh\administrators_authorized_keys
$acl.SetAccessRuleProtection($true, $false)
$administratorsRule = New-Object system.security.accesscontrol.filesystemaccessrule("Administrators","FullControl","Allow")
$systemRule = New-Object system.security.accesscontrol.filesystemaccessrule("SYSTEM","FullControl","Allow")
$acl.SetAccessRule($administratorsRule)
$acl.SetAccessRule($systemRule)
$acl | Set-Acl
# Set the proper Shell (PowerShell)
New-ItemProperty -Path "HKLM:\SOFTWARE\OpenSSH" -Name DefaultShell -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -PropertyType String -Force
Test & Result:
ssh -i ~/.ssh/id_rsa Administrator@10.109.3.103
ssh -i ~/.ssh/id_rsa Administrator@<domain>@<ip or hostname>
Deinstallation:
choco uninstall openssh -params "/SSHServerFeature /SSHAgentFeature" -y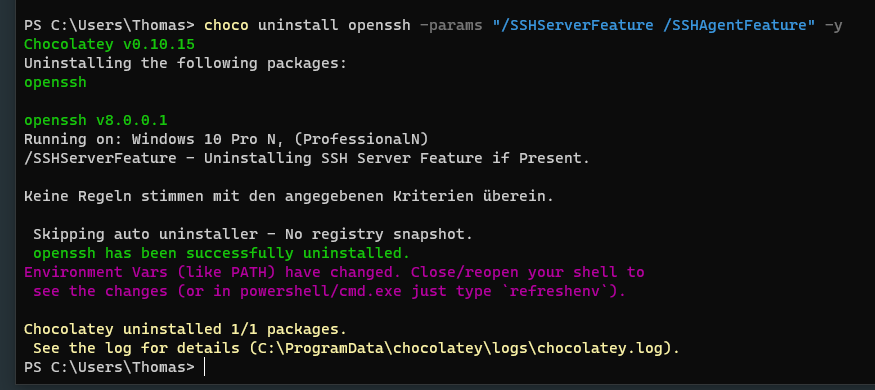
Sources:
PowerShell/Win32-OpenSSH
Win32 port of OpenSSH. Contribute to PowerShell/Win32-OpenSSH development by creating an account on GitHub.
https://www.concurrency.com/blog/may-2019/key-based-authentication-for-openssh-on-windows
Configuring SSH Key-Based Authentication on Windows 10/ Server 2019 | Windows OS Hub
In this article we will configure SSH authentication with RSA keys on Windows to securely access remote servers/computers. We’ll show how to generate RSA keys (certificates) on Windows and configure…
https://www.concurrency.com/blog/february-2019/getting-started-with-ssh-on-windows-server-2019
